Using Process Hacker to view non-signed processes
Process Hacker is an open-source process utility for Windows that is similar to the Sysinternals application Process Explorer. The utility can be found at:
http://processhacker.sourceforge.net/
To view the services “behind” a svchost.exe entry, hover the cursor over the entry and a small dialog box should appear.
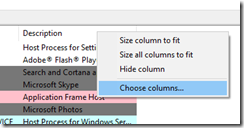
The majority of the time, malware is not digitally signed. To view non-signed processes, first add the two columns by right-clicking on an existing column under the Processes tab and selecting the “Choose columns” option.
Select “Verification status” and “Verified signer”, and add both to the active columns list.
To view only non-signed processes, use the menu option View –> Hide signed processes.
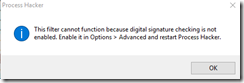
An error dialog box may appear:
Under Options –> Advanced, enable the selection for “Check images for digital signatures and packing”. A restart of the application will probably be required.
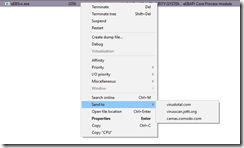
A process entry can be submitted to VirusTotal by using the right-click –> Send to –> virustotal.com option.