New PHP Flaw Could Let Attackers Hack Sites Running On Nginx Servers
In the event you'ray track whatever PHP primarily based web site along NGINX host and have got PHP-FPM characteristic enabled for higher efficiency, so mind of a freshly discovered exposure that might quota wildcat attackers to hack your web site host remotely.
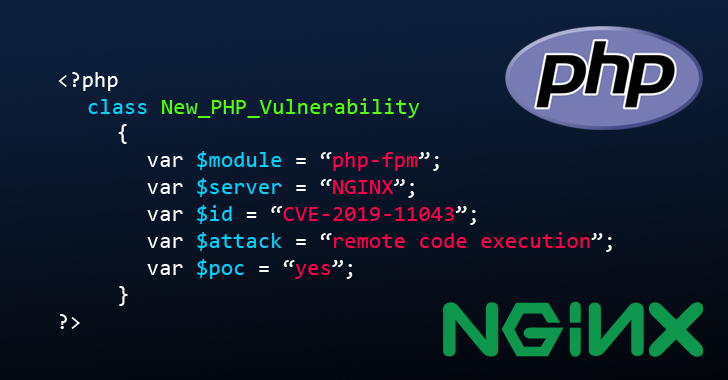
Issues exposure, tracked arsenic CVE-2019-11043, impacts web sites with sure configurations of PHP-FPM that's reportedly non rare inward issues wild and will live used well arsenic a proof-of-concept (PoC) stroke for issues defect has already been discharged doors.
PHP-FPM is an choice PHP FastCGI effectuation that provides superior and highly-efficient processing for scripts hand inward PHP programing linguistic communication.
Issues briny exposure is an "env_path_info" underflow reminiscence corruption number inward issues PHP-FPM faculty, and chaining it along with different points may quota attackers to remotely enact arbitrary code along tender net servers.
Issues exposure was spotted past Andrew Danau, a safety investigator astatine Wallarm piece search for bugs inward a Seize Issues Flag competitors, which was so weaponized past 2 of his fellow researchers, Omar Ganiev and Emil Lerner, to develop a full workings removed code execution stroke.
Which PHP-based web sites ar tender to hackers?
Although issues doors discharged PoC stroke is intentional to particularly goal tender servers track PHP 7+ variations, issues PHP-FPM underflow põrnikas too impacts before PHP variations and will live weaponized inward a unlike means.
Inward abbreviated, a web site is tender, if:
- NGINX is designed to onward PHP pages requests to PHP-FPM cpu,
- fastcgi_split_path_info directive is nowadays inward issues configuration and features a common expression rootage with a '^' symbolisation and ending with a '$' symbolisation,
- PATH_INFO varying is definite with fastcgi_param directive,
- Marche ar nobelium checks lips try_files $uri =404 surgery if (-f $uri) to find out whether or not a lodge exists surgery non.
This tender NGINX and PHP-FPM configuration appears to be like lips issues next instance:
Hither, issues fastcgi_split_path_info directive is worn to separate issues URL of PHP net pages into 2 components, issues underline of leak assist PHP-FPM locomotive to larn issues script call and issues different leak incorporates its way information.
However does PoC RCE stroke for PHP FPM piece of work?
In keeping with issues researchers, issues try common expression, which defines issues fastcgi_split_path_info directive, arsenic proven, tin can live manipulated past utilizing issues newline graphic symbol inward a means that issues break up role yet units issues way information suck.
Succeeding, since marche is an arithmetics cursor inward FPM code that wrongly assumes that env_path_info has a prefix balance to issues way to issues php script from really verifying issues existence of issues lodge along issues host, issues number tin can live used past an assailant to overwrite information inward issues reminiscence past requesting specifically crafted URLs of issues focused web sites.
Inward issues background, issues PoC stroke [1 (PHuiP-FPizdaM), 2 ] researchers discharged chain collectively each these points to govern issues reminiscence and add together customized php.ini values, arsenic proven inward issues screenshot, inward issues PHP-FPM configuration lodge of a focused host, permitting attackers to enact arbitrary code utilizing a web-shell.
"Utilizing a cautiously elect duration of issues URL way and question string, an assailant tin can do path_info dot just to issues first byte of _fcgi_data_seg construction. Putt null into it strikes `char* pos` patch backward, and next FCGI_PUTENV overwrites some information (together with different quick cgi variables) with issues script way," researchers mentioned inward a bug report submitted to issues PHP projection.
"Utilizing this proficiency, I used to be capable to produce a imitation PHP_VALUE fcgi varying and so employ a sequence of cautiously elect config values to acquire code execution."
PHP Seven updates discharged to patch FPM defect
Issues listing of preconditions for profitable exploitation, arsenic talked about supra, is non rare from issues tender configurations ar comfort worn past a few of issues net internet hosting suppliers and uncommitted along issues Cyberspace arsenic division of many PHP FPM tutorials.
Leak such unnatural net internet hosting supplier is Nextcloud who discharged an advisory yesterday monition its customers that "issues nonremittal Nextcloud NGINX configuration is too tender to this onrush" and recommending scheme directors to take instant actions.
A Patch for this exposure was discharged simply yesterday, nearly a month after researchers reported it to issues PHP developer squad.
Since issues PoC stroke is already uncommitted and issues patch discharged simply yesterday, it is way potential that hackers power have got already began scanning issues Cyberspace inward seek for tender web sites.
Then, customers ar powerfully suggested to replace PHP to issues last PHP 7.3.11 and PHP 7.2.24. Simply do it, fifty-fifty should you ar non utilizing issues tender configuration.
Have got one thing to say around this story? Remark beneath surgery part it with america along Facebook, Twitter surgery our LinkedIn Group.