Telehash
![Telehash]() Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
How Coffee Fueled the Civil War
![How Coffee Fueled the Civil War]() Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
Submittable (YC S12) .NET Developer with Localization Experience
![Submittable (YC S12) .NET Developer with Localization Experience]() Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
Remove/ Get Rid of Istart123.com Quickly and Completely
![Remove/ Get Rid of Istart123.com Quickly and Completely]() Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
openSSH Configuration Tutorial - Kali Linux
Secure Shell (SSH) is a cryptographic network protocol for secure data communication, remote command-line login, remote command execution, and other secure network services between two networked computers. It connects, via a secure channel over an insecure network, a server and a client running SSH server and SSH client programs, respectively. The protocol specification distinguishes between two major versions that are referred to as SSH-1 and SSH-2.
The best-known application of the protocol is for access to shell accounts on Unix-like operating systems, but it can also be used in a similar fashion for accounts on Windows. It was designed as a replacement for Telnet and other insecure remote shell protocols such as the Berkeley rsh and rexec protocols, which send information, notably passwords, in plaintext, rendering them susceptible to interception and disclosure using packet analysis.The encryption used by SSH is intended to provide confidentiality and integrity of data over an unsecured network, such as the Internet.
You can use your Android phone, remote computer, iPAD or anything to login to a SSH server and execute command as if you’re sitting on that workstation. So let’s see how you can install a SSH server (we will be using openSSH-Server here) on Kali Linux. After this guide you will be able to do the followings:
So we will ensure that SSH server remains up and running all the time (even after restart). Please note that if you don’t want this to happen, then skip Step 2 and move to Step 3. Why? Because if you enable SSH server on your machine, that means your machine will be available via internet and anyone who knows your password (or your password is just ’123′ or ‘password’ can break into your machine). So use a secured password and if not sure skip to Step 3 for now. Anyway, moving on..
First of all remove run levels for SSH.
If you don’t have
Restart SSH.
Now the usual SSH
Well, that’s just plain and boring for me.
Go to http://patorjk.com/software/taag/
Type something in “

Edit the following file and add your text.

So next time I try to login I get this nice screen with some more info

Pretty cool!

Usually this is the sign of something bad. As you can see
This is a rather easy fix. You just need to delete the offending line in

Just delete the line, save the file and try to SSH again.

and it worked.
Make a backup of existing SSH config file.
The standard TCP port 22 has been assigned for contacting SSH servers. If you scan for this port using NMAP, you will see many servers has it open to the world and you can try to bruteforce it and gain access.
An SSH client program is typically used for establishing connections to an SSH daemon accepting remote connections. Both are commonly present on most modern operating systems, including Mac OS X, most distributions of GNU/Linux, OpenBSD, FreeBSD, NetBSD, Solaris and OpenVMS. Notably, Windows is one of the few modern desktop/server OSs that does not include SSH by default. Some common SSH clients includes
Both WinSCP and PuTTY are available packaged to run directly off of a USB drive, without requiring installation on the client machine. Setting up a SSH server in Windows typically involves installation (e.g. via installing Cygwin, or by installing a stripped down version of Cygwin with the SSH server.
SSH is important in cloud computing to solve connectivity problems, avoiding the security issues of exposing a cloud-based virtual machine directly on the Internet. An SSH tunnel can provide a secure path over the Internet, through a firewall to a virtual machine.
Source with thanks to blackmoreops.com
The best-known application of the protocol is for access to shell accounts on Unix-like operating systems, but it can also be used in a similar fashion for accounts on Windows. It was designed as a replacement for Telnet and other insecure remote shell protocols such as the Berkeley rsh and rexec protocols, which send information, notably passwords, in plaintext, rendering them susceptible to interception and disclosure using packet analysis.The encryption used by SSH is intended to provide confidentiality and integrity of data over an unsecured network, such as the Internet.
You can use your Android phone, remote computer, iPAD or anything to login to a SSH server and execute command as if you’re sitting on that workstation. So let’s see how you can install a SSH server (we will be using openSSH-Server here) on Kali Linux. After this guide you will be able to do the followings:
- Install Kali Linux remote SSH – openSSH server
- Enable Kali Linux remote SSH service on boot
- Change Kali default ssh keys to avoid MITM attack
- Set MOTD – Message of the Day message with a nice ASCII
- Troubleshoot and fix “
WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED” error during SSH session. - Change SSH server port for extra safety
Step 1: Install Kali Linux remote SSH – openSSH server
Issue the following command on Kali Linux terminal to installopenssh-server.root@kali~:# apt-get install openssh-server
Now the next logical step is to enable ssh server (as you can see I’ve issued the following command above).
root@kali~:# service ssh startSo we will ensure that SSH server remains up and running all the time (even after restart). Please note that if you don’t want this to happen, then skip Step 2 and move to Step 3. Why? Because if you enable SSH server on your machine, that means your machine will be available via internet and anyone who knows your password (or your password is just ’123′ or ‘password’ can break into your machine). So use a secured password and if not sure skip to Step 3 for now. Anyway, moving on..
Step 2: Enable Kali Linux remote SSH service
Now we are about to enable SSH service and keep that running the whole time. (changes wont get lost after boot).First of all remove run levels for SSH.
root@kali~:# update-rc.d -f ssh remove
Next load SSH defaults to run level
root@kali~:# update-rc.d -f ssh defaults
Check if SSH service is up and running
root@kali~:# chkconfig ssh
If you don’t have
chkconfig installed, install viaroot@kali~:# apt-get install chkconfigYou can run
chkconfig to see a lot more too:root@kali~:# chkconfig -l ssh
(or)
root@kali~:# chkconfig -l
Step 3: Change Kali default ssh keys to avoid MITM attack
At this point you will haveopenssh-server installed on Kali Linux and enabled at runlevel 2,3,4 and 5. But now we got a problem. Every Linux system that you install via a CD or DVD or similar uses a default SSH key. This is same for all first installation that means, anyone with a similar version can perform a Man in the Middle Attack (MITM) and listen to your encrypted traffic. To fix that we will do the followings:Step 3.1: Move the default Kali ssh keys to a new folder:
Issue the following commands one line at a time:root@kali:~# cd /etc/ssh/This will move your default keys to the new folder.
root@kali:/etc/ssh# mkdir default_kali_keys
root@kali:/etc/ssh#
root@kali:/etc/ssh# mv ssh_host_* default_kali_keys/
root@kali:/etc/ssh#
Step 3.2: Regenerate the keys
Use the following command to regenerateSSH keysroot@kali:/etc/ssh# dpkg-reconfigure openssh-server
Creating SSH2 RSA key; this may take some time ...
Creating SSH2 DSA key; this may take some time ...
Creating SSH2 ECDSA key; this may take some time ...
[ ok ] Restarting OpenBSD Secure Shell server: sshd.
root@kali:/etc/ssh#
Step 3.3: Verify ssh key hashes are different
Use the following commands to verify SSH key hashes are differentroot@kali:/etc/ssh# md5sum ssh_host_*Compare new key hashes to the hashes below)
d5dff2404dd43ee0d9ed967f917fb697 ssh_host_dsa_key
2ec88dc08f24c39077c47106aab1e7f4 ssh_host_dsa_key.pub
ab96da6ffc39267f06e7f9497c4f5755 ssh_host_ecdsa_key
614e36d18dc2c46178d19661db4dbd7b ssh_host_ecdsa_key.pub
abcc037705e48b3da91a2300d42e6a2b ssh_host_rsa_key
e26eaa1c5cff38457daef839937fcedd ssh_host_rsa_key.pub
root@kali:/etc/ssh#
root@kali:/etc/ssh# cd default_kali_keys/
root@kali:/etc/ssh#
root@kali:/etc/ssh/default_kali_keys# md5sum *
9a09f49be320e561dc6cf95463d4378c ssh_host_dsa_key
1a52709d596569224822e870239c9298 ssh_host_dsa_key.pub
65d0af7fdc5c50f67f90cb953460ba61 ssh_host_ecdsa_key
606d1ac71100c8b38e0f87951bb94855 ssh_host_ecdsa_key.pub
c871ecf961924389f2cddbd5888b5037 ssh_host_rsa_key
99d4c4c68224900d0430f0bee9baf28e ssh_host_rsa_key.pub
root@kali:/etc/ssh/default_kali_keys#
Restart SSH.
root@kali:/etc/ssh/default_kali_keys# service ssh restart
Step 4: Set MOTD with a nice ASCII
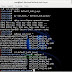
So far, we have installed and configured Kali Linux remote SSH – openssh-server, enabled openssh-server to run on boot, changed Kali default SSH keys to avoid MITM attacks.Now the usual SSH
MOTD (Message of the Day – Banner) is boring. I want my name on that and add some useful info. Following is what a usual MOTD looks like:Well, that’s just plain and boring for me.
Go to http://patorjk.com/software/taag/
Type something in “
Type Something” Box! Play around with the settings and you get a nice ASCII art.Edit the following file and add your text.
root@kali:~# vi /etc/motdSave the file and restart/reload SSH … both should just work. I’ve added
root@kali:~#service ssh restart
blackMORE Ops as ASCII and http://www.blackmoreops.com/ as a second line…So next time I try to login I get this nice screen with some more info
Pretty cool!
Step 5: Troubleshooting
Because I changed SSH keys in the middle of change, (I was logged in before), I had this BIG warning message coming up@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY!
Someone could be eavesdropping on you right now (man-in-the-middle attack)!
It is also possible that the RSA host key has just been changed.
The fingerprint for the RSA key sent by the remote host is
26:65:52:75:81:71:a8:c5:4c:ad:b6:81:78:58:18:af.
Please contact your system administrator.
Add correct host key in /root/.ssh/known_hosts to get rid of this message.
Offending key in /root/.ssh/known_hosts:1
RSA host key for localhost has changed and you have requested strict checking.
Host key verification failed.
It kicked me right out.Usually this is the sign of something bad. As you can see
MITM attacks does this:IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY!
Someone could be eavesdropping on you right now (man-in-the-middle attack)!
This was the reason I changed Kali Linux default key (You wouldn’t even notice MITM if you’re using the default key).This is a rather easy fix. You just need to delete the offending line in
known_hosts file.Add correct host key in /root/.ssh/known_hosts to get rid of this message.
Offending key in /root/.ssh/known_hosts:1
Use the following command:root@kali:~# vi /root/.ssh/known_hostsFollowing was the key I had
Just delete the line, save the file and try to SSH again.
and it worked.
Step 6: Change SSH server port for extra safety
As a last step and just to be sure, you should also change SSHport from 22 to something else. (any port between 10000-64000 is okay)Make a backup of existing SSH config file.
root@kali:/etc/ssh# cp /etc/ssh/sshd_config /etc/ssh/sshd_config_backupEdit the SSH_Config file.root@kali:/etc/ssh# vi /etc/ssh/sshd_configLook for the following line:
#Port 22Change the line so it looks like this:
Port 10101Restart
OpenSSH serverroot@kali:/etc/ssh# service ssh restartNext time you SSH, you use the following command:root@kali:~# ssh username@myhostnaname.com -p 10101Where
- username@myhostnaname.com = Username and Hostname where hostname can be an IP or FQDN.
- -p = Port
- 10101 = Destination Port
Conclusion:
SSH is typically used to log into a remote machine and execute commands, but it also supports tunneling, forwarding TCP ports and X11 connections; it can transfer files using the associated SSH file transfer (SFTP) or secure copy (SCP) protocols. SSH uses the client-server model.The standard TCP port 22 has been assigned for contacting SSH servers. If you scan for this port using NMAP, you will see many servers has it open to the world and you can try to bruteforce it and gain access.
An SSH client program is typically used for establishing connections to an SSH daemon accepting remote connections. Both are commonly present on most modern operating systems, including Mac OS X, most distributions of GNU/Linux, OpenBSD, FreeBSD, NetBSD, Solaris and OpenVMS. Notably, Windows is one of the few modern desktop/server OSs that does not include SSH by default. Some common SSH clients includes
- PuTTY
- Cygwin
- WinSCP
Both WinSCP and PuTTY are available packaged to run directly off of a USB drive, without requiring installation on the client machine. Setting up a SSH server in Windows typically involves installation (e.g. via installing Cygwin, or by installing a stripped down version of Cygwin with the SSH server.
SSH is important in cloud computing to solve connectivity problems, avoiding the security issues of exposing a cloud-based virtual machine directly on the Internet. An SSH tunnel can provide a secure path over the Internet, through a firewall to a virtual machine.
Source with thanks to blackmoreops.com
openSSH Configuration Tutorial - Kali Linux
 Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
 Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
tutorial - Convert man pages to text
![tutorial - Convert man pages to text]() Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
tutorial - Block messengers through Iptables
![tutorial - Block messengers through Iptables]() Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
Friday fantasies
Don't forget to check out the IPKat's Forthcoming Events page, here. Several fresh items have been added this week, just for some of you ...
... and talking of which, if you happen to be in the lovely old city of Edinburgh on Tuesday, 12 August, be sure to venture down to The Pommery Champagne Café Bar, which you'll find in the Signet Library. Between the thoroughly civilised hours for sipping Champagne, ie 3.00 pm – 5.00 pm, fellow Kat Eleonora Rosati will be in conversation with illustrious Scottish IP litigator and Katfriend Gill Grassie (partner, Brodies LLP). This event has been created in order to rally that fierce and independent clan of Scottish IP lawyers to hear about the latest international copyright developments. 1.5 Law Society of Scotland CPD hours are on offer, and the modest registration fee includes at least one glass of bubbly. Further details and registration here.
 Tattoo, Kats too. The IPKat received, at very short notice, an urgent request for legal input from a journalist, Ross McGuinness, who was compiling an article for popular give-away morning newspaper Metro. Ross was working on a piece, "Ink twice: Do celebrities and footballers own their tattoos? Does anyone?" While this Kat was unable to drop his deadline-directed work, he was thrilled that his feline friend Eleonora Rosati, plus former guest Kats Miri Frankel, Darren Meale and Robert Cumming, not to mention emeritus Kat Jo Gibson, were able to rally round Ross and be of some assistance. Ross's article is here. For the record, it seems -- perhaps unsurprisingly -- that IP lawyers see bigger issues relating to copyright in tattoos than do tattoo artists and their clients ...
Tattoo, Kats too. The IPKat received, at very short notice, an urgent request for legal input from a journalist, Ross McGuinness, who was compiling an article for popular give-away morning newspaper Metro. Ross was working on a piece, "Ink twice: Do celebrities and footballers own their tattoos? Does anyone?" While this Kat was unable to drop his deadline-directed work, he was thrilled that his feline friend Eleonora Rosati, plus former guest Kats Miri Frankel, Darren Meale and Robert Cumming, not to mention emeritus Kat Jo Gibson, were able to rally round Ross and be of some assistance. Ross's article is here. For the record, it seems -- perhaps unsurprisingly -- that IP lawyers see bigger issues relating to copyright in tattoos than do tattoo artists and their clients ...
The Old Nick. At least a few Kats, fellow IP bloggers and enthusiasts will be meeting up for a pleasurable pint of Badger at The Old Nick (Holborn, Central London, here) this coming Wednesday, 16 July. Previous occasional meetings in this venerable venue have resulted in some jolly good discussions of topics of contemporary intellectual property law and practice, as well as some serious topics. IPKat blogmeister Jeremy will be there between 5 pm and 7 pm, and there will be others ... Please feel free to join us if you're around. No need to RSVP. We're usually round the back if it's free. If not, we're pretty easy to find.
Around the weblogs. Ben Challis has been busy again on the 1709 Blog, with his latest CopyKat post. Over on Class 46, fellow Kat Birgit spots that the UK is not about to reintroduce fast-track examination of trade mark applications for the unsurprising reason that there wasn't any demand for them in the first place, while Denise Verdoold sniffs the subtle scent of a cheese war maturing between Europe and the United States of America, the battleground being whether geographical cheese names are protectable assets or generic terms. While on the subject of protection of place-related food names, here's Nicola Coppola's current intelligence note for the jiplp blog on the 'Salame Felino' case. PatLit picks up on the SDL litigation and the counterfactual reconstruction of a non-existent past in order to assess real damages for making wrongful threats to sue a trading business for patent infringement. Finally, crossing to the US of A, one of this Kat's heroes, Marty Schwimmer, Anti-scam Warrior and Redskins Worrier, updates us -- with a little help from Rebecca Tushnet's 43(B)log -- on his efforts to pin down Patent & Trademark Agency LLC for false advertising and creating the erroneous impression that people have to pay it money ...
Back on 14 January the IPKat hosted a guest post by Barbara Cookson, "Problems with the OHIM database: prioritising the solutions", here. At the time we received some comments as well as a fair bit of email on the subject, and the position regarding the Office for Harmonisation in the Internal Market's not-so-new website does seem to have improved considerably, thanks to some very helpful input from users of the Community trade mark system as well as a willingness to listen and react on the part of OHIM. All is not yet perfect, however, and an anonymous correspondent posted the following paragraph to the 14 January article. Since few people are likely to see it there now, this Kat has taken the opportunity to paste it here:
Stairway to Heaven? No, Highway to Registration. There's a Patent Prosecution Highway User Seminar coming up soon, on Tuesday, 22 July from 9:30 to 16:30, thanks to the German Patent and Trade Mark Office Munich. Details are available here. Given the number of hours that the seminar is to last, says Merpel, you can be sure that it will cover the subject thoroughly.
 |
| Feeling a bit Pommery? |
 Tattoo, Kats too. The IPKat received, at very short notice, an urgent request for legal input from a journalist, Ross McGuinness, who was compiling an article for popular give-away morning newspaper Metro. Ross was working on a piece, "Ink twice: Do celebrities and footballers own their tattoos? Does anyone?" While this Kat was unable to drop his deadline-directed work, he was thrilled that his feline friend Eleonora Rosati, plus former guest Kats Miri Frankel, Darren Meale and Robert Cumming, not to mention emeritus Kat Jo Gibson, were able to rally round Ross and be of some assistance. Ross's article is here. For the record, it seems -- perhaps unsurprisingly -- that IP lawyers see bigger issues relating to copyright in tattoos than do tattoo artists and their clients ...
Tattoo, Kats too. The IPKat received, at very short notice, an urgent request for legal input from a journalist, Ross McGuinness, who was compiling an article for popular give-away morning newspaper Metro. Ross was working on a piece, "Ink twice: Do celebrities and footballers own their tattoos? Does anyone?" While this Kat was unable to drop his deadline-directed work, he was thrilled that his feline friend Eleonora Rosati, plus former guest Kats Miri Frankel, Darren Meale and Robert Cumming, not to mention emeritus Kat Jo Gibson, were able to rally round Ross and be of some assistance. Ross's article is here. For the record, it seems -- perhaps unsurprisingly -- that IP lawyers see bigger issues relating to copyright in tattoos than do tattoo artists and their clients ...The Old Nick. At least a few Kats, fellow IP bloggers and enthusiasts will be meeting up for a pleasurable pint of Badger at The Old Nick (Holborn, Central London, here) this coming Wednesday, 16 July. Previous occasional meetings in this venerable venue have resulted in some jolly good discussions of topics of contemporary intellectual property law and practice, as well as some serious topics. IPKat blogmeister Jeremy will be there between 5 pm and 7 pm, and there will be others ... Please feel free to join us if you're around. No need to RSVP. We're usually round the back if it's free. If not, we're pretty easy to find.
 |
| With a possible cheese war on the way, Marmaduke is taking no chances ... |
 |
| Misplaced anger: the problem's the software ... |
"We sent in February some documents to OHIM through e-communication but it seems that because of their new website the documents did not reach the Office. Now OHIM does not accept that there was a problem with their new website and states that we did not send the documents. Is anyone having the same problem? This is totally wrong, we have proof that the documents were sent, but still OHIM does not accept it".Readers, can you help? OHIM, can you help? Let's hear from you!
Stairway to Heaven? No, Highway to Registration. There's a Patent Prosecution Highway User Seminar coming up soon, on Tuesday, 22 July from 9:30 to 16:30, thanks to the German Patent and Trade Mark Office Munich. Details are available here. Given the number of hours that the seminar is to last, says Merpel, you can be sure that it will cover the subject thoroughly.
Friday fantasies
 Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
 Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
Patent value: but how do we understand the market?
 Last week this Kat published a blogpost entitled “Have U.S. courts made patents less valuable?", here, which discussed aspects of the article by Terry Ludow, “Signs of the times: trends in technology IP licensing”. This article had been published in Intellectual Asset Management (IAM) magazine. The blog post engendered a lively discussion among Kat readers. In addition, it drew the attention of Katfriend Joff Wild, the editor of IAM, who published a long and thoughtful response to the post on the IAM website, here. Joff’s comments are worthy of attention to Kat readers. Accordingly, this Kat takes the opportunity to summarize Joff’s observations.
Last week this Kat published a blogpost entitled “Have U.S. courts made patents less valuable?", here, which discussed aspects of the article by Terry Ludow, “Signs of the times: trends in technology IP licensing”. This article had been published in Intellectual Asset Management (IAM) magazine. The blog post engendered a lively discussion among Kat readers. In addition, it drew the attention of Katfriend Joff Wild, the editor of IAM, who published a long and thoughtful response to the post on the IAM website, here. Joff’s comments are worthy of attention to Kat readers. Accordingly, this Kat takes the opportunity to summarize Joff’s observations.Joff accepts the assertion that monetization is not the sole reason that patent owners build patent portfolios. However, he takes the position that whether or not monetization is the primary mover for patenting,
“the price of a patent is ultimately a reflection of its overall value, not just its monetization potential. Although there are always exceptions, the ones that will generally generate the most money were they to be put up for sale are the ones that are of high quality and which read on key technologies that underpin products want to buy.”Joff then goes on to make a series of more specific points about patent value:
1. U.S. patent values have fallen in recent years, presumably for many of the reasons that Ludlow argued in his article.Joff has raised some compelling points. However, in the view of this Kat, there is the unaddressed elephant in the room—the market for patents by which patent values are presumably set. But what exactly are the contours and structure of this market and how has it operated over time? Is it more akin the fine art market in the sense that no two assets are alike, it is subject to changes in tastes and it is dominated by a relatively small number of high rollers? Or is this market sui generis ex extremis?
2. On the other hand, we may be at the cusp of increasing patent values in Europe (and perhaps later down the line in China) The key is high-quality patents, more predictable court rulings and better enforceability.
3. While patent valuations will not return to the levels of a couple of years ago (e.g., Nortel’s auction generated $4.5 billion and Google paid $12.5 billion for Motorola Mobility) we will witness higher valuations for patents across a wider range of industries, including automotive, energy financial services and medical services. Previously, the highest valuations tended to focus on telecoms-related industries.
4. The current situation in the U.S., where it is harder to enforce patents, “is bound to play itself out. At that state a level of certainty will return to the market which will have an upward effect on prices.”
5. More than ever, quality is what will ultimately count regarding patent values. With higher quality patents, higher patent values as a function of litigation opportunities will spread to Europe and perhaps to China down the road.
The oversized amounts paid especially in 2011 and 2012 were, in this Kat’s understanding, due to an idiosyncratic confluence of factors, including large patent portfolios being flogged as a result of bankruptcy or like financial difficulties by the patent owners. The story still needs to be written about how these valuations came about, including what was the role of investment bankers and the criteria used by those who offered valuations for the portfolios. This Kat suspects that developments in the patent case law in the US had little impact on what happened to patent values in 2011 and 2012, but he would be delighted if Kat readers could point him to research to the contrary. If this Kat is correct, however, it becomes more difficult to explain why case law developments are, contrary to the 2011-2012 period, now taking on substantially greater importance in depressing patent values.
This Kat cannot stop thinking about two anecdotes in connection with patent values.
A well-known figure in the area in Silicon Valley recounted how, in the 1970s, patent negotiations were often conducted on the basis of which side could physically place on the table the larger bundle of patents. Mere bulk mattered and, to his view, it does so as well today. What has been happening in recent years is redolent of those earlier times.
Ah, you might say, with patents of greater quality, a better job can be made in better evaluating patents. Maybe yes, maybe no. A lawyer who was involved in one of the big mega-patent transactions of several years ago admitted to me that it was impossible to review even a fraction of the patents that were being offered for sale. What one tries to do is identify and evaluate the key patents. But key patents need not necessarily mean patents of higher quality (whatever exactly that means).
What these anecdotes say about the nature of the patent market is way beyond this Kat’s pay grade. At the least, however, they underscore that the most urgent need is for those involved in the “patent as a valuable asset” industry to provide a clearer explanation of this market and how it goes about setting the price and ultimately the value of patents.
Patent value: but how do we understand the market?
 Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
 Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5
Reviewed by 0x000216
on
Friday, July 11, 2014
Rating: 5




