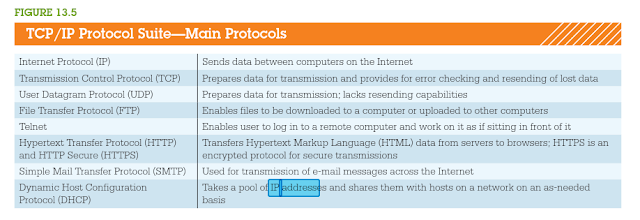
TCP/IP Protocol Suite - Main Protocols
 Reviewed by 0x000216
on
Monday, April 17, 2017
Rating: 5
Reviewed by 0x000216
on
Monday, April 17, 2017
Rating: 5
 Reviewed by 0x000216
on
Monday, April 17, 2017
Rating: 5
Reviewed by 0x000216
on
Monday, April 17, 2017
Rating: 5
SmartSniff - Capture TCP/IP packets on your network adapter
SmartSniff is a network monitoring utility that allows you to capture TCP/IP packets that pass through your network adapter, and view the captured data as sequence of conversations between clients and servers. You can view the TCP/IP conversations in Ascii mode (for text-based protocols, like HTTP, SMTP, POP3 and FTP.) or as hex dump. (for non-text base protocols, like DNS)
SmartSniff provides 3 methods for capturing TCP/IP packets :
- Raw Sockets (Only for Windows 2000/XP or greater): Allows you to capture TCP/IP packets on your network without installing a capture driver. This method has some limitations and problems.
- WinPcap Capture Driver: Allows you to capture TCP/IP packets on all Windows operating systems. (Windows 98/ME/NT/2000/XP/2003/Vista) In order to use it, you have to download and install WinPcap Capture Driver from this Web site. (WinPcap is a free open-source capture driver.)This method is generally the preferred way to capture TCP/IP packets with SmartSniff, and it works better than the Raw Sockets method.
- Microsoft Network Monitor Driver (Only for Windows 2000/XP/2003): Microsoft provides a free capture driver under Windows 2000/XP/2003 that can be used by SmartSniff, but this driver is not installed by default, and you have to manually install it, by using one of the following options:
- Option 1: Install it from the CD-ROM of Windows 2000/XP according to the instructions in Microsoft Web site
- Option 2 (XP Only) : Download and install the Windows XP Service Pack 2 Support Tools. One of the tools in this package is netcap.exe. When you run this tool in the first time, the Network Monitor Driver will automatically be installed on your system.
- Microsoft Network Monitor Driver 3: Microsoft provides a new version of Microsoft Network Monitor driver (3.x) that is also supported under Windows 7/Vista/2008. Starting from version 1.60, SmartSniff can use this driver to capture the network traffic.The new version of Microsoft Network Monitor (3.x) is available to download from Microsoft Web site.Notice:If WinPcap is installed on your system, and you want to use the Microsoft Network Monitor Driver method, it's recommended to run SmartSniff with /NoCapDriver, because the Microsoft Network Monitor Driver may not work properly when WinPcap is loaded too.
SmartSniff - Capture TCP/IP packets on your network adapter
 Reviewed by 0x000216
on
Saturday, April 19, 2014
Rating: 5
Reviewed by 0x000216
on
Saturday, April 19, 2014
Rating: 5
 Reviewed by 0x000216
on
Saturday, April 19, 2014
Rating: 5
Reviewed by 0x000216
on
Saturday, April 19, 2014
Rating: 5
nbtscan - NETBIOS nameserver scanner
This is a command-line tool that scans for open NETBIOS nameservers on a local or remote TCP/IP network, and this is a first step in finding of open shares. It is based on the functionality of the standard Windows tool nbtstat, but it operates on a range of addresses instead of just one. I wrote this tool because the existing tools either didn't do what I wanted or ran only on the Windows platforms: mine runs on just about everything.
NETBIOS is commonly known as the Windows "Network Neighborhood" protocol, and (among other things), it provides a nameservice that listens on UDP port 137. When it receives a query on this port, it responds with a list of all services it offers. Windows ships with a standard tool nbtstatwhich queries a single IP address when given the -A parameter. When run against a machine on the local network (a development box), it shows:
C:\> nbtstat -A 192.168.1.99
NetBIOS Remote Machine Name Table
Name Type Status
---------------------------------------------
XPDEV <00> UNIQUE Registered
UNIXWIX <00> GROUP Registered
XPDEV <03> UNIQUE Registered
XPDEV <20> UNIQUE Registered
UNIXWIX <1E> GROUP Registered
MAC Address = 00-50-04-6D-50-37The numeric code (in hexadecimal) and the type serve to identify the service being offered, and (for instance) a UNIQUE code of <20> indicates that the machine is running the file-sharing service. Unfortunately, nbtstat only reports the codes, and it requires looking up the meanings elsewhere. The References section at the end of this document lists some resources to learn what all the codes mean.
Machines participating in NETBIOS listen on UDP port 137 for these queries and respond accordingly. Simple configurations might only have a few resource records (as above), but an NT server supporting a large enterprise could easily have more than a dozen. Though it's sometimes useful to examine the full set of resource records for a given machine, in practice it's more useful to summarize them into the key "interesting" services.
Our tool has taken this approach. Not only does it scan ranges of addresses -- instead of just one machine -- but it can fully decode most of the resource record types and can summarize the interesting data on a one-line display.
On our network we have quite a few machines, but it appears that only three respond to our queries:
C:\> nbtscan 192.168.1.0/24
192.168.1.3 MTNDEW\WINDEV SHARING DC
192.168.1.5 MTNDEW\TESTING
192.168.1.9 MTNDEW\WIZ SHARING U=STEVE
192.168.1.99 MTNDEW\XPDEV SHARING
nbtscan - NETBIOS nameserver scanner
 Reviewed by 0x000216
on
Monday, March 31, 2014
Rating: 5
Reviewed by 0x000216
on
Monday, March 31, 2014
Rating: 5
 Reviewed by 0x000216
on
Monday, March 31, 2014
Rating: 5
Reviewed by 0x000216
on
Monday, March 31, 2014
Rating: 5