Lightbulb Framework - Tools For Auditing Wafs
LightBulb is an opened upwards source python framework for auditing spider web application firewalls as well as filters.
Synopsis
The framework consists of ii top dog algorithms:
- GOFA: An active learning algorithm that infers symbolic representations of automata inwards the measure membership/equivalence inquiry model.
Active learning algorithms permits the analysis of filter as well as sanitizer programs remotely, i.e. given simply the mightiness to inquiry the targeted plan as well as honour the output.
- SFADiff: Influenza A virus subtype H5N1 black-box differential testing algorithm based on Symbolic Finite Automata (SFA) learning
Finding differences betwixt programs alongside similar functionality is an of import safety work every bit such differences tin live on used for fingerprinting or creating evasion attacks against safety software similar Web Application Firewalls (WAFs) which are designed to give away malicious inputs to spider web applications.
Motivation
Web Applications Firewalls (WAFs) are primal edifice blocks of modern application security. For example, the PCI measure for organizations treatment credit card transactions dictates that whatever application facing the network should live on either protected past times a WAF or successfully transcend a code review process. Nevertheless, despite their popularity as well as importance, auditing spider web application firewalls remains a challenging as well as complex task. Finding attacks that bypass the firewall unremarkably requires proficient domain cognition for a specific vulnerability class. Thus, penetration testers non armed alongside this cognition are left alongside publicly available lists of laid on strings, similar the XSS Cheat Sheet, which are unremarkably insufficient for thoroughly evaluating the safety of a WAF product.
Commands Usage
Main interface commands:
| Command | Description |
|---|---|
| core | Shows available heart as well as mortal modules |
| utils | Shows available inquiry handlers |
| info | Prints module information |
| library | Enters library |
| modules | Shows available application modules |
| use | Enters module |
| start | Initiate algorithm |
| help | Prints help |
| status | Checks as well as installs required packages |
| complete | Prints bash completion command |
| Command | Description |
|---|---|
| back | Go dorsum to top dog menu |
| info | Prints electrical flow module information |
| library | Enters library |
| options | Shows available options |
| define | Set an choice value |
| start | Initiate algoritm |
| complete | Prints bash completion command |
| Command | Description |
|---|---|
| back | Go dorsum to top dog menu |
| info | Prints requested module information (folder must live on located inwards lightbulb/data/) |
| cat | Prints requested module (folder must live on located inwards lightbulb/data/) |
| modules | Shows available library modules inwards the requested folder (folder must live on located inwards lightbulb/data/) |
| search | Searches available library modules using comma separated keywords |
| complete | Prints bash completion command |
Installation
Prepare your system
First yous accept to verify that your scheme supports flex, python dev, pip as well as construct utilities:
For apt platforms (ubuntu, debian...):
sudo apt-get install flex sudo apt-get install python-pip sudo apt-get install python-dev sudo apt-get install build-essential sudo apt-get install libmysqlclient-dev sudo yum install -y python-pip sudo yum install -y python-devel sudo yum install -y wget sudo yum groupinstall -y 'Development Tools' sudo yum install -y mysql-devel sudo yum install -y MySQL-pythonInstall Lightbulb
In club to utilization the application without consummate packet installation:
git clone https://github.com/lightbulb-framework/lightbulb-framework cd lightbulb-framework brand lightbulb statuspip install setuptools --upgrade pip install lightbulb-framework lightbulb statuspip install virtualenv virtualenv env source env/bin/activate pip install lightbulb-framework lightbulb statusIt should live on noted that the "lightbulb status" dominance is non necessary if yous are going to utilization the Burp Extension. The argue is that this dominance installs the "openfst" as well as "mysql" bindings as well as the extension past times default is using Jython, which does non back upwards C bindings. It is recommended to utilization the dominance simply if yous desire to modify the Burp extension configuration from the settings as well as enable the native support.
It is also possible to utilization a docker instance:
docker line lightbulb/lightbulb-frameworkInstall Burp Extension
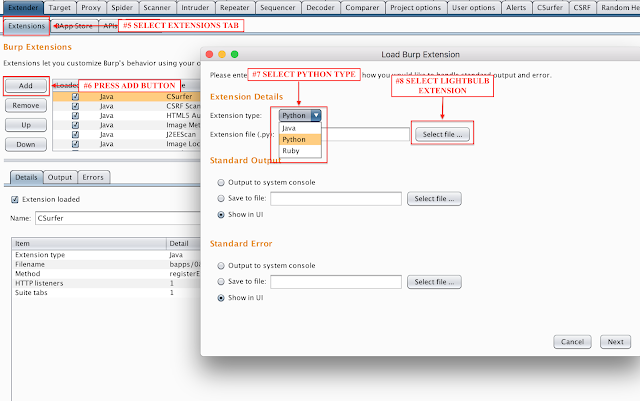
If yous wishing to utilization the novel GUI, yous tin utilization the extension for the Burp Suite. First yous accept to setup a working environs alongside Burp Proxy as well as Jython
- Download the latest Jython from here
- Find your local python packages installation folder*
- Configure Burp Extender to utilization these values, every bit shown below*
- Select the novel LightBulb module ("BurpExtension.py") as well as laid the extension type to live on "Python"
*You tin ignore this step, as well as install the standalone version which contains all the required python packages included. You tin download it here
Examples
Check out the Wiki page for usage examples.
Contributors
- George Argyros
- Ioannis Stais
- Suman Jana
- Angelos D. Keromytis
- Aggelos Kiayias
References
- G. Argyros, I. Stais, S. Jana, A. D. Keromytis, as well as A. Kiayias. 2016. SFADiff: Automated Evasion Attacks as well as Fingerprinting Using Black-box Differential Automata Learning. In Proceedings of the 2016 ACM SIGSAC Conference on Computer as well as Communications Security (CCS '16). ACM, New York, NY, USA, 1690-1701. doi: 10.1145/2976749.2978383
- G. Argyros, I. Stais, A. Kiayias as well as A. D. Keromytis, "Back inwards Black: Towards Formal, Black Box Analysis of Sanitizers as well as Filters," 2016 IEEE Symposium on Security as well as Privacy (SP), San Jose, CA, 2016, pp. 91-109. doi: 10.1109/SP.2016.14