The Hitchhiker’s Guide to Bug Bounty Hunting Throughout the Galaxy. v2 by Nick Jenkins
Hello friends!
I want to talk a little about what has got me started on reviving my technology skills and started me on this journey. As a lifetime linux aficionado, I’ve been aware of the hacker sub-culture almost my whole life. It’s quite interesting to see how it has morphed and changed with technology. And what recently has gotten me hooked and excited about brushing up my dated computer skills is bug bounty hunting.
What is bug bounty hunting?
A bug bounty program is a deal offered by many websites and developers by which individuals can receive recognition and compensation for bugs, especially those pertaining to exploits and vulnerabilities- WikiPedia
As every aspect of our lives and how we do business is continually pushed online, it doesn’t take a rocket scientist to see that the need for security researchers will continue to grow. Code that is properly written and secure ensures sensitive data remains protected. And this benefits everybody. Which is why I decided to write this blog post, documenting the way to learn how to jump into this wild and crazy world of bug hunters. Are you ready? Hang on to your seat, it’s gonna be a crazy ride!

Report Triaged!!!
While the resources for how to become a bug bounty hunter are numerous and vast. They are spread out and the information can be hard to differentiate between what a newbie needs to learn now and what can be learned in the future. Hopefully this blog post alleviates some of that problem. I’m not going to dive into the detail by detail how-to of the matter, that’s for you and the resources to do later. This is just the roadmap, so to speak. I’m not gonna barrage you with a million resources either. Those lists are what I’m trying to help demystify. Here you will find the bare bones basics of what to use in your quest to become a bug bounty hunter.
Books
What? Really books in this day and age? Is he kidding? No I’m not. You can get the online version if your allergic to paper. ;)
- The Web Application Hacker’s Handbook – This is your new Bible. Sleep with it under your pillow.
- Web Hacking 101 by Peter Yaworski – This is your new Book of Prayers. So Pete, on his journey decided to write a book while he learned bug bounty hunting. This book goes over real live examples of bugs found and reported. Not to mention he updates it continually. We aren’t done with Peter. More on him and his awesomeness to the bug bounty community will come later.
- OWASP Testing Guide – This is the net standard from the awesome OWASP community. Think of OWASP as the bug-hunters union, sort of. Official security documentation. I have to include the docs right? ;)
- Breaking into Information Security by Andy Gill – Bug Hunting falls under Web Security/WebApp Security. These are really just a couple sub-specialties in Info Sec. Andy Gill offers a great intro into this world. I received this book because he offered it free over the holidays, so on top of the great book he is a great guy to boot!
- Mastering Modern Web Penetration Testing – And this book concludes the required reading for a new bounty hunter. Master the techniques in these books and you will be well on your way. This list is in no means everything there is but is all a new bug hunter needs.
Textbooks now covered, let’s move on to the lectures and the labs shall we? Again, this is not meant to be all inclusive, just what I think a new bounty hunter needs to know.
One of the things I’ve found awesome is the bug hunting community itself and I’m sure you will find the same thing as well. Everyone is super helpful and lead by example. For instance, two main platforms for bug bounties are HackerOne and BugCrowd. It’s only natural that they have the best content for learning the craft.
HackerOne’s: Hacker101 Course
This is hot of the press and quite simply amazing! It also shows that their finger is on the pulse, so to speak, in educating new hunters. But developers will also benefit with the mitigation section of each video detailing how to secure your code and apps! After watching the videos there are labs below them where you can practice your new found skills. Thanks for this one HackerOne!!
- *Update** HackerOne has done away with the labs and has now included a CTF! Not only can you practice your webapp skills but you get private invites for flags! Excellent combo for their Hacker101 curriculum. Way to go HackerOne!!
- https://ctf.hacker101.com/
Bugcrowd also has some amazing hacker wizards who also try to help you learn the craft.
How to Shot Web: This is Jason Haddix (@jhaddix) seminal DEFCON speech talking about how to get into the bug bounty game.
Bug Bounty Hunting Methodology v2: This is the follow up to Jason’s above talk. Watch them together and feel your brain growing.
- *Update** Not to be left behind, and being firm believers in educating the bug hunting crowd, BugCrowd also has a come out with BugCrowd University. Another great resource to really help you level up and learn bug bounty basics. https://www.youtube.com/playlist?list=PLIK9nm3mu-S4K4jMHwtplbrE1JMg0jyN-
That’s about as college block-styled as you get with those lectures and material. There is enough information here to learn the basics to finding bugs in the wild.
**Labs**
There are now a few excellent resources for practicing these newly learned ninja webapp hacking skills that are by now, exploding from your brain. I used to recommend setting up your own virtual lab and testing that way. And while it is an excellent way to learn these things. It’s not the only way now. With tech advances in web technology specifically you can find excellent labs to practice webapp pentesting. In particular I think these 2 are the best currently.
I am a Pentesterlabs Pro member as it was recommended to me multiple times by internet hacking mates I talk to. It was the best decision ever for me personally, to really help take my learning and skills to the next level. I can’t recommend Pentesterlabs Pro highly enough if webapp pentesting is what keeps you up at night. Check out the free resources they offer and I’m sure you will agree with me.
I also really highly recommend the labs at attackdefense.com Not limited to just webapps, every single lab can be run from your browser. Kali in the browser! What?!?! It’s great stuff. Go look. Now!
What about tools?
Glad you asked about that. There are two main tools that a bug hunter could use BurpSuite and OWASP Zed Attack Proxy. BurpSuite is commercial software that is quite excellent and has a huge fanbase. OWASP ZAP is open source. I’m a fan of open source software and ZAP is what I’ve been using. Both are highly extendible which will make using them alot easier. Let’s talk about that extendibility for a minute.
HUNT
Jason Haddix(@jhaddix) and the motley BugCrowd crew decided to help “pass the torch” and show new bug hunters where and how to look for bugs in the wild using Burp and Zap. The HUNT Scanner and Methodology is what they came up with. And it is amazing. I’ll let you check out the talk he did here:
HUNT and here is JP’s talk about HUNT as well. Watch them both! Well it’s also not just for Burp. @_sbzo also made it for OWASP ZAP as well. And this has been what I’ve been using. Why do I mention it? Well a new hunter isn’t going to know exactly where or how to start looking. That’s the experience that they lack coming forth. HUNT changes that by alerting on common parameters that are found with specific vulnerabilities. This was taken from actual reports by bounty hunters to BugCrowd. Cool, huh? So as you browse the site or app, you will start getting alerts about parameters that you should manually test. That’s the Scanner part.
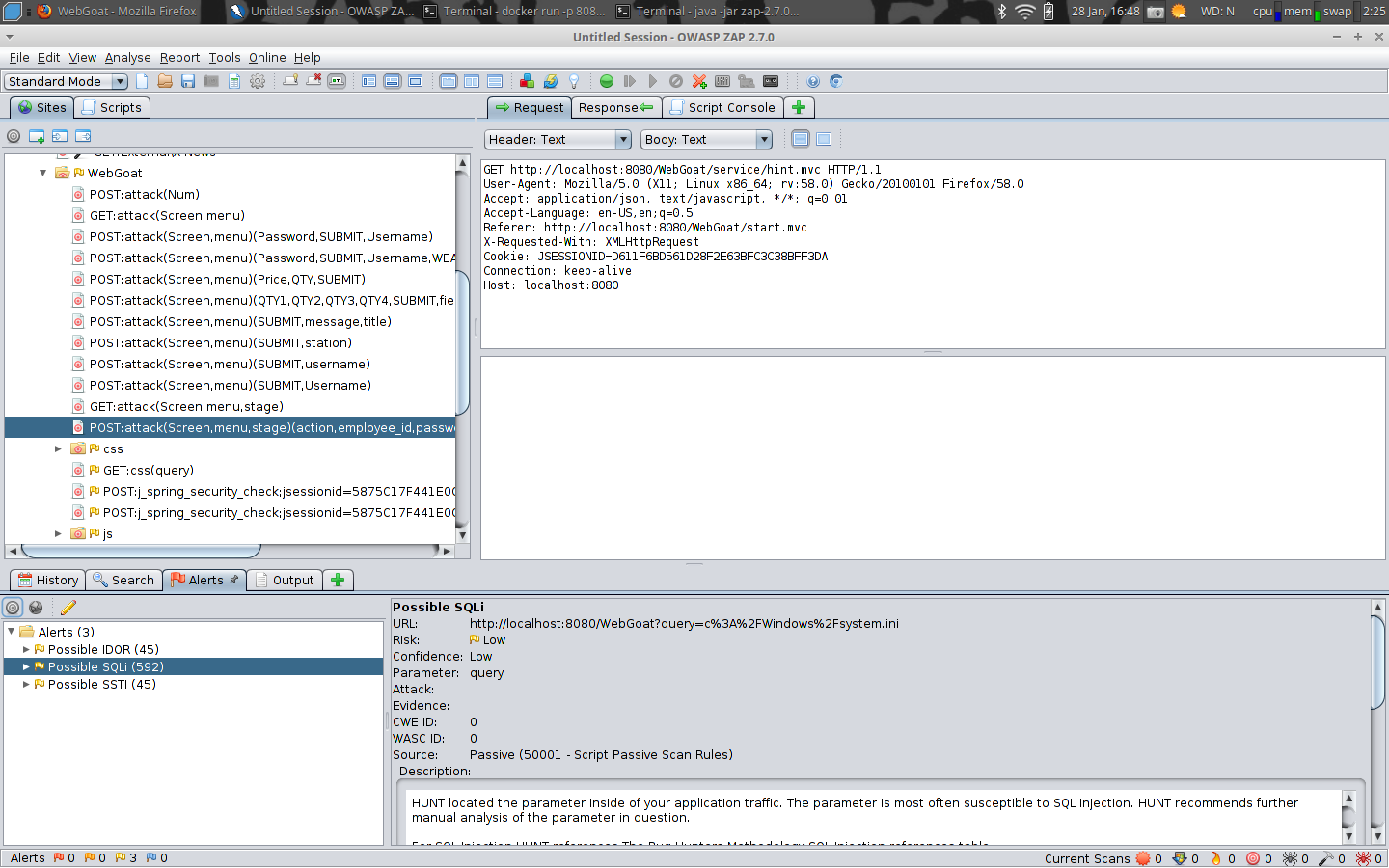
BugCrowd HUNT Scanner putting in work on OWASP WebGoat
The methodology part is equally as neat. You can’t see it but in the above image, where you to scroll down on the bottom right of the selected Possible SQLi, HUNT tells you further resources to check about that particular vulnerabilty, like CHP 9 of Web App Hackers Handbook, which is the chapter on SQLi, and a link to a write up or two of the same vulnerability by a researcher.
These scripts IMO are absolutely required for ANYONE just starting bug hunting, for the above mentioned reasons. They will definitely help you wrap your head around what to be on the lookout for.
And that’s all I’ll recommend for tools even though there are loads more you will use as a bug hunter. Why? Because you will learn that the best bug hunters out there, often use as little tooling as possible. Manual is better, is the mantra. And how can you argue? They are the best for a reason. I mention the above because I think that this particular setup Burp/HUNT or ZAP/Hunt gives a new hunter the best chance to effectively learn the craft, initially.
And the last thing I want to touch on is to learn bug hunting, you have to read and understand others who are doing it. This means write-ups. Bugs are submitted via write-ups and these write-ups allow you to get behind the thought process of other bug hunters.
But an equally incredible resource for a new bug hunter who wants to get into a bug hunter’s mentality is listening to a hunter talk about it. Remember Peter from Earlier? This is where he comes back in. He tracks down some of the best and most elusive bug hunters in the game, just to pick their brains and share it with the community. (Didn’t I say he was awesome earlier?) You can find those talks here under his Web Hacking Pro-tips. He has offered a lot of resources to new hunters and that is extremely commendable in my opinion. Thanks Peter Y!
Remember to never stop learning. This is the most crucial thing about hacking. And be persist ant. And practice, practice, practice. There are a multitude of platforms for this but here are a few that can help. These won’t be linked (I can’t do everything for you), Google them and choose one that suits you. I was using Damned Vulnerable Web App and the WebSec Dojo in VMs at first. But i’ve since changed to using WebGoat or Buggy Web App on a local server. Yes a VM is easier, but it’s good to know how to set a server up if you want to hack, isn’t it? So pick one or two or all the ones you can find and start trying to break them.
Give yourself structure though as if in a school lab. Today is XSS day. Today I’ll just practice XSS vulns on such and such. Tomorrow is CSRF day. I’ll practice CSRF skills on yada yada. You get the idea. Don’t just go in blind and hit AUTO Scan and hope for the best. Learn the vulnerabilities. Learn the tool. Then ratchet up the security option (most have this) and try again. See why the XSS that was working earlier isn’t now and how to find one that will fire. Google is your friend. There are lists and lists for everything for days. Continually test and push yourself and you will start to learn the skills.
Where am I in my journey? I’m with you. :) I’ve only found one measly XSS bug. And I found that ordering pizza. (Funny story, I’ll blog about it soon..) So I’m definitely not an expert. There are alot of people way smarter then me who could write something like this. But because I’m walking the same journey and just starting as well I thought it might be a little easier from the perspective of a fellow newbie. There are resources galore for learning the bug hunting craft and I’d be remiss to think I could include them all. So I just included the very few I think crucial and essential.
***Update** I wanna give a big shout out to all the awesome fellas from the #BBAC Crew that put up with a noobs questions and allow me to be sponge. You guys all rock!!
As with anything in life, there can be bad as well as good, I hope you are able to filter the bad elements out when it comes to bug bounty, and focus on the positive aspects of the community.
Learn how to ask a question!! This one thing, will serve you far more then any elite hacker you may DM. ;)
Hope this helps you on your bug bounty journey.
Originally posted: https://medium.com/@Nick_Jenkins/the-hitchhikers-guide-to-bug-bounty-hunting-throughout-the-galaxy-474ddb87ae15
The post The Hitchhiker’s Guide to Bug Bounty Hunting Throughout the Galaxy. v2 by Nick Jenkins appeared first on Hakin9 - IT Security Magazine.
from Hakin9 – IT Security Magazine http://bit.ly/2DgeK8U