How to use ssldump in kali linux
Intro - ssldump is an SSL/TLS network protocol analyzer. It identifies TCP connections on the chosen network interface and attempts to interpret them as SSL/TLS traffic.When it identifies SSL/TLS traffic, it decodes the records and displays them in a textual form to stdout. If provided with the appropriate keying material, it will also decrypt the connections and display the application data traffic.
1. How to open
A. GUI Method
Application →Kali Linux → Information gathering → SSL Analysis → ssldump
(click on image for large view)
B. open terminal type ssldump –h this command will open ssldump with help option
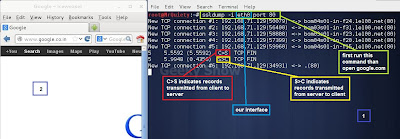
2. This command will show the traffic.
Syntax – ssldump –i interface port portno
Ex – ssldump –i eth0 port 80
3. This command display the application data traffic. This usually means decrypting it, but when -d is used ssldump will also decode application data traffic before the SSL session initiates. This allows you to see HTTPS CONNECT behavior as well as SMTP STARTTLS. As a side effect, since ssldump can't tell whether plaintext is traffic before the initiation of an SSL connection or just a regular TCP connection, this allows you to use ssldump to sniff any TCP connection.
ssldump will automatically detect ASCII data and display it directly to the screen.non-ASCII data is displayed as hex dumps.
4. Print absolute timestamps instead of relative timestamps.
5. The full SSL packet header. ssldump may print record-specific data on the rest of the line. For Handshake records, it prints the handshake message. Thus, this record is a Certificate message. ssldump chooses certain record types for further decoding. These are the ones that have proven to be most useful for debugging:
ClientHello - version, offered cipher suites, session id
ServerHello - version, session_id, chosen cipher suite, compression method
(click on image for large view)
Like it ? Share it.