Silketw - Flexible C# Wrapper For Etw (Event Tracing For Windows)
SilkETW is a flexible C# wrapper for ETW, it is meant to abstract away the complexities of ETW as well as hand people a unproblematic interface to perform interrogation as well as introspection. While SilkETW has obvious defensive (and offensive) applications it is primarily a interrogation tool inwards it's electrical current state.
For slow consumption, output information is serialized to JSON. The JSON information tin either live analyzed locally using PowerShell or shipped off to tertiary political party infrastructure such every bit Elasticsearch.
Implementation Details
Libraries
SilkETW is buit on .Net v4.5 as well as uses a disclose of tertiary political party libraries, every bit shown below. Please run across LICENSE-3RD-PARTY for farther details.
ModuleId Version LicenseUrl -------- ------- ---------- McMaster.Extensions.CommandLineUtils 2.3.2 https://licenses.nuget.org/Apache-2.0 Microsoft.Diagnostics.Tracing.TraceEvent 2.0.36 https://github.com/Microsoft/perfview/blob/master/LICENSE.TXT Newtonsoft.Json 12.0.1 https://licenses.nuget.org/MIT System.ValueTuple 4.4.0 https://github.com/dotnet/corefx/blob/master/LICENSE.TXT YaraSharp 1.3.1 https://github.com/stellarbear/YaraSharp/blob/master/LICENSECommand Line Options
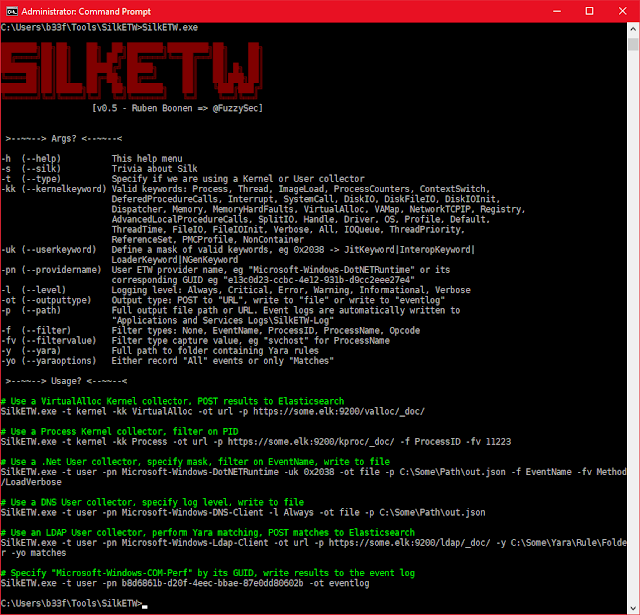
Command work usage is fairly withdraw frontward as well as user input is validated inwards the execution prologue. See the icon below for farther details.
JSON Output Structure
The JSON output, prior to serialization, is formatted according to the next C# struct.
public struct EventRecordStruct { world Guid ProviderGuid; world List YaraMatch; world string ProviderName; world string EventName; world TraceEventOpcode Opcode; world string OpcodeName; world DateTime TimeStamp; world int ThreadID; world int ProcessID; world string ProcessName; world int PointerSize; world int EventDataLength; world Hashtable XmlEventData; } { "ProviderGuid":"22fb2cd6-0e7b-422b-a0c7-2fad1fd0e716", "YaraMatch":[ ], "ProviderName":"Microsoft-Windows-Kernel-Process", "EventName":"ThreadStop/Stop", "Opcode":2, "OpcodeName":"Stop", "TimeStamp":"2019-03-03T17:58:14.2862348+00:00", "ThreadID":11996, "ProcessID":8416, "ProcessName":"", "PointerSize":8, "EventDataLength":76, "XmlEventData":{ "FormattedMessage":"Thread 11,996 (in Process 8,416) stopped. ", "StartAddr":"0x7fffe299a110", "ThreadID":"11,996", "UserStackLimit":"0x3d632000", "StackLimit":"0xfffff38632d39000", "MSec":"560.5709", "TebBase":"0x91c000", "CycleTime":"4,266,270", "ProcessID":"8,416", "PID":"8416", "StackBase":"0xfffff38632d40000", "SubProcessTag":"0", "TID":"11996", "ProviderName":"Microsoft-Windows-Kern el-Process", "PName":"", "UserStackBase":"0x3d640000", "EventName":"ThreadStop/Stop", "Win32StartAddr":"0x7fffe299a110" } }Usage
Filter information inwards PowerShell
You tin import JSON output from SilkETW inwards PowerShell using the next unproblematic function.
function Get-SilkData { param($Path) $JSONObject = @() Get-Content $Path | ForEach-Object { $JSONObject += $_ | ConvertFrom-Json } $JSONObject }SilkETW.exe -t heart as well as somebody -kk ImageLoad -ot file -p C:\Users\b33f\Desktop\mimikatz.jsonYara
SilkETW includes Yara functionality to filter or tag consequence data. Again, this has obvious defensive capabilities but it tin but every bit easily live used to augment your ETW research.
In this illustration nosotros volition exercise the next Yara dominion to honor Seatbelt execution inwards retentivity through Cobalt Strike's execute-assembly.
rule Seatbelt_GetTokenInformation { strings: $s1 = "ManagedInteropMethodName=GetTokenInformation" ascii broad nocase $s2 = "TOKEN_INFORMATION_CLASS" ascii broad nocase $s3 = /bool\(native int,valuetype \w+\.\w+\/\w+,native int,int32,int32&/ $s4 = "locals (int32,int64,int64,int64,int64,int32& pinned,bool,int32)" ascii broad nocase condition: all of ($s*) }SilkETW.exe -t user -pn Microsoft-Windows-DotNETRuntime -uk 0x2038 -l verbose -y C:\Users\b33f\Desktop\yara -yo matches -ot file -p C:\Users\b33f\Desktop\yara.jsonNote also that nosotros are exclusively capturing a subset of the "Microsoft-Windows-DotNETRuntime" events (0x2038), specifically: JitKeyword, InteropKeyword, LoaderKeyword as well as NGenKeyword.
Changelog
For details on version specific changes, delight refer to the Changelog.