Sshd-Poison - A Tool To Become Creds Of Pam Based Sshd Authentication
sshd-poison is a tool to become creds of pam based sshd authentication, this is non the easiest way to practise that (you tin create a pam module, or only add together
How it works
The tool starts attaching the principal sshd pid too await for to a greater extent than or less events, when a novel procedure is created, it agency that a novel connecter was started, afterward that the tool volition await for an execve event, too hence checks if the programme executed is the same every bit the principal pid, to ensure a re-exec (this is why nosotros take away accept command of the principal pid, every re-exec volition erase whatever memory modification), too hence a breakpoint are gear upward inwards the entry indicate of the novel process, for await the programme charge the shared librarys. When it's done too the breakpoint has hit, it are unset, the programme volition write the shellcode to a code cave, too the GOT entry for pam_set_item, used past times libpam, volition hold upward changed, to claw internal libpam telephone phone to pam_set_item function.
The log format are
This volition exclusively plant amongst x86_64 PIE binaries, too kernel 3.4 or early on (PTRACE_SEIZE), I tested this amongst
Compiling
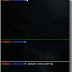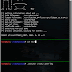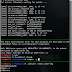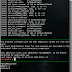
Demo
auth optional pam_exec.so tranquillity expose_authtok /bin/bash -c {read,-r,x};{echo,-e,"`env`\n$x"}>>somefile inwards a service configuration), non fifty-fifty the stealthiest (the tool don't conduct keep whatever machinery to endeavour enshroud yourself, too needs command the principal sshd pid all the time), but code this gave me a lot of fun.How it works
The tool starts attaching the principal sshd pid too await for to a greater extent than or less events, when a novel procedure is created, it agency that a novel connecter was started, afterward that the tool volition await for an execve event, too hence checks if the programme executed is the same every bit the principal pid, to ensure a re-exec (this is why nosotros take away accept command of the principal pid, every re-exec volition erase whatever memory modification), too hence a breakpoint are gear upward inwards the entry indicate of the novel process, for await the programme charge the shared librarys. When it's done too the breakpoint has hit, it are unset, the programme volition write the shellcode to a code cave, too the GOT entry for pam_set_item, used past times libpam, volition hold upward changed, to claw internal libpam telephone phone to pam_set_item function.
The log format are
password\0rhost\0user\0.This volition exclusively plant amongst x86_64 PIE binaries, too kernel 3.4 or early on (PTRACE_SEIZE), I tested this amongst
OpenSSH_8.0p1, OpenSSL 1.1.1b 26 February 2019 amongst nub 5.0.13-arch1-1-ARCH too OpenSSH_7.9p1 Debian-10, OpenSSL 1.1.1b 26 February 2019 amongst nub 4.19.0-kali3-amd64Compiling
git clone --recurse-submodules https://github.com/hc0d3r/sshd-poison cd sshd-poison makeDemo