Survey of Firmware Finds No Security Gains in 15 Years #Security #InternetOfThings #IoT #Firmware @securityledger

Via The Security Ledger, a survey of more than 6,000 firmware images spanning more than a decade finds no improvement in firmware security and lax security standards for the software running connected devices by Linksys, Netgear and other major vendors.
“Nobody is trying,” said Sarah Zatko, the Chief Scientist at the Cyber Independent Testing Lab (CITL), a non-profit organization that conducts independent tests of software security. “We found no consistency in a vendor or product line doing better or showing improvement. There was no evidence that anybody is making a concerted effort to address the safety hygiene of their products,” she said.
Zatko presented the findings of CITL’s extensive study in Las Vegas on Friday on the sidelines of the Black Hat and DEF CON conferences at an event hosted by The Hewlett Foundation. CITL was started by Sarah and her husband Peiter (aka “Mudge”) Zatko. It bills itself as a kind of “Consumer Reports” for cyber security.
The CITL study surveyed firmware from 18 vendors including ASUS, D-link, Linksys, NETGEAR, Ubiquiti and others. In all, more than 6,000 firmware versions were analyzed, totaling close to 3 million binaries created from 2003 to 2018. It is the first longitudinal study of IoT software safety, according to Zatko.
CITL researchers studied publicly available firmware images and evaluated them for the presence of standard security features such as the use of non-executable stacks, Address Space Layout Randomization (ASLR) and stack guards, which prevent buffer overflow attacks.
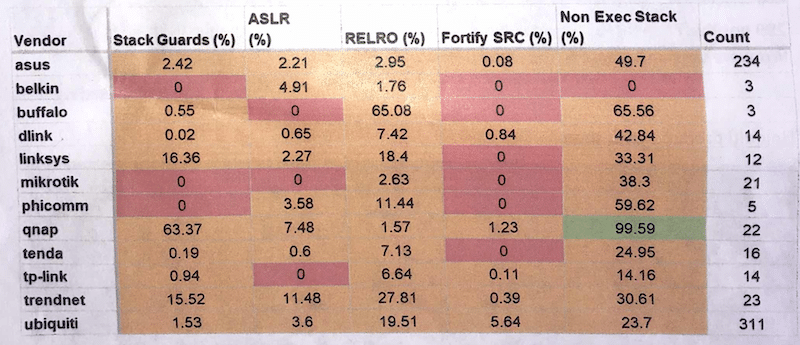
Zatko said much of the conversation about IoT security focuses on software applications, but misses the security of firmware. Hardware vendors need to do much more to harden their devices prior to release. That means assessing the security of software development tools and implementing basic hardening consistently.
See more on the security ledger.