Tracing and Terminating a Reverse Connection Trojan | Lucideus Research
[Difficulty : Hard]
Introduction
Reverse Connection Trojan created by a RAT (Remote Administration Tool) gives an Attacker the authority to access a Victim Machine and get a complete remote access of it without any authentication and acts like a Administrator. So, that Trojan will look alike a cute from outside but is Malicious from inside. It can be any file, which contains some malicious code. That malicious code will give you the Reverse Connection of the Victim’s Machine to the attacker's machine. A Trojan can also be a FUD (Fully Undetectable) which will no be detected by any Anti-Malware, you can trace back and terminate the connection by these following steps.
Remote Administration Tools
A RAT or remote administration tool, is software that gives a person full control a tech device, remotely. The RAT gives the user access to your system, just as if they had physical access to your device. With this access, the person can access your files, use your camera, and even turn on/off your device. [1] The most famous RAT we are using to Create a Stub (a malicious Trojan) here is Dark Comet.
Lab Environment




Introduction
Reverse Connection Trojan created by a RAT (Remote Administration Tool) gives an Attacker the authority to access a Victim Machine and get a complete remote access of it without any authentication and acts like a Administrator. So, that Trojan will look alike a cute from outside but is Malicious from inside. It can be any file, which contains some malicious code. That malicious code will give you the Reverse Connection of the Victim’s Machine to the attacker's machine. A Trojan can also be a FUD (Fully Undetectable) which will no be detected by any Anti-Malware, you can trace back and terminate the connection by these following steps.
Remote Administration Tools
A RAT or remote administration tool, is software that gives a person full control a tech device, remotely. The RAT gives the user access to your system, just as if they had physical access to your device. With this access, the person can access your files, use your camera, and even turn on/off your device. [1] The most famous RAT we are using to Create a Stub (a malicious Trojan) here is Dark Comet.
Lab Environment
- Attacker’s Machine - Win 7x64 Ultimate , Dark Comet (RAT) , NO-IP DUC (Dynamic DNS Providing us Static IP)
- Victim’s Machine - Win7x64 Ultimate , Wireshark(A Network Packet Analysis Tool)
Workflow
The Trojan can be deployed in 2 ways :
- In a same particular Network (Attacker and Victim is in the same network)
- In different Networks (In which the Attacker is having a Static IP through DDNS in another network can connect to the Victim Machine of another network)
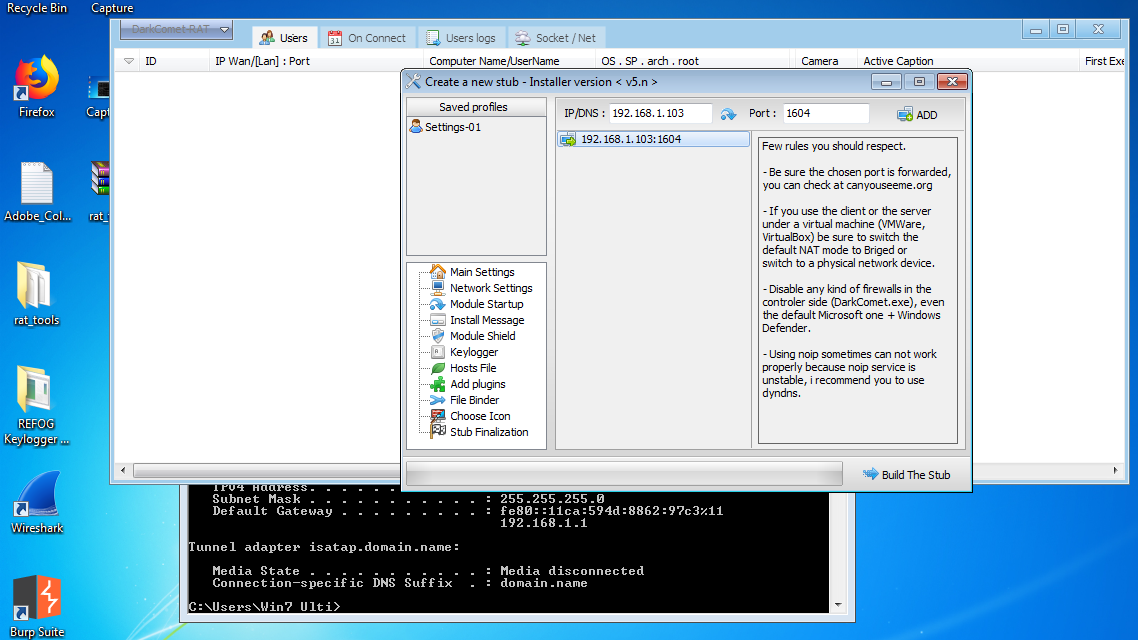
- Creating a Trojan through Dark Comet (whether in a same network or different individual networks).
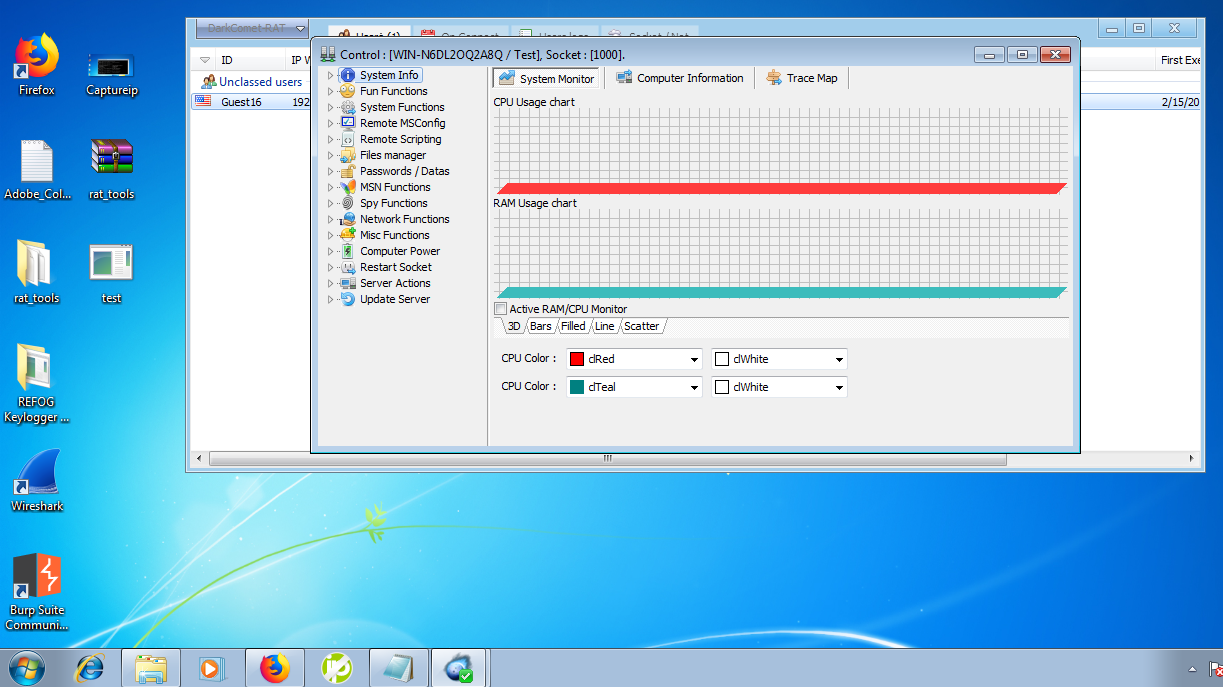
- Executing the Trojan in a Victim Machine.
- Tracing back the Trojan to its owner and Terminating the connection through there Sockets and Process IDs.
PoC
- Executing Trojan In the Same Network
- Creation of a Trojan through Dark Comet in the Attacker’s Machine.
- Executing the Trojan into the Victim’s Machine.
- Tracing and Terminating the Connection
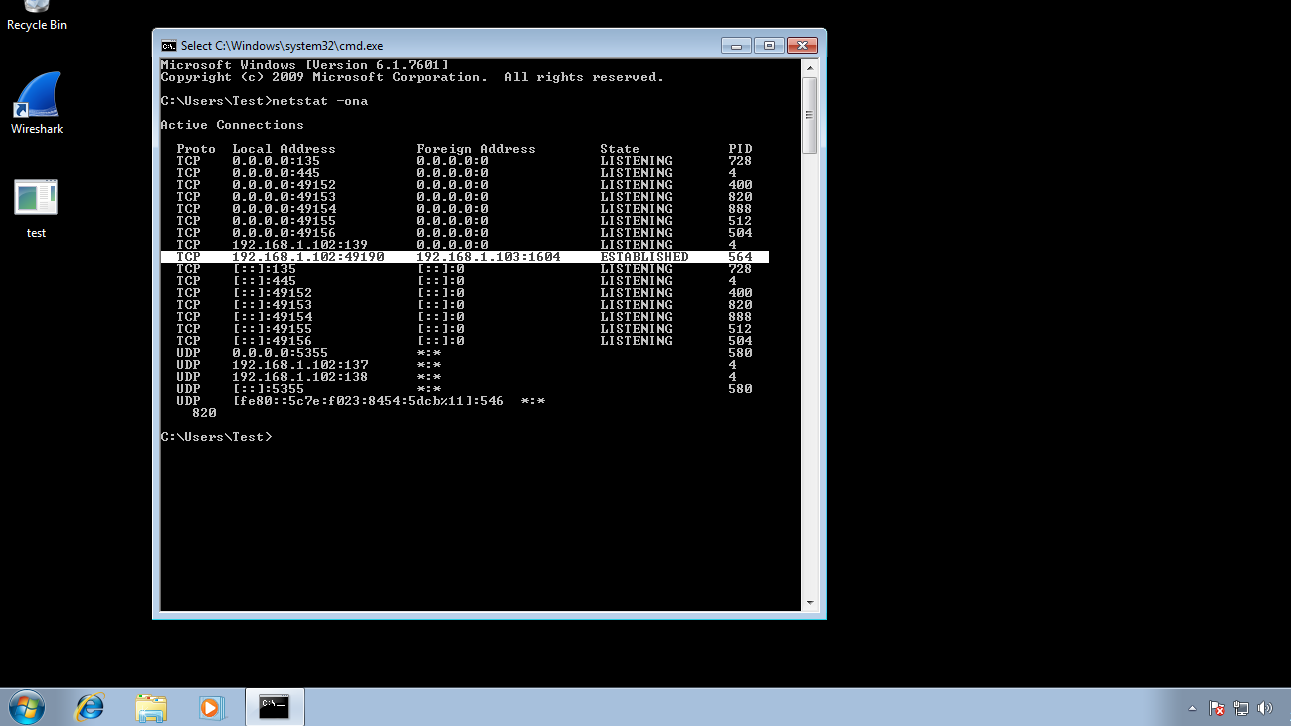
- CMD > $ netstat -ona (This will show all the Sockets : IP+Port Connections with their Stats of that particular machine)
This will show all connections established with a IP and Port Number with your Machine. So by this we get the IP of the Attacker which is in our Network only.
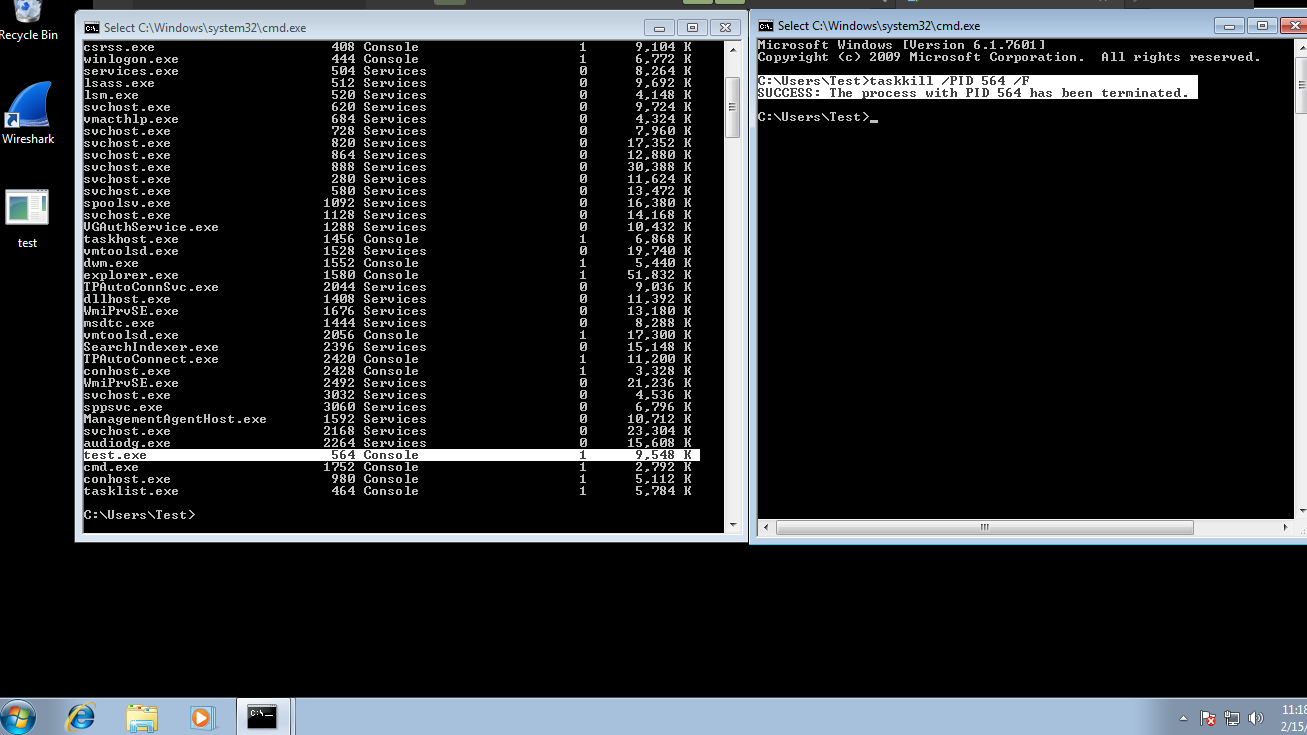
- CMD > $ tasklist (IT will show all the .exe running in your Machine and if you will get to know the name of the malicious exe with their PIDs)
- Killing PID (Process IDs) of those malicious exe
CMD > $ taskkill /PID ___ /F
- Task Manager < $ ctrl+alt+del
$ Processes > kill PID (Process ID) of the Malicious Executable(exe)
2. Executing Trojan in Different Networks (Through Host Dynamic DNS by NO-IP DUC)
- Installing Dynamic User Client of No-IP DDNS in Attacker’s Machine and get a Static IP by creating a Host DNS in that.
- Creating a Trojan by the Host DNS which we get from No-IP DUC.
- So here we will be using a Dynamic DNS Host instead of IP Address which will be providing some kind of partial anonymity to the Reverse Connection and after that we’ll Trace back those Reverse Connection DDNS.
- Executing the Trojan into the Victim’s Machine.
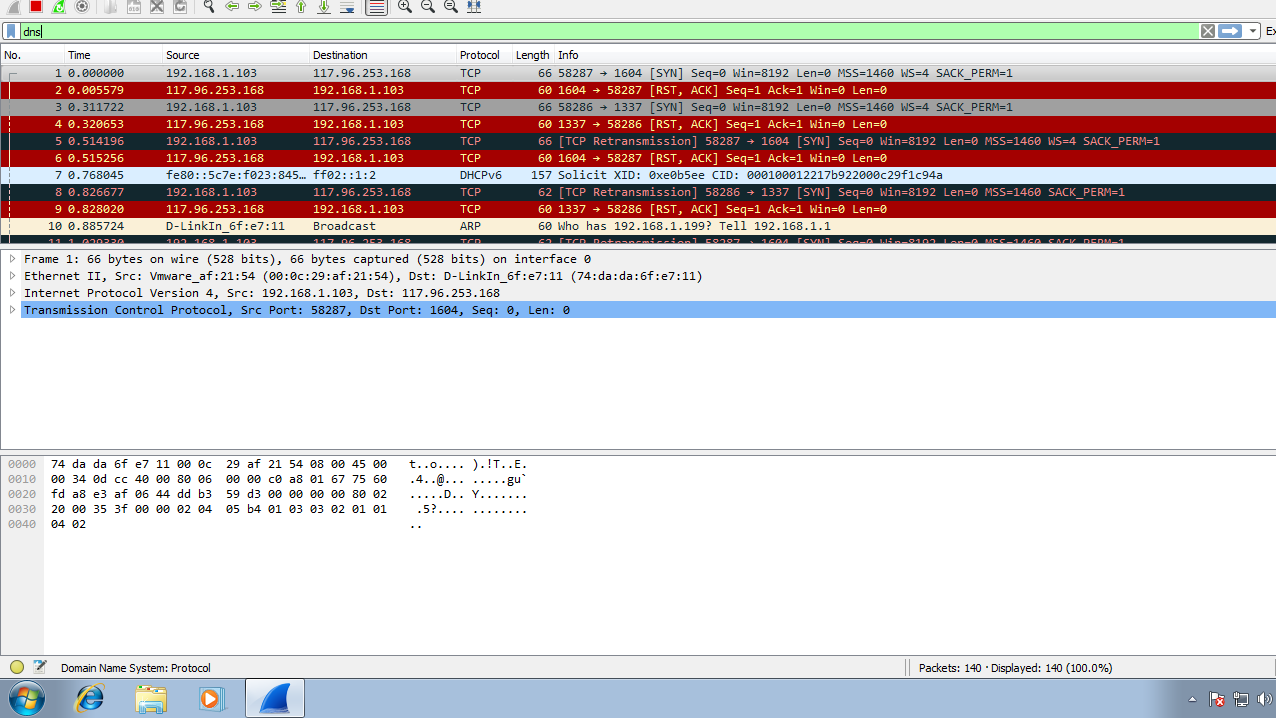
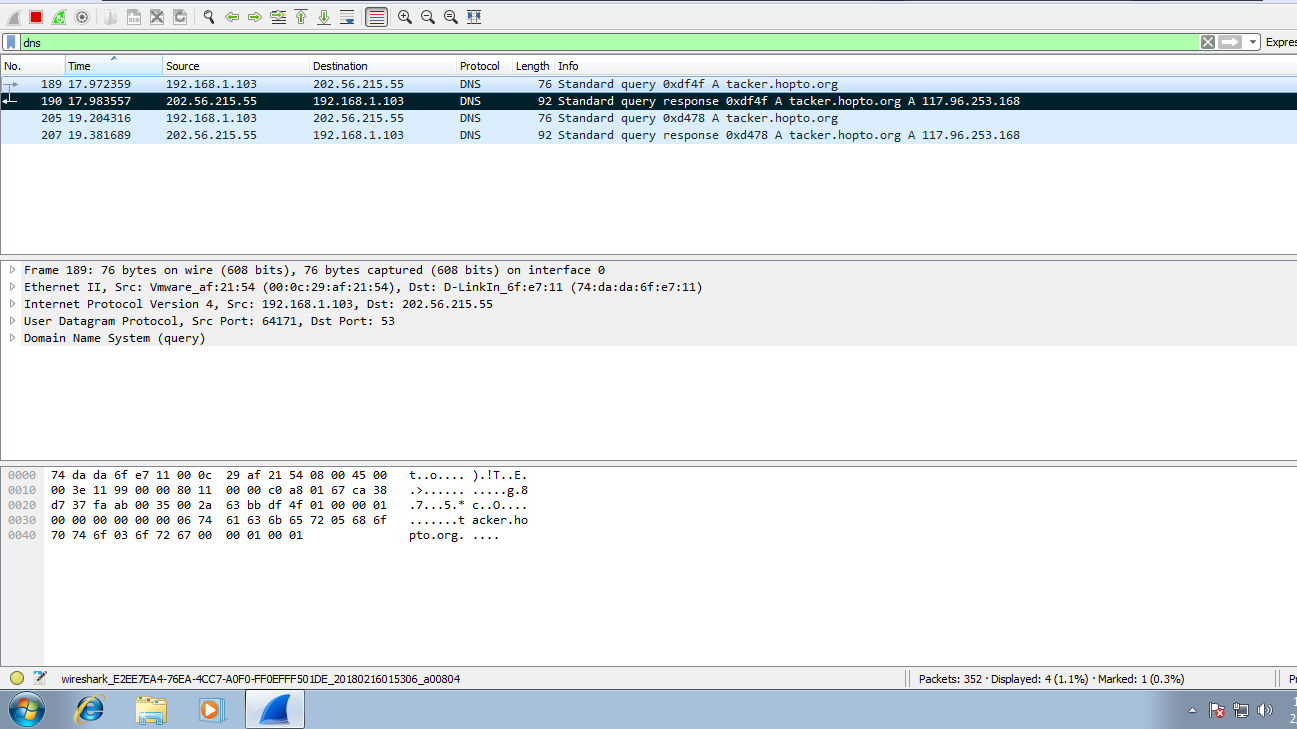
- Tracing the Reverse Connection : Starting Wireshark by selecting the Adapter you want to capture the packets of and Searching for “DNS” Packets.
So Wireshark will start capturing and gathering all the Packets (Data Flowing in the Network) from a particular Machine and show us with the help of filters like IP Addresses , Protocols etc. So If a Attacker has established a Reverse Connection through a Trojan, Wireshark will capture those Reverse Connection Packets along with all the Packets. After capturing a Multiple amount of Packets, we will use a Protocol Filter of DNS which will probably show the reverse connection established through a Dynamic DNS.
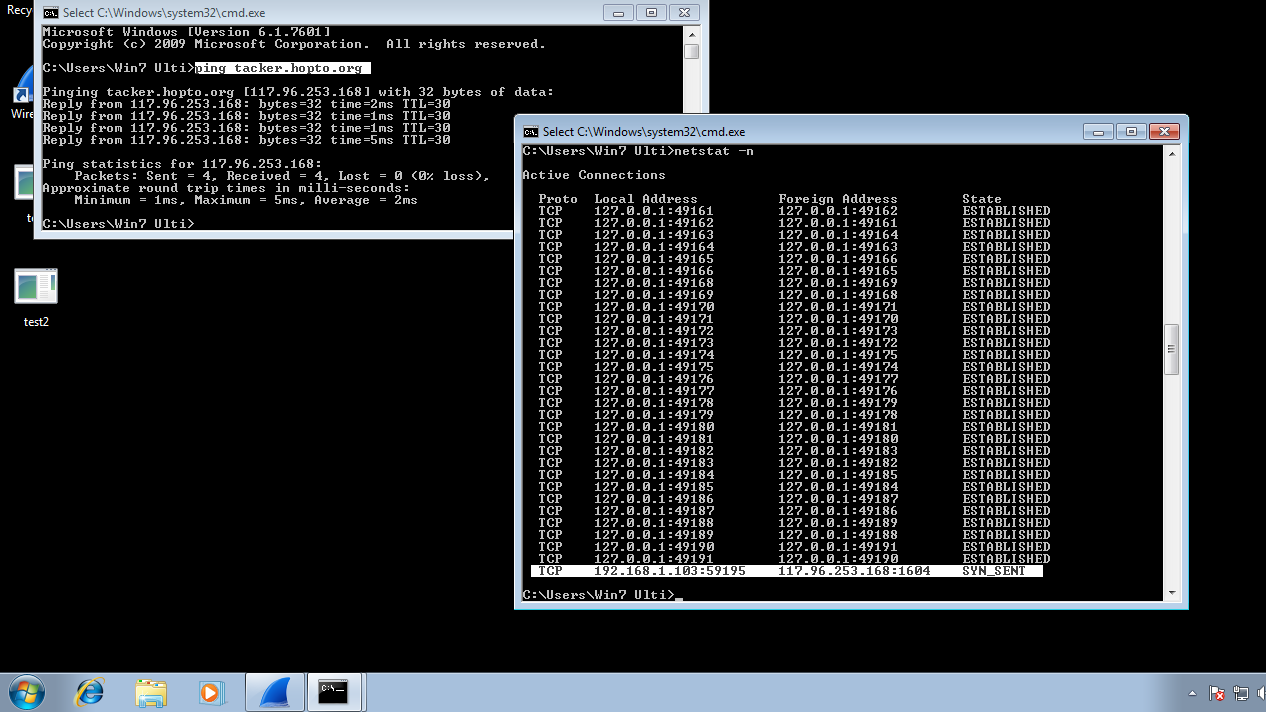
Ping the DNS we got in the DNS Packets through Wireshark. (Pinging will check that whether that DDNS Host is Connected to our Machine and is alive or not along with the IP Address of that Host DDNS).
$ ping tacker.hopto.org
$ ping tacker.hopto.org
For verifying the Established Connection through a DNS Foreign Address scanning through Netstat. $ netstat -n
Terminating the Reverse Connection :
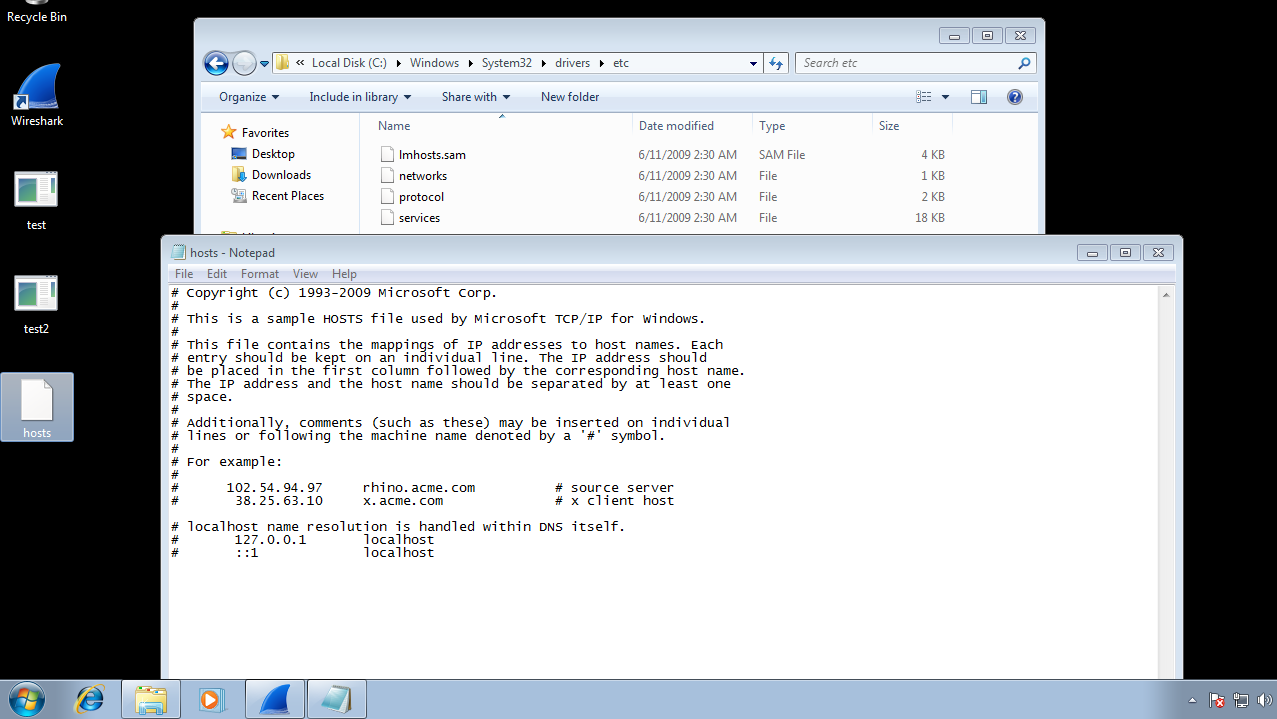
Blocking DNS Host Name to prevent further Reverse Connection from that same Host DNS.
- $ Go to C:\Windows\System32\drivers\etc
- $ Move the Hosts File to any other Folder.
- $ Open it using a Editor.
$ Scroll down and go the Host DNS you found on your Wireshark Results and put 127.0.0.1 (which is a loopback Localhost IP Address) and paste the Hosts file back to its Earlier Destination.
Conclusion
Whether a Trojan is executed in the same Network or in Different Networks via Dynamic Host DNS, you’ll be able to Terminate the connection through above steps. Once the Connection is Terminated, the Trojan has to be again executed for the Reverse Connection. If the Trojan is Executed into a Same Particular Network, you’ll be able to find the Attacker’s IP and Port on which he/she has established a Reverse Connection and then the Victim can go through the DHCP Server and find out the that who is the Attacker by DHCP Client List and with other scanners in that Particular Network.
If the Attacker is hosting the Reverse Connection via that Trojan, the user/victim should always have the eyes on the traffic it’s machine is passing on. If user will find anything suspicious which is not initiated by them, then that suspicious thing can be further enumerated that why it is running on the Machine and if it is a Reverse Connection Trojan, the connection will be terminated by changing the “Hosts” file of Windows Operating System so that no further connection can be established with that Dynamic Host DNS or we can block the certain PORT by adding a new firewall rule set. At last, awareness of your environment can only help you from becoming a Victim of such attacks. So Stay Safe :)