wifite <= another wifi cracking tool
this tool is design for backtrack4 so if you using another linux distro you need to install aircrack-ng first
lets get started
set your interface to monitor mode
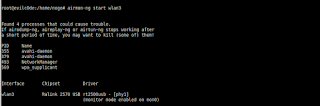
run wifite
# python wifite.py
wifite will automatically detect available access point and client also your interface
press CTRL+C when you ready to attack
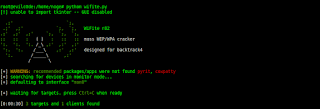
you will see all access point in your range
i just have 3 access point :(
now you can select which access point do you want to attack
if you want attack all access point in your range just type "all" and enter
in my case i will attack access point number 2 so i type "2" and enter
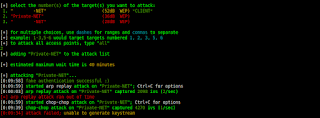
fake authentication successfull but my 2 attack not success :(
arp replay attack timeout and chop chop attack failed
wifite will automatically use another attack method like fragmentation attack
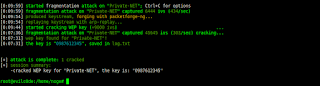
fragmentation attack require packetforge-ng to build keystream
if the capture packet is enough, wifite will automatically crack for a key
walla.. key found!! :))
now i can connect to access point
download wifite
download aircrack-ng
use this command to view help
# python wifite.py -h
./NoGe
lets get started
set your interface to monitor mode

run wifite
# python wifite.py
wifite will automatically detect available access point and client also your interface
press CTRL+C when you ready to attack

you will see all access point in your range
i just have 3 access point :(
now you can select which access point do you want to attack
if you want attack all access point in your range just type "all" and enter
in my case i will attack access point number 2 so i type "2" and enter

fake authentication successfull but my 2 attack not success :(
arp replay attack timeout and chop chop attack failed
wifite will automatically use another attack method like fragmentation attack

fragmentation attack require packetforge-ng to build keystream
if the capture packet is enough, wifite will automatically crack for a key
walla.. key found!! :))
now i can connect to access point

download wifite
download aircrack-ng
use this command to view help
# python wifite.py -h
./NoGe
