Dcomrade - Powershell Script For Enumerating Vulnerable Dcom Applications
DCOMrade is a Powershell script that is able to enumerate the possible vulnerable DCOM applications that mightiness allow for lateral movement, code execution, information exfiltration, etc. The script is cook to piece of employment amongst Powershell 2.0 but volition piece of employment amongst all versions to a higher house every bit well. The script currently supports the next Windows operating systems (both x86 in addition to x64):
- Microsoft Windows 7
- Microsoft Windows 10
- Microsoft Windows Server 2012 / 2012 R2
- Microsoft Windows Server 2016
How it works
The script was made based on the inquiry done past times Matt Nelson (@enigma0x3), particularly the round 2 blogpost that goes into finding DCOM applications that mightiness endure useful for pentesters in addition to cherry teams.
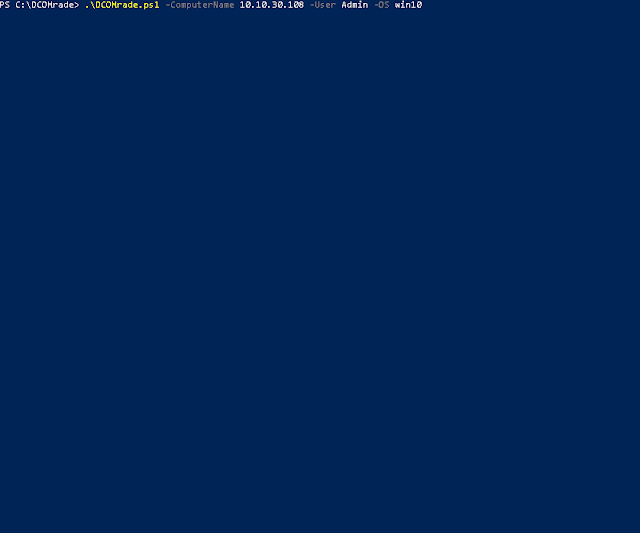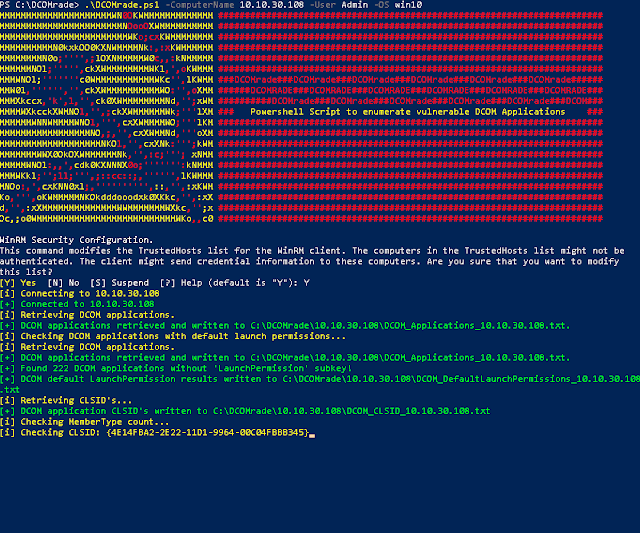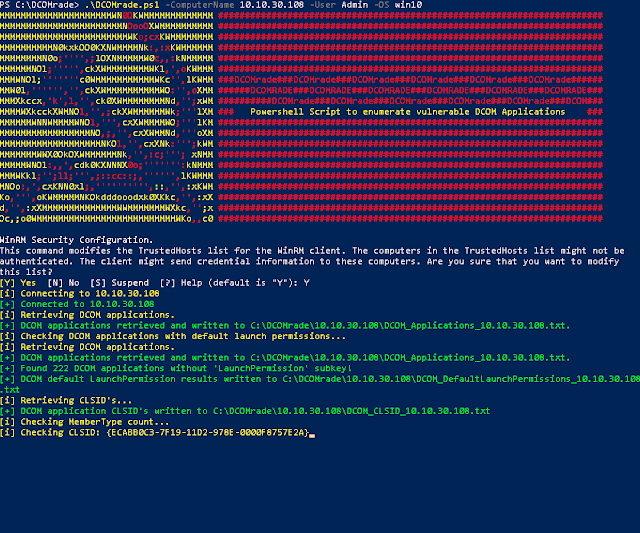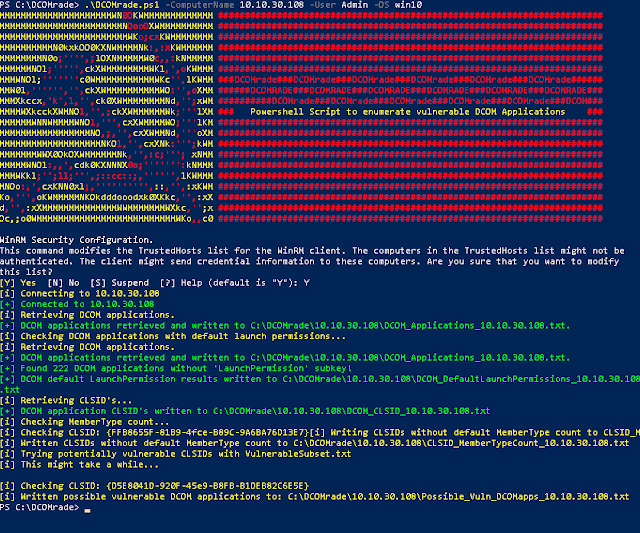
First a remote connective amongst the target organization is made, this connective is used throughout the script for a multitude of operations. H5N1 Powershell ascendance is executed on the target organization that retrieves all the DCOM applications in addition to their AppID's. The AppID's are used to loop through the Windows Registry in addition to banking enterprise agree for whatsoever AppID that does non conduct maintain the
LaunchPermission subkey ready inwards their entry, these AppID's are stored in addition to used to recall their associated CLSID's.The script uses a specific blacklist amongst each OS, this is why at that spot are dissimilar options for the target operating system. The blacklist skips CLSID entries that mightiness hang the script because of DCOM applications that cannot endure activated, this reduces the charge on the target organization in addition to reduces the fourth dimension for the script to complete.
With the CLSID, the DCOM application associated amongst it tin endure activated. The 'Shortcut' CLSID is used to count the amount of
MemberTypes associated amongst it, this is done to banking enterprise agree the default amount of MemberTypes. This reveal is used to banking enterprise agree for the CLSID's that concord anything dissimilar than this amount. The script does this amongst the CLSID of the 'Shortcut' (HKEY_CLASSES_ROOT\CLSID\{00021401-0000-0000-C000-000000000046}) because this is a shared CLSID across the Microsoft Windows operating systems. The CLSID's amongst a dissimilar amount of MemberTypes mightiness concord a Method or Property that tin endure (ab)used, in addition to volition endure added to an array.The CLSID's inwards the array are beingness checked on strings inwards the
MemberTypes that mightiness signal a way to (ab)use it, this listing of strings tin endure flora inwards the VulnerableSubset file. Please authorities notation that this listing is past times no agency a consummate listing to discover every unmarried vulnerable DCOM application, but this listing beingness a dynamic constituent of the procedure should laissez passer the user of the script a way to await for specific strings that migth signal a functionality of a DCOM application that mightiness endure useful for their purpose.The results of the script are outputted inwards a HTML study in addition to should endure usable for auditing a organization every bit a preventive measure. For the offensive side I created an Empire module which at the fourth dimension of writing is awaiting blessing to endure added to the master copy branch. If yous would similar to add together this to Empire yourself yous tin produce in addition to thence past times adding the module located here.
For a total technical explanation of the idea, the script in addition to possible detection methods yous tin read the research paper associated amongst this.
Prerequisites
The script, piece non beingness used every bit an Empire module, has but about limitations every bit the working of the script in addition to how it connects amongst the target machine differs.
- For this script to work, the Windows Remote Management services demand to endure allowed inwards the Windows Firewall (5985);
- If the target system's network profile is ready to
Publicthe next ascendance needs to endure executed to allow Windows Remote Management services beingness used on the target system:Enable-PSRemoting -SkipNetworkProfilecheck -Force - This script solely industrial plant when 1 has the credentials of a local Administrator on the target system. Without these credentials yous volition non endure able to get-go a remote session amongst the target machine, or endure able to activate DCOM applications.
Example usage
When inwards a Microsoft Windows domain:
.\DCOMrade.ps1 -ComputerName [Computername / IP] -User [Local Administrator] -OS [Operating System] -Domain [Domain name].\DCOMrade.ps1 -ComputerName [Computername / IP] -User [Local Administrator] -OS [Operating System]Limitations
- Currently the script does endeavor to loose whatsoever instantiated / activated DCOM applications but but about activations get-go novel processes (such every bit Internet Explorer), the procedure could endure stopped but this would hateful that if a user on the target organization is using that item application, this procedure volition halt for them every bit well;
- Another thing, which in all likelihood has to produce amongst bad my coding skills, is that the script mightiness innovate considerable charge on the target organization if the target organization does non conduct maintain a lot of resources. Be considerate when using this inwards a production surroundings or on servers;
- The script mightiness accept but about fourth dimension to execute completely, this depends on the amount of DCOM applications in addition to the size of the vulnerable subset file.
Acknowledgements
This script was inspired past times a DCOM lateral displace workshop that was given past times Eva Tanaskoska, without this workshop the whole sentiment for trying to enumerate this inwards an automated fashion would never endure conceived.
Thanks to Matt Nelson's (a.k.a. @enigma0x3) inquiry I was able to discover plenty information to come upwardly up amongst a cast of automation.
Philip Tsukerman's article which sums upwardly almost of the available DCOM techniques for lateral displace in addition to going into how these work.