DefCon CTF 2015 Quals WriteUp: BabyCmd and MathWhiz
Hey all! I got to play some of DefCon CTF 2015 Quals early on Friday evening, during which I was able to solve the BabyCmd challenge. First, they provided you with this binary, and also a service to connect to and pwn. The binary was a striped, 64bit ELF, that gave the user a limited command shell, consisting of these four commands:
and if you take too long:
After playing around I discovered a format string vulnerability, but this didn't seem to yield much:
Next I found I could escape the input and get command injection:
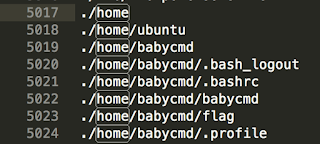
Which quickly led to being able to traverse the disk, and locate the flag (note, our commands couldn't include spaces or pipes):
And then read the flag:
This does the trick too, as you can tell from the output below:
Just some more quick CTF solutions :)
and if you take too long:
Next I found I could escape the input and get command injection:
Which quickly led to being able to traverse the disk, and locate the flag (note, our commands couldn't include spaces or pipes):
And then read the flag:
MathWhiz was another quick solve, this one came with no binary, just a socket connection where they throw a ton of math questions at you with various differences, such as brackets, braces, exponents, and the numbers written as words. You only have a few seconds to solve each question, and have to solve well over 500, so an automated solution is the way to go. I drafted up a quick python script, which you can find below:
This does the trick too, as you can tell from the output below:
Just some more quick CTF solutions :)