More Registry Fun
Once, on a blog far, far away, there was this post that discussed the use of the Unicode RLO control character to "hide" malware in the Registry, particularly from GUI viewers that processed Unicode.
Recently, Jamie shared this Symantec article with me; figure 1 in the article illustrates an interesting aspect of the malware when it comes to persistence...it apparently prepends a null character to the beginning of the value name. Interesting, some seem to think that this makes tools like RegEdit "brokken".
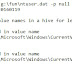
So, I wrote a RegRipper plugin called "null.pl" that runs through a hive file looking for key and value names that being with a null character. Jamie also shared a couple of sample hives, so I got to test the plugin out. The following image illustrates the plugin output when run against one of the hives:
All in all, the turn-around time was pretty quick. I started this morning, and had the plugin written, tested, and uploaded to Github before lunch.
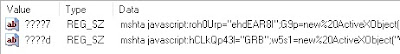
Later in the day, Eric Zimmerman followed up by testing the hive that Jamie graciously shared with me against the Registry Explorer. I should also note that MiTeC WRR has no issues with the value names; it displays them as follows:
Addendum, 20 Jan: On a whim, I ran the fileless.pl plugin against the hive, and it detected the two values with the "fileless" data seen in figure 2.
Recently, Jamie shared this Symantec article with me; figure 1 in the article illustrates an interesting aspect of the malware when it comes to persistence...it apparently prepends a null character to the beginning of the value name. Interesting, some seem to think that this makes tools like RegEdit "brokken".
So, I wrote a RegRipper plugin called "null.pl" that runs through a hive file looking for key and value names that being with a null character. Jamie also shared a couple of sample hives, so I got to test the plugin out. The following image illustrates the plugin output when run against one of the hives:
 |
| Figure 1 |
All in all, the turn-around time was pretty quick. I started this morning, and had the plugin written, tested, and uploaded to Github before lunch.
Later in the day, Eric Zimmerman followed up by testing the hive that Jamie graciously shared with me against the Registry Explorer. I should also note that MiTeC WRR has no issues with the value names; it displays them as follows:
 |
| Figure 2 |
Addendum, 20 Jan: On a whim, I ran the fileless.pl plugin against the hive, and it detected the two values with the "fileless" data seen in figure 2.