Ponce - Ida Plugin For Symbolic Execution Only One-Click Away!
Ponce (pronounced [ 'poN θe ] pon-they ) is an IDA Pro plugin that provides users the mightiness to perform taint analysis too symbolic execution over binaries inward an slow too intuitive fashion. With Ponce y'all are 1 click away from getting all the mightiness from cutting border symbolic execution. Entirely written inward C/C++.
Why?
Symbolic execution is non a novel concept inward the safety community. It has been some for years but it is non until the terminal duad of years that opened upwards source projects similar Triton too Angr stimulate got been created to address this need. Despite the availability of these projects, halt users are oftentimes left to implement specific usage cases themselves.
We addressed these needs past times creating Ponce, an IDA plugin that implements symbolic execution too taint analysis inside the most used disassembler/debugger for contrary engineers.
Installation
Ponce plant amongst both x86 too x64 binaries inward IDA 6.8 too IDA 6.9x. Installing the plugin is every bit unproblematic every bit copying the appropiate files from the latest builds to the
plugins\ folder inward your IDA installation directory.IDA 7.0.
Ponce has initial back upwards of IDA 7.0 for both x86 too x64 binaries inward Windows. The plugin named
Ponce64.dll should last copied from the latest_builds to the plugins\ folder inward your IDA installation directory. Starting from version 7.0, IDA64 should last used to piece of employment amongst both x86 too x64 binaries.Don't forget to register Ponce inward
plugins.cfg located inward the same folder past times adding the next line:Ponce Ponce Ctrl+Shift+Z 0 WINOS Support
Ponce plant on Windows, Linux too OSX natively!
Use cases
- Exploit development: Ponce tin forcefulness out assistance y'all create an exploit inward a far to a greater extent than efficient mode every bit the exploit developer may easily run across what parts of retentivity too which registers y'all control, also every bit possible addresses which tin forcefulness out last leveraged every bit ROP gadgets.
- Malware Analysis: Another usage of Ponce is related to malware code. Analyzing the commands a item solid unit of measurement of malware supports is easily determined past times symbolizing a unproblematic known command too negating all the atmospheric condition where the command is beingness checked.
- Protocol Reversing: One of the most interesting Ponce uses is the possibility of recognizing required magic numbers, headers or fifty-fifty entire protocols for controlled user input. For instance, Ponce tin forcefulness out assistance y'all to listing all the accepted arguments for a given command line binary or extract the file format required for a specific file parser.
- CTF: Ponce speeds upwards the procedure of reverse engineer binaries during CTFs. As Ponce is totally integrated into IDA y'all don't involve to worry most setup timing. It's ready to last used!
Use modes
- Tainting engine: This engine is used to create upwards one's take away heed at every stride of the binary's execution which parts of retentivity too registers are controllable past times the user input.
- Symbolic engine: This engine maintains a symbolic field of registers too component of retentivity at each stride inward a binary's execution path.
Examples
Use symbolic execution to solve a crackMe
Here nosotros tin forcefulness out run across the usage of the symbolic engine too how nosotros tin forcefulness out solve constrains:
- Passing unproblematic
aaaaaevery bit argument. - We showtime conduct the symbolic engine.
- We convert to symbolic the retentivity pointed past times argv[1] (
aaaaa) - Identify the symbolic status that brand us win too solve it.
- Test the solution.
The crackme source code tin forcefulness out last constitute here
Negate too inject a condition
In the adjacent gif nosotros tin forcefulness out run across the usage of automatic tainting too how nosotros tin forcefulness out negate a status too inject it inward retentivity patch debugging:
- We conduct the symbolic engine too laid the choice to symbolize
argv. - We position the status that needs to last satisfied to win the crackMe.
- We negate an inject the solution everytime a byte of our input is checked against the key.
- Finally nosotros larn the fundamental
elitethat has been injected inward retentivity too thus accomplish theWincode.
The crackme source code tin forcefulness out last constitute here
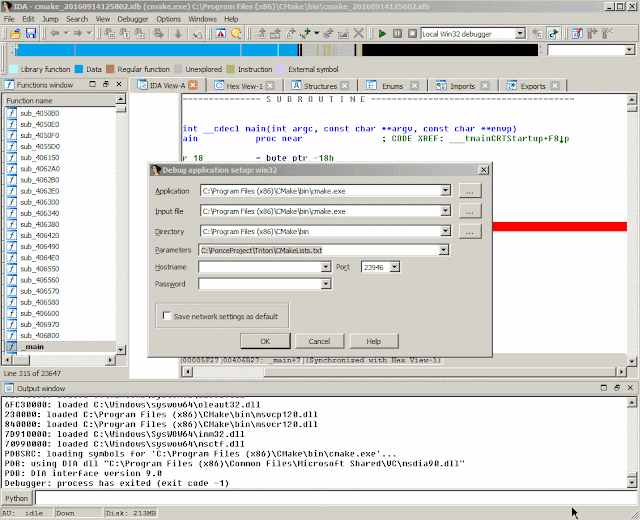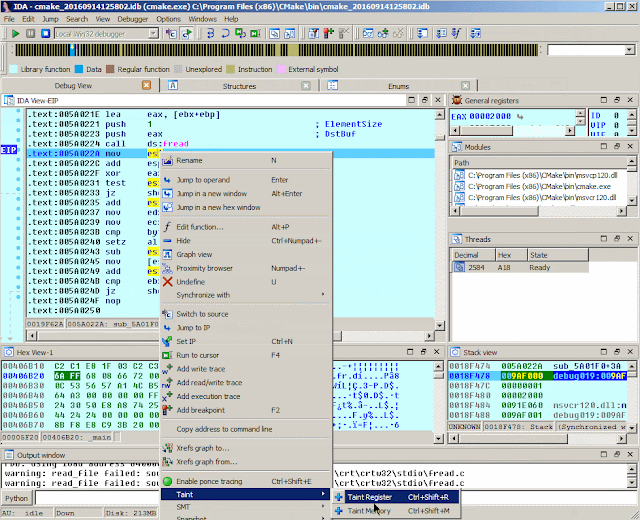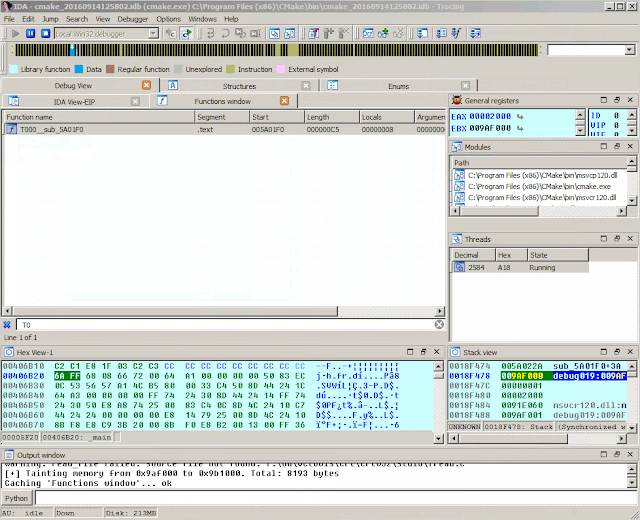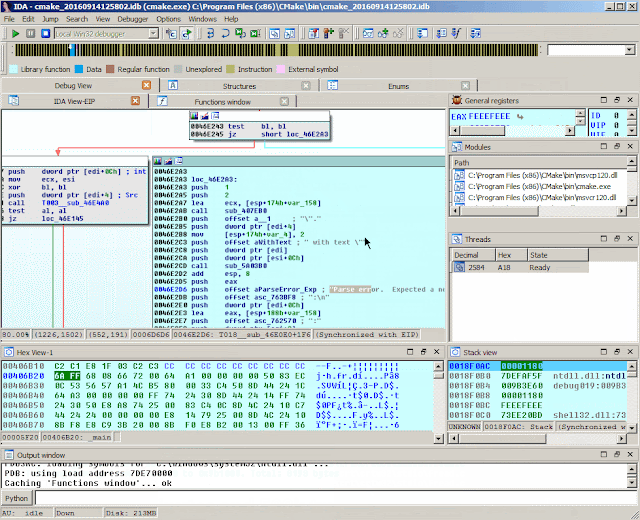
Using the tainting engine to rails user controlled input
In this instance nosotros tin forcefulness out run across the usage of the tainting engine amongst cmake. We are:
- Passing a file every bit declaration to cmake to stimulate got him parsing it.
- We conduct nosotros desire to usage the tainting engine
- We taint the buffer that ```fread()```` reads from the file.
- We resume the execution nether the debugger command to run across where the taint input is moved to.
- Ponce volition rename the tainted functions. These are the functions that somehow the user has influence on, non the merely executed functions.
Use Negate, Inject & Restore
In the adjacent instance nosotros are using the snapshot engine:
- Passing a file every bit argument.
- We conduct nosotros desire to usage the symbolic engine.
- We taint the buffer that ```fread()```` reads from the file.
- We create a snapshot inward the business office that parses the buffer read from the file.
- When a status is evaluated nosotros negate it, inject the solution inward retentivity too restore the snapshot amongst it.
- The solution volition last "valid" too then nosotros volition satisfy the real conditions.
The instance source code tin forcefulness out last constitute here
Usage
In this department nosotros volition listing the dissimilar Ponce options also every bit keyboard shortcuts:
- Access the configuration too taint/symbolic windows: Edit > Ponce > Show Config (Ctl+Shift+P too Ctl+Alt+T)
- Enable/Disable Ponce tracing (Ctl+Shift+E)
- Symbolize/taint a register (Ctl+Shift+R)
- Symbolize/taint memory. Can last done from the IDA View or the Hex View (Ctl+Shift+M)
- Solve formula (Ctl+Shift+S)
- Negate & Inject (Ctl+Shift+N)
- Negate, Inject & Restore Snaphot (Ctl+Shift+I)
- Create Execution Snapshot (Ctl+Shift+C)
- Restore Execution Snapshot (Ctl+Shift+S)
- Delete Execution Snapshot (Ctl+Shift+D)
- Execute Native (Ctl+Shift+F9)
##Triton Ponce relies on the Triton framework to render semantics, taint analysis too symbolic execution. Triton is an awesome Open Source projection sponsored past times Quarkslab too maintained mainly past times Jonathan Salwan amongst a rich library. We would similar to give thank y'all too endorse Jonathan's piece of employment amongst Triton. You rock! :)
Building
We render compiled binaries for Ponce, but if y'all desire to create your ain plugin y'all tin forcefulness out exercise too then using Visual Studio 2013. We tried to brand the edifice procedure every bit slow every bit possible:
- Clone the projection amongst submodules:
git clone --recursive https://github.com/illera88/PonceProject.git - Open
Build\PonceBuild\Ponce.sln: The projection configuration is ready to usage the includes too libraries shipped amongst the projection that reside inwardexternal-libs\. - The VS projection has a
Post-Build Eventthat volition motility the created binary plugin to the IDA plugin folder for you.copy /Y $(TargetPath) "C:\Program Files (x86)\IDA 6.9\plugins". NOTE: usage your IDA installation path.
- x86ReleaseStatic: volition create the 32 bits version statically linking every 3rd political party library into a whole large plugin file.
- x86ReleaseZ3dyn: volition create the 32 bits version statically linking every 3rd political party library but z3.lib.
- x64ReleaseStatic: volition create the 64 bits version statically linking every 3rd political party library into a whole large plugin file.
- x64ReleaseZ3dyn: volition create the 64 bits version statically linking every 3rd political party library but z3.lib.
z3.lib is 1.1Gb too the linking fourth dimension is considerable. That's the chief argue why nosotros stimulate got a edifice version that uses z3 dynamically (as a dll). If y'all are using z3 dynamically don't forget to re-create the libz3.dll file into the IDA's directory.If y'all desire to create Triton for linux or MacOsX banking concern gibe this file: https://github.com/illera88/Ponce/tree/master/builds/PonceBuild/nix/README.md
FAQ
Why the mention of Ponce?
Juan Ponce de León (1474 – July 1521) was a Castilian explorer too conquistador. He discovered Florida inward the United States. The IDA plugin volition assistance y'all discover, explore too hopefully conquer the dissimilar paths inward a binary.
Can Ponce last used to analyze Windows, OS X too Linux binaries?
Yes, y'all tin forcefulness out natively usage Ponce inward IDA for Windows or remotely attach to a Linux or OS X box too usage it. In the adjacent Ponce version nosotros volition natively back upwards Ponce for Linux too OS X IDA versions.
How many instructions per instant tin forcefulness out grip Ponce?
In our tests nosotros accomplish to procedure 3000 instructions per second. We conception to usage the PIN tracer IDA offers to increase the speed.
Something is non working!
Open an issue, nosotros volition solve it ASAP ;)
I dearest your project! Can I collaborate?
Sure! Please exercise draw requests too piece of employment inward the opened issues. We volition pay y'all inward beers for assistance ;)
Limitations
Concolic execution too Ponce stimulate got some problems:
- Symbolic retentivity load/write: When the index used to read a retentivity value is symbolic similar inward
x = aray[symbolic_index]some problems arise that could Pb on the unloosen of rails of the tainted/symbolized user controled input. - Triton doesn't piece of employment really good amongst floating indicate instructions.
Authors
- Alberto Garcia Illera (@algillera) alberto.garcia@salesforce.com
- Francisco Oca (@francisco_oca) foca@salesforce.com