H2t - Scans A Website As Well As Suggests Safety Headers To Apply
h2t is a uncomplicated tool to assistance sysadmins to hardening their websites.
Until at in i trial h2t checks the website headers too recommends how to larn inwards better.
Dependences
Install
Usage
h2t has subcommands: list too scan.
List Subcommand
The list subcommand lists all headers cataloged inwards h2t too tin demo informations almost it every bit a description, links for to a greater extent than information too for how to's.
Scan Subcommand
The scan subcommand perform a scan inwards a website looking for their headers.
Output
For at in i trial the output is exclusively inwards normal mode. Understant it every bit follows:
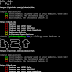
Screenshots
List h2t catalog
Scan from file
Scan url
Scan verbose
Headers information
Until at in i trial h2t checks the website headers too recommends how to larn inwards better.
Dependences
Install
$ git clone https://github.com/gildasio/h2t $ cd h2t $ pip install -r requirements.txt $ ./h2t.py -hUsage
h2t has subcommands: list too scan.
$ ./h2t.py -h usage: h2t.py [-h] {list,l,scan,s} ... h2t - HTTP Hardening Tool positional arguments: {list,l,scan,s} sub-command assistance listing (l) demo a listing of available headers inwards h2t catalog (that tin live on used inwards scan subcommand -H option) scan (s) scan url to hardening headers optional arguments: -h, --help demo this assistance message too exitList Subcommand
The list subcommand lists all headers cataloged inwards h2t too tin demo informations almost it every bit a description, links for to a greater extent than information too for how to's.
$ ./h2t.py listing -h usage: h2t.py listing [-h] [-p PRINT [PRINT ...]] [-B] [-a | -H HEADERS [HEADERS ...]] optional arguments: -h, --help demo this assistance message too leave of absence -p PRINT [PRINT ...], --print PRINT [PRINT ...] a listing of additional information almost the headers to print. For at in i trial at that topographic point are 2 options: description too refs (you tin move either or both) -B, --no-banner don't impress the h2t banner -a, --all listing all available headers [default] -H HEADERS [HEADERS ...], --headers HEADERS [HEADERS ...] a listing of headers to await for inwards the h2t catalogScan Subcommand
The scan subcommand perform a scan inwards a website looking for their headers.
$ ./h2t.py scan -h usage: h2t.py scan [-h] [-v] [-a] [-g] [-b] [-H HEADERS [HEADERS ...]] [-p PRINT [PRINT ...]] [-i IGNORE_HEADERS [IGNORE_HEADERS ...]] [-B] [-E] [-n] [-u USER_AGENT] [-r | -s] url positional arguments: url url to await for optional arguments: -h, --help demo this assistance message too leave of absence -v, --verbose increase output verbosity: -v impress reply headers, -vv impress reply too asking headers -a, --all scan all cataloged headers [default] -g, --good scan practiced headers exclusively -b, --bad scan bad headers exclusively -H HEADERS [HEADERS ...], --headers HEADERS [HEADERS ...] scan exclusively these headers (see available inwards listing sub- command) -p PRINT [PRINT ...], --print PRINT [PRINT ...] a listing of additional information almost the headers to print. For at in i trial at that topographic point are 2 options: description too refs (you tin move either or both) -i IGNORE_HEADERS [IGNORE_HEADERS ...], --ignore-headers IGNORE_HEADERS [IGNORE_HEADERS ...] a listing of headers to ignore inwards the results -B, --no-banner don't impress the h2t banner -E, --no-explanation don't impress the h2t output explanation -o {normal,csv,json}, --output {normal,csv,json} select which output format to move (available: normal, csv, json) -n, --no-redirect don't follow http redirects -u USER_AGENT, --user-agent USER_AGENT laid user agent to scan asking -k, --insecure don't verify SSL certificate every bit valid -r, --recommendation output exclusively recommendations [default] -s, --status output actual condition (eg: real headers only)Output
For at in i trial the output is exclusively inwards normal mode. Understant it every bit follows:
- [+] Red Headers are bad headers that opened upwardly a breach on your website or mayhap demo a lots of information. We recommend cook it.
- [+] Yellow Headers are practiced headers that is non applied on your website. We recommend apply them.
- [-] Green Headers are practiced headers that is already used inwards your website. It's shown when move
-sflag.
- Cookie HTTP Only would live on practiced to live on applied
- Cookie over SSL/TLS would live on practiced to live on applied
- Server header would live on practiced to live on removed
- Referrer-Policy would live on practiced to live on applied
- X-Frame-Options is already inwards use, nil to produce here
- X-XSS-Protection is already inwards use, nil to produce here
Screenshots
List h2t catalog
Scan from file
Scan url
Scan verbose
Headers information