FTPShell Client 6.70 (Enterprise Edition) - Stack Buffer Overflow (Metasploit) | CVE-2018-7573
Introduction Difficulty: Easy
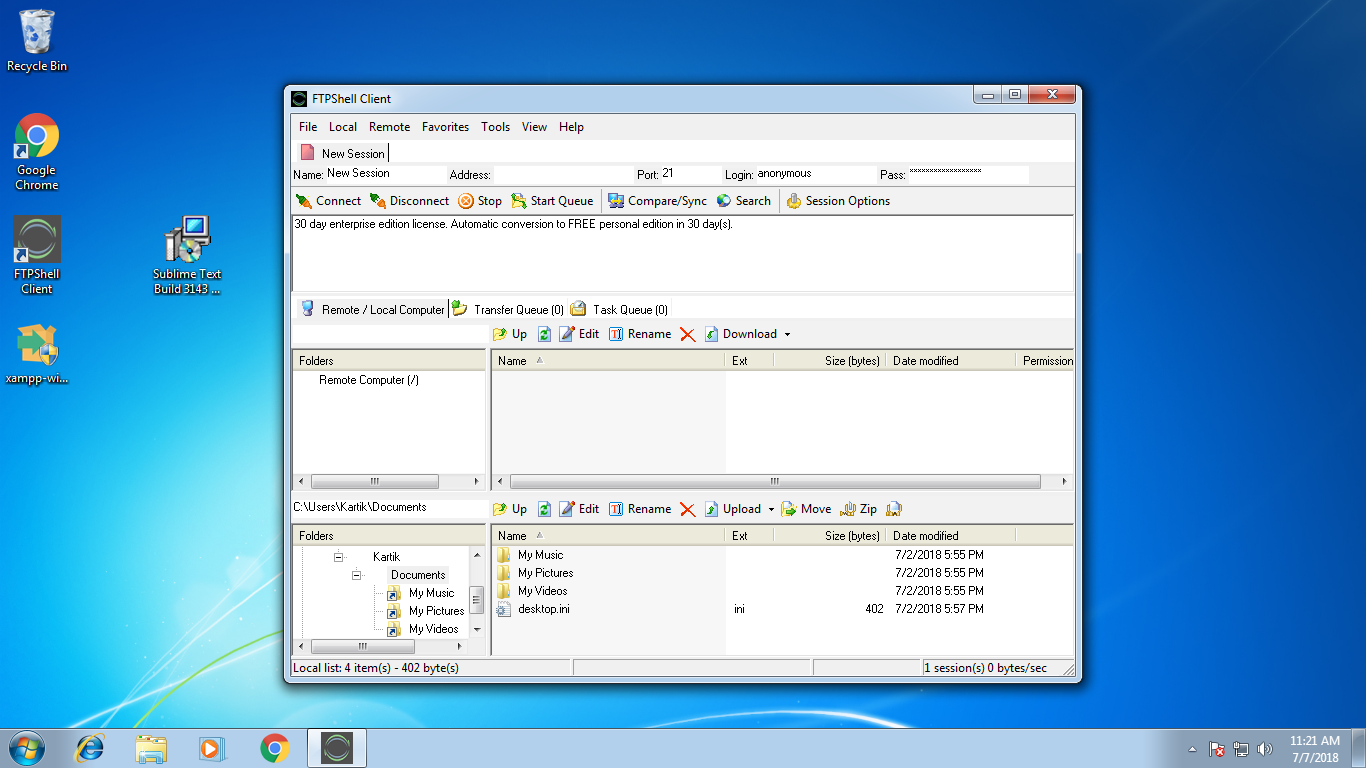
As the new exploit (CVE-2018-7573) is published which is capable to exploit the FTPShell Client 6.70 (Enterprise Edition). Download the FTPShell Client 6.70 and exploit from www.exploit-db.com and paste it in the subdirectory “exploit” of the Metasploit framework and initialise the database or you can easily update the Metasploit-framework by updating the OS.
Lab Environment
Victim’s machine:-Windows 7 Home Basic
Attacker's machine:-Linux kali 4.14.0-kali3-amd64 #1 SMP Debian 4.14.12-2kali1 (2018-01-08) x86_64 GNU/Linux
Vulnerable application:-FTPShell Client 6.70(Enterprise Edition)
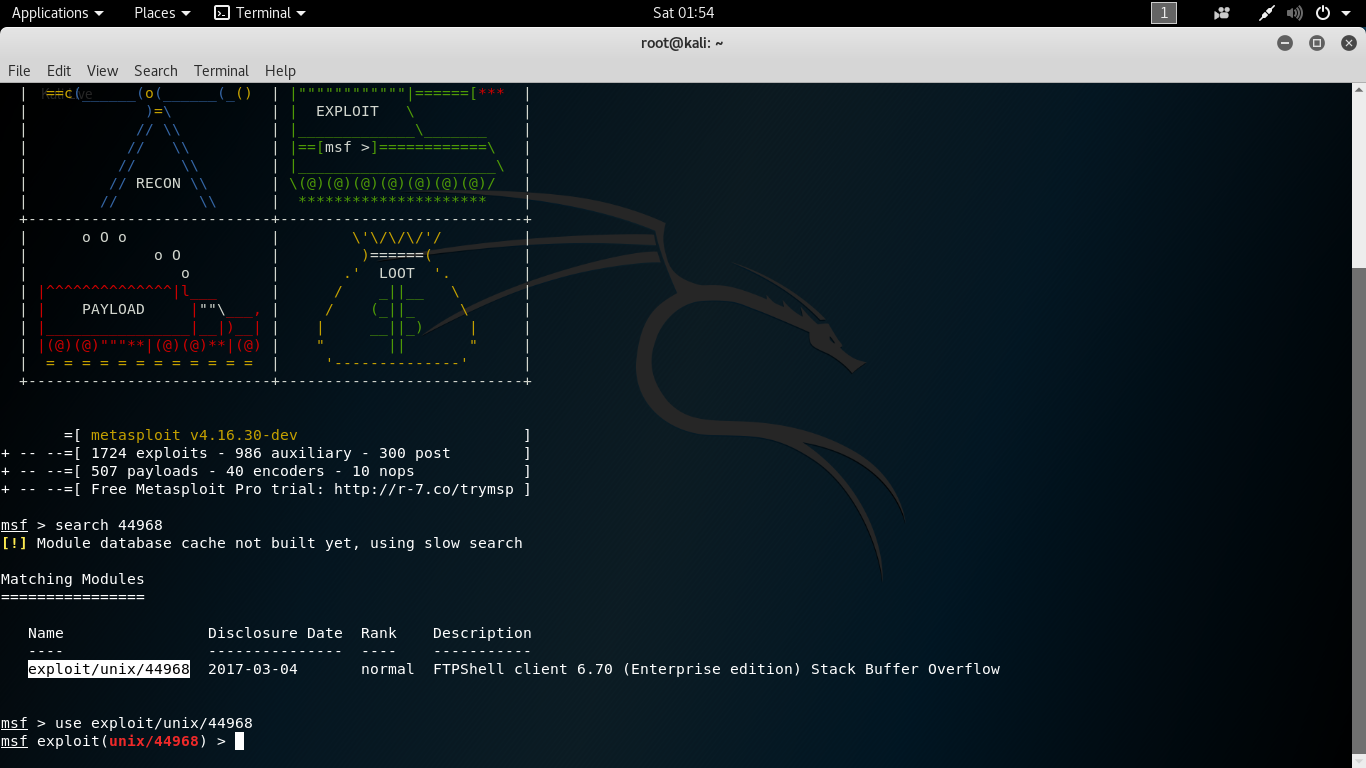
Step 2: Open msfconsole and search for 44968 and we get “exploit/unix/44968”. So lets use it :)


As the new exploit (CVE-2018-7573) is published which is capable to exploit the FTPShell Client 6.70 (Enterprise Edition). Download the FTPShell Client 6.70 and exploit from www.exploit-db.com and paste it in the subdirectory “exploit” of the Metasploit framework and initialise the database or you can easily update the Metasploit-framework by updating the OS.
Lab Environment
Victim’s machine:-Windows 7 Home Basic
Attacker's machine:-Linux kali 4.14.0-kali3-amd64 #1 SMP Debian 4.14.12-2kali1 (2018-01-08) x86_64 GNU/Linux
Vulnerable application:-FTPShell Client 6.70(Enterprise Edition)
Step 2: Open msfconsole and search for 44968 and we get “exploit/unix/44968”. So lets use it :)
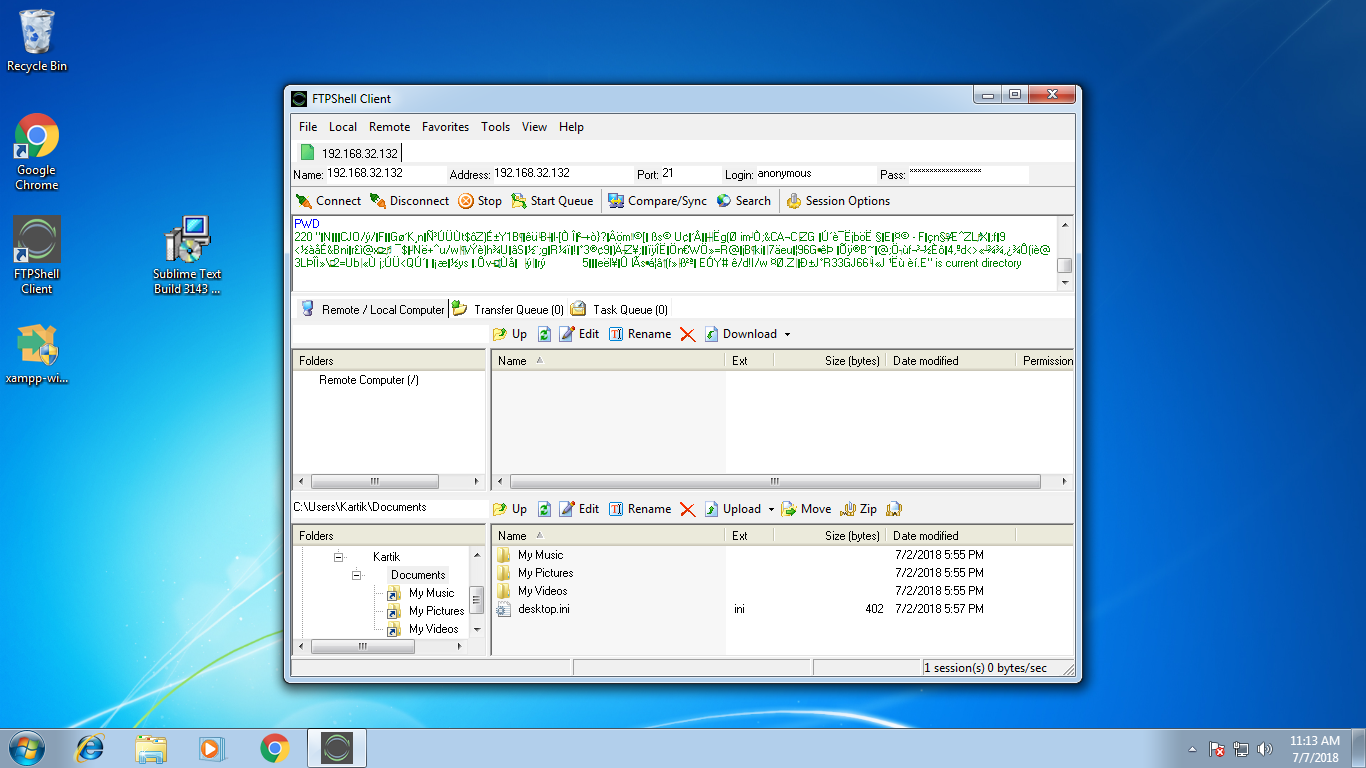
Step 3: This exploit needs only SRVHOST IP(Host to Listen)So we put the IP and run the exploit
Step 4: As the victim connects to the attacker by FTPShell client. As an attacker, you will get meterpreter session.
Step 5: Here we got the shell and now its all your playground. You can do privilege escalation and dig more in post-exploitation part to make the best use of it.