Home
Unlabelled
Using hashcat to recover your passwords
Using hashcat to recover your passwords
Many people may have a user account on their system which they may not know the password to log in. Other passwords may also exist which can be recovered.
This article will cover the use of Hashcat to find missing passwords. Of course, this process will not find every password, but it can help to attempt a recovery.
Installation
The first step to use Hashcat is to get the program.
To get the files needed you need to open a Terminal and type the following commands:
cd ~
wget https://hashcat.net/files_legacy/hashcat-2.00.7z
NOTE: Hashcat 3.50 is available, but the CPU and GPU requirements are quite limiting for use. Version 2.00 works on most systems.
The commands will place you in your HOME folder and then download the compressed file containing Hashcat.
To extract the downloaded file you need ‘7Zip’ the program for extracting the ‘7z’ file. Then you need to extract the file. Perform the following for your Linux type:
Debian
sudo apt-get install p7zip
p7zip -d hashcat-2.00.7z
cd hashcat-2.00
Red Hat
sudo yum install p7zip
7za x hashcat-2.00.7z
cd hashcat-2.00
Next, the commands will be the same for Debian and Red Hat systems.
There are two files you need to be aware of in this folder. If you have a 64-bit system then you will need the file ‘hashcat64-cli.bin’. If your system is a 32-bit system then you need to use the file ‘hashcat-cli32.bin’.
Once you know which file you need you can copy it to the folder ‘/usr/bin’ with the appropriate following command:
sudo cp hashcat-cli64.bin /usrbin/hashcat.bin
sudo cp hashcat-cli32.bin /usrbin/hashcat.bin
To test that the file will work type the name of your specific file followed by ‘-help’. For example, for either a 32 or a 64-bit system type the command ‘sudo hashcat.bin -help’.
You should be given a long list of help information for the hashcat program.
Getting Things Ready
Perform the following commands to prepare hashcat:
cd ~/hashcat-2.00/
mkdir passwords
cd passwords
wget https://downloads.skullsecurity.org/passwords/500-worst-passwords.txt.bz2
wget https://downloads.skullsecurity.org/passwords/john.txt.bz2
wget https://downloads.skullsecurity.org/passwords/english.txt.bz2
bzip2 -d 500-worst-passwords.txt.bz2
bzip2 -d john.txt.bz2
bzip2 -d english.txt.bz2
The use of the ‘bzip2’ command will extract the specified file and the ‘-d’ parameter will decompress the compressed file. The original compressed file will be deleted once it has been extracted.
Getting Things Ready to Recover an Account
If we are looking to recover a password for a Linux account then we should create one.
To add a User Account I will name mine ‘tester’, perform the following commands:
sudo useradd tester
sudo passwd tester
After typing the last command you will be prompted to enter and re-enter the password for the User ‘tester’.
Next, we need to know what encryption method is used by your Linux System. I ran the following command on both a Ubuntu 14.04 and CentOS 7.0 system and received the result of SHA512:
grep -rn ENCRYPT_METHOD /etc/login.defs
Before we can get the SALT for the User ‘tester’ you need to log in as ‘tester’ and then log back in as you. You can get the SALT for the user ‘tester’ by typing one of the following commands:
sudo tail -n 1 /etc/shadow
sudo grep -rn tester /etc/shadow
Since the User ‘tester’ was the last User Account created then it will be the last line in the file. The output is shown in Figure 1.
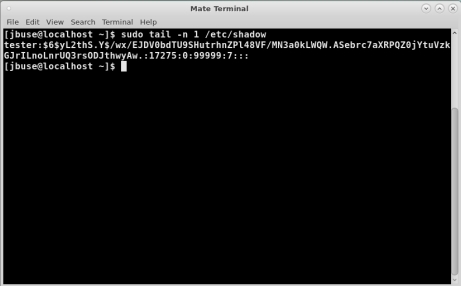
FIGURE 1
We need to create a hash file for the User ‘tester’. To create the hash file perform the following command:
sudo tail -n 1 /etc/shadow >> password.hash
You will need to edit the file and remove the Users name (tester) and all colons and periods at the end of the line as shown in Figure 2.
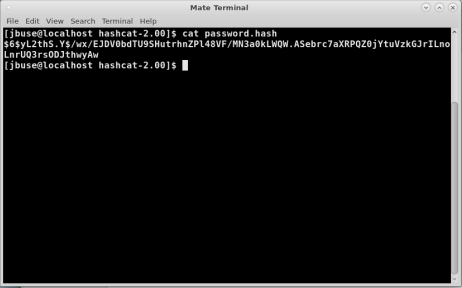
FIGURE 2
Now, about the SALT. SALT is random data that is included with a password to produce the hash.
In Figure 1, the SALT is between the two dollar signs ($) and is ‘yL2thS.Y’.
We can also combine the three password files into one file to make things easier. To do this
enter the following command:
cat 500-worst-passwords.txt john.txt english.txt >> passwords.txt
You should now have a file named ‘passwords.txt’ which contains all of the passwords from the three original files.
We are now ready to look at Hashcat and hopefully find the password for ‘tester’.
Hashcat Syntax
First we must understand the Hashcat syntax to find our password.
The basic syntax is:
hashcat [options] hashfile [mask|wordfiles|dictionaries]
The two primary options we will use are as follows:
-m, --hash-type=NUM
-a, --attack-mode=NUM
The ‘hashtype’ is based off of the following values:
sha1 =100
sha-256 = 1400
sha-512 = 1700
sha-512 (unix) = 1800
To get a more extensive list use the command ‘hashcat64.bin –help’ and look for the section on ‘Hash Modes’.
The ‘Attack Mode’ option has the following values:
0 – Straight
1 – Combination
3 – Brute Force
6 – Hybrid (wordlist + mask)
7 – Hybrid Mask (mask + wordlist)
So the command we will use is as follows:
sudo hashcat.bin -m 1800 -a 0 password.hash passwords/passwords.txt
NOTE: The command is being run from the folder ‘hashcat-2.00’ where the ‘password.hash’ file is located.
The command, as shown in Figure 3, took 2 milliseconds and found that password to be ‘starwars’. The process did not take long since the password was in the ‘passwords.txt’. What if I change the password to one which is not in the list?
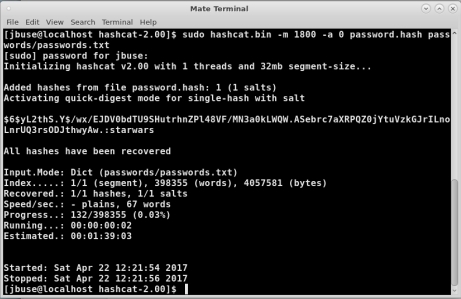
FIGURE 3
If you want to find a larger text file of words, try ‘http://dazzlepod.com/site_media/txt/passwords.txt’ which contains over 2,000,000 entries. Depending on the system it will take over an hour to get through the list. The time goes faster if the password is found in the list toward the beginning of the file.
Keep in mind that all your lists can be concatenated together as we did before to make one large list. The command is as follows:
cat file1 file2 file3 >> newfile
Just enter as many filenames as you need and give the new larger file a new name (newfile). The larger your dictionary the more chances you have of finding a password.
I changed the password for ‘tester’ and created a new hash file. I am using the new passwords file from dazzlepod.com.
What if a password is not found in the dictionary?
Hashcat Mask
We can provide a mask to use as a model for trying various passwords at random. The Brute Force Attack can be quite lengthy to determine a password which is completely unknown.
The Mask you provide is based off of known or unknown characters. The characters are symbolized by the following:
?l – lower-case alphabetic character
?u – upper-case alphabetic character
?d – numeric digit (0-9)
?s – symbol character (!@#$%^&*,. etc.)
?a – any of the above
If you know the password is all lower-case alphabetic characters and is five characters long the the mask would be ‘?l?l?l?l?l’.
Any way you can limit the mask to characters other than all (?a) will greatly reduce the time needed to find the password.
If we have no clue as to the characters or even the length, we would have to use a mask of all ‘?a’ and assume there is a specific number, or less, of characters in the password. For instance, we can assume there will be ten or less characters in the password so the mask would be ‘?a?a?a?a?a?a?a?a?a?a’.
The command given would be similar to that used before, but the dictionary list would be replaced with the mask:
hashcat -m 1800 -a 3 password.hash ?a?a?a?a?a?a?a?a?a?a’
Have fun with cracking passwords. Hope this helps find lost passwords.
This article will cover the use of Hashcat to find missing passwords. Of course, this process will not find every password, but it can help to attempt a recovery.
Installation
The first step to use Hashcat is to get the program.
To get the files needed you need to open a Terminal and type the following commands:
cd ~
wget https://hashcat.net/files_legacy/hashcat-2.00.7z
NOTE: Hashcat 3.50 is available, but the CPU and GPU requirements are quite limiting for use. Version 2.00 works on most systems.
The commands will place you in your HOME folder and then download the compressed file containing Hashcat.
To extract the downloaded file you need ‘7Zip’ the program for extracting the ‘7z’ file. Then you need to extract the file. Perform the following for your Linux type:
Debian
sudo apt-get install p7zip
p7zip -d hashcat-2.00.7z
cd hashcat-2.00
Red Hat
sudo yum install p7zip
7za x hashcat-2.00.7z
cd hashcat-2.00
Next, the commands will be the same for Debian and Red Hat systems.
There are two files you need to be aware of in this folder. If you have a 64-bit system then you will need the file ‘hashcat64-cli.bin’. If your system is a 32-bit system then you need to use the file ‘hashcat-cli32.bin’.
Once you know which file you need you can copy it to the folder ‘/usr/bin’ with the appropriate following command:
sudo cp hashcat-cli64.bin /usrbin/hashcat.bin
sudo cp hashcat-cli32.bin /usrbin/hashcat.bin
To test that the file will work type the name of your specific file followed by ‘-help’. For example, for either a 32 or a 64-bit system type the command ‘sudo hashcat.bin -help’.
You should be given a long list of help information for the hashcat program.
Getting Things Ready
Perform the following commands to prepare hashcat:
cd ~/hashcat-2.00/
mkdir passwords
cd passwords
wget https://downloads.skullsecurity.org/passwords/500-worst-passwords.txt.bz2
wget https://downloads.skullsecurity.org/passwords/john.txt.bz2
wget https://downloads.skullsecurity.org/passwords/english.txt.bz2
bzip2 -d 500-worst-passwords.txt.bz2
bzip2 -d john.txt.bz2
bzip2 -d english.txt.bz2
The use of the ‘bzip2’ command will extract the specified file and the ‘-d’ parameter will decompress the compressed file. The original compressed file will be deleted once it has been extracted.
Getting Things Ready to Recover an Account
If we are looking to recover a password for a Linux account then we should create one.
To add a User Account I will name mine ‘tester’, perform the following commands:
sudo useradd tester
sudo passwd tester
After typing the last command you will be prompted to enter and re-enter the password for the User ‘tester’.
Next, we need to know what encryption method is used by your Linux System. I ran the following command on both a Ubuntu 14.04 and CentOS 7.0 system and received the result of SHA512:
grep -rn ENCRYPT_METHOD /etc/login.defs
Before we can get the SALT for the User ‘tester’ you need to log in as ‘tester’ and then log back in as you. You can get the SALT for the user ‘tester’ by typing one of the following commands:
sudo tail -n 1 /etc/shadow
sudo grep -rn tester /etc/shadow
Since the User ‘tester’ was the last User Account created then it will be the last line in the file. The output is shown in Figure 1.
FIGURE 1
We need to create a hash file for the User ‘tester’. To create the hash file perform the following command:
sudo tail -n 1 /etc/shadow >> password.hash
You will need to edit the file and remove the Users name (tester) and all colons and periods at the end of the line as shown in Figure 2.
FIGURE 2
Now, about the SALT. SALT is random data that is included with a password to produce the hash.
In Figure 1, the SALT is between the two dollar signs ($) and is ‘yL2thS.Y’.
We can also combine the three password files into one file to make things easier. To do this
enter the following command:
cat 500-worst-passwords.txt john.txt english.txt >> passwords.txt
You should now have a file named ‘passwords.txt’ which contains all of the passwords from the three original files.
We are now ready to look at Hashcat and hopefully find the password for ‘tester’.
Hashcat Syntax
First we must understand the Hashcat syntax to find our password.
The basic syntax is:
hashcat [options] hashfile [mask|wordfiles|dictionaries]
The two primary options we will use are as follows:
-m, --hash-type=NUM
-a, --attack-mode=NUM
The ‘hashtype’ is based off of the following values:
sha1 =100
sha-256 = 1400
sha-512 = 1700
sha-512 (unix) = 1800
To get a more extensive list use the command ‘hashcat64.bin –help’ and look for the section on ‘Hash Modes’.
The ‘Attack Mode’ option has the following values:
0 – Straight
1 – Combination
3 – Brute Force
6 – Hybrid (wordlist + mask)
7 – Hybrid Mask (mask + wordlist)
So the command we will use is as follows:
sudo hashcat.bin -m 1800 -a 0 password.hash passwords/passwords.txt
NOTE: The command is being run from the folder ‘hashcat-2.00’ where the ‘password.hash’ file is located.
The command, as shown in Figure 3, took 2 milliseconds and found that password to be ‘starwars’. The process did not take long since the password was in the ‘passwords.txt’. What if I change the password to one which is not in the list?
FIGURE 3
If you want to find a larger text file of words, try ‘http://dazzlepod.com/site_media/txt/passwords.txt’ which contains over 2,000,000 entries. Depending on the system it will take over an hour to get through the list. The time goes faster if the password is found in the list toward the beginning of the file.
Keep in mind that all your lists can be concatenated together as we did before to make one large list. The command is as follows:
cat file1 file2 file3 >> newfile
Just enter as many filenames as you need and give the new larger file a new name (newfile). The larger your dictionary the more chances you have of finding a password.
I changed the password for ‘tester’ and created a new hash file. I am using the new passwords file from dazzlepod.com.
What if a password is not found in the dictionary?
Hashcat Mask
We can provide a mask to use as a model for trying various passwords at random. The Brute Force Attack can be quite lengthy to determine a password which is completely unknown.
The Mask you provide is based off of known or unknown characters. The characters are symbolized by the following:
?l – lower-case alphabetic character
?u – upper-case alphabetic character
?d – numeric digit (0-9)
?s – symbol character (!@#$%^&*,. etc.)
?a – any of the above
If you know the password is all lower-case alphabetic characters and is five characters long the the mask would be ‘?l?l?l?l?l’.
Any way you can limit the mask to characters other than all (?a) will greatly reduce the time needed to find the password.
If we have no clue as to the characters or even the length, we would have to use a mask of all ‘?a’ and assume there is a specific number, or less, of characters in the password. For instance, we can assume there will be ten or less characters in the password so the mask would be ‘?a?a?a?a?a?a?a?a?a?a’.
The command given would be similar to that used before, but the dictionary list would be replaced with the mask:
hashcat -m 1800 -a 3 password.hash ?a?a?a?a?a?a?a?a?a?a’
Have fun with cracking passwords. Hope this helps find lost passwords.
Using hashcat to recover your passwords
![Using hashcat to recover your passwords]() Reviewed by 0x000216
on
Thursday, September 12, 2019
Rating: 5
Reviewed by 0x000216
on
Thursday, September 12, 2019
Rating: 5