Timeline Analysis, pt V - First Steps
In order to really understand developing a timeline of activity on a system, a great place to start is with the file system. Well...okay...not great, per se...it's the traditional way, how's that? So, let's get some hands-on experience, and to do that, let's start with an image...pick one from the Available Images section below; I'm going to use the NIST "hacking" case image because it has some interesting things we'll take a look at. You may have to download the segments of the raw, dd-format image and reassemble them into a single image file using the "type" command, or download the .E0x file and recapture the image into a raw format using FTK Imager.
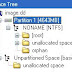
 Once you've downloaded the image, you can use FTK Imager to load the file and check out the partition table, or you can use the VDK file system driver (see the Resources section below) to view the partition table from the command line. Using the "vdk view" command, you can see the partition table, which gives us similar information (along with offsets) as what is available through FTK Imager:
Once you've downloaded the image, you can use FTK Imager to load the file and check out the partition table, or you can use the VDK file system driver (see the Resources section below) to view the partition table from the command line. Using the "vdk view" command, you can see the partition table, which gives us similar information (along with offsets) as what is available through FTK Imager:
Disk Capacity : 9514260 sectors (4645 MB)
Number Of Files : 1
Type Size Path
------- ------- ----
FLAT 9514260 d:\hacking\image.dd
Partitions :
# Start Sector Length in sectors Type
-- ------------ --------------------- ----
0 0 9514260 ( 4645 MB)
1 63 9510417 ( 4643 MB) 07h:HPFS/NTFS
Another tool you can use to collect similar information from an image is TSK's mmls tool. Using the command "mmls -t dos d:\hacking\image.dd", we see the following output:
DOS Partition Table
Offset Sector: 0
Units are in 512-byte sectors
Slot Start End Length Description
00: Meta 0000000000 0000000000 0000000001 Primary Table (#0)
01: ----- 0000000000 0000000062 0000000063 Unallocated
02: 00:00 0000000063 0009510479 0009510417 NTFS (0x07)
03: ----- 0009510480 0009514259 0000003780 Unallocated
In the output of both "vdk view" and "mmls", I've bolded the particular information that we're looking for, the offset to the partition that we're interested in.
This is why I chose this image in particular; it provides us with a good example to use in order to demonstrate the use of the tools, as the NTFS partition doesn't at the first sector; rather, it starts at sector 63 (Note: you can get this same information by selecting the partition in FTK Imager and choosing View -> Properties). One of the tools that we'll want to use to obtain timeline information from our acquired image is the TSK tool 'fls' (see the link in the Resource section below). The 'fls' tool will allow you to extract timeline information for the file system from the acquired image. In order to create a bodyfile containing all of the timeline information, use the following command:
fls -r -p -o 63 -l -m C:/ d:\hacking\image.dd > bodyfile
Another great use for the tool is to get just a listing of all of the deleted files from the system using the following command:
fls -d -r -p -l -o 63 -m C:/ d:\hacking\image.dd > deleted
I won't go into detail on the uses of all of the various switches, as you can find those by typing just "fls" at the command prompt, or by accessing the appropriate link in the Resources section below. The output bodyfile from our first command contains all of the deleted files, as well.
The bodyfile created by fls lists 4 timestamps in Unix epoch time format; atime, mtime, ctime, and crtime. In this case, the crtime is the creation time, and the ctime value is the metadata change time, which are derived from the $STANDARD_INFORMATION NTFS attribute (for the NTFS file system, of course).
At this point, we have a body file that we can use with mactime to create a timeline of file system activity. We can also use this body file as an input to Michael Cloppert's ex-tip in order to incorporate other data sources into our timeline.
Available Images
Lance's ForensicKB blog practicals
NIST "hacking" case
InfoSecShortTakes competition image
Resources
SleuthKit fls man page
SleutKit Wiki: BodyFile
SleuthKit Wiki: Timeline
Forensic Wiki: How to analyze partitions
VDK file system driver
ForensicWiki: NTFS
 Once you've downloaded the image, you can use FTK Imager to load the file and check out the partition table, or you can use the VDK file system driver (see the Resources section below) to view the partition table from the command line. Using the "vdk view" command, you can see the partition table, which gives us similar information (along with offsets) as what is available through FTK Imager:
Once you've downloaded the image, you can use FTK Imager to load the file and check out the partition table, or you can use the VDK file system driver (see the Resources section below) to view the partition table from the command line. Using the "vdk view" command, you can see the partition table, which gives us similar information (along with offsets) as what is available through FTK Imager:Disk Capacity : 9514260 sectors (4645 MB)
Number Of Files : 1
Type Size Path
------- ------- ----
FLAT 9514260 d:\hacking\image.dd
Partitions :
# Start Sector Length in sectors Type
-- ------------ --------------------- ----
0 0 9514260 ( 4645 MB)
1 63 9510417 ( 4643 MB) 07h:HPFS/NTFS
Another tool you can use to collect similar information from an image is TSK's mmls tool. Using the command "mmls -t dos d:\hacking\image.dd", we see the following output:
DOS Partition Table
Offset Sector: 0
Units are in 512-byte sectors
Slot Start End Length Description
00: Meta 0000000000 0000000000 0000000001 Primary Table (#0)
01: ----- 0000000000 0000000062 0000000063 Unallocated
02: 00:00 0000000063 0009510479 0009510417 NTFS (0x07)
03: ----- 0009510480 0009514259 0000003780 Unallocated
In the output of both "vdk view" and "mmls", I've bolded the particular information that we're looking for, the offset to the partition that we're interested in.
This is why I chose this image in particular; it provides us with a good example to use in order to demonstrate the use of the tools, as the NTFS partition doesn't at the first sector; rather, it starts at sector 63 (Note: you can get this same information by selecting the partition in FTK Imager and choosing View -> Properties). One of the tools that we'll want to use to obtain timeline information from our acquired image is the TSK tool 'fls' (see the link in the Resource section below). The 'fls' tool will allow you to extract timeline information for the file system from the acquired image. In order to create a bodyfile containing all of the timeline information, use the following command:
fls -r -p -o 63 -l -m C:/ d:\hacking\image.dd > bodyfile
Another great use for the tool is to get just a listing of all of the deleted files from the system using the following command:
fls -d -r -p -l -o 63 -m C:/ d:\hacking\image.dd > deleted
I won't go into detail on the uses of all of the various switches, as you can find those by typing just "fls" at the command prompt, or by accessing the appropriate link in the Resources section below. The output bodyfile from our first command contains all of the deleted files, as well.
The bodyfile created by fls lists 4 timestamps in Unix epoch time format; atime, mtime, ctime, and crtime. In this case, the crtime is the creation time, and the ctime value is the metadata change time, which are derived from the $STANDARD_INFORMATION NTFS attribute (for the NTFS file system, of course).
At this point, we have a body file that we can use with mactime to create a timeline of file system activity. We can also use this body file as an input to Michael Cloppert's ex-tip in order to incorporate other data sources into our timeline.
Available Images
Lance's ForensicKB blog practicals
NIST "hacking" case
InfoSecShortTakes competition image
Resources
SleuthKit fls man page
SleutKit Wiki: BodyFile
SleuthKit Wiki: Timeline
Forensic Wiki: How to analyze partitions
VDK file system driver
ForensicWiki: NTFS