Cracking Unix Passwords Brute Force - Viper
Originally, the ufc-crypt implementation seemed to be the fastest crypt function around, using it made porting the program to different platforms easy.
Viper runs under Linux, Solaris, HPUX and DOS/Windows.
Usage
Viper v1.6 (Hale 05/12/2000) - C version by Frank4DD (05/05/2014)
Wiltered Fire - www.wilter.com/wf, incl. bugfixes by David C. Rankin
-f File to load password from (required unless using lsf)
-u Username to load from file (required unless using lsf)
-lsf Load saved file from previous session
-pf Save progress to file at update interval
-rf # Amount of time in hours to run for (default infinite)
-c # Character set from charset.ini to use (default 1)
-pws # Minimum password length (starting value, default 1)
-pwl # Maximum password length (default 8 - maximum 16)
-ui # Console update interval (in minutes - default 10)
-v Verbose output
Usage Example
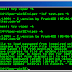
susie112:/home/me/viper-1.6/src # ./viper -f passwd -u root -ui 1 -v
Viper v1.6 (Hale 05/12/2000) - C version by Frank4DD (05/05/2014)
Wiltered Fire - www.wilter.com/wf, incl. bugfixes by David C. Rankin
Found: user root pw:reUJbHrFWYCQk
Found: Charset 0 in charset.ini
...command line parameters loaded.
Character set is 93 chars long
Starting crack on: Sun Oct 3 23:04:44 2009
Cracking for pass length 1 (93 possibilities)
Cracking for pass length 2 (8649 possibilities)
Cracking for pass length 3 (804357 possibilities)
Cracking for pass length 4 (7.48052e+07 possibilities)
[ Length: | Last: | CPS: | Time Spent: | Time Remaining: | Done: ]
-------------------------------------------------------------------------------
[ 4 | kq2r | 150000 | 000d:00h:01m:00s | 000d:00h:07m:18s | 12.03% ]
The password has been located.
Username : root
Password : test
Started : Sun Oct 3 23:04:44 2009
Finished : Sun Oct 3 23:06:30 2009
Duration : 000d:00h:01m:00s
Viper exiting...
Latest Updates
ºViper Version 1.5 has been updated to use the OpenSSL DES routines for encrypting. The UFC library has been dropped as outdated and even generating segfaults on some systems. There is a performance gain of approx. 25% coming from the OpenSSL libraries. In addition to the libraries, the OpenSSL headers (dev package) need to be installed in order to be able to compile Viper.
ºViper Version 1.6 received bugfixes thanks to David C. Rankin.
See also http://fm4dd.com/sw/viper/