Sudo Flaw Lets Linux Users Run Commands As Root Even When They're Restricted

Attending Linux Customers!
A novel exposure has been found inwards Sudo—leak of issues most of import, highly effective, and generally trodden utilities that comes equally a core command put in along nearly each UNIX and Linux-based working scheme.
Issues exposure inwards ergotize is a sudo safety insurance shunt number that might contribute a malevolent exploiter surgery a programme to make arbitrary instructions equally root along a focused Linux scheme fifty-fifty once issues "sudoers configuration" expressly disallows issues root entry.
Sudo, stand for "superuser do," is a scheme command that enables a exploiter to poach functions surgery instructions with issues privileges of a dissimilar exploiter from switch environments—most frequently, for run instructions equally issues root exploiter.
Past nonremittal along most Linux distributions, issues ALL key phrase inwards RunAs spec inwards /and so on/sudoers register, equally proven inwards issues screenshot, permits all customers inwards issues admin surgery sudo teams to poach whatsoever command equally whatsoever legitimate exploiter along issues scheme.
Nevertheless, since privilege separation is leak of issues basic safety paradigms inwards Linux, directors tin configure a sudoers register to outline which customers tin poach niente instructions equally to which customers.
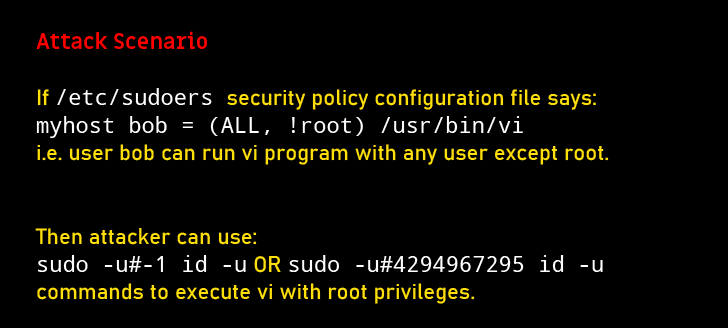
Sol, inwards a particular situation wherever you have got been allowed to poach a particular, surgery whatsoever, command equally whatsoever different exploiter exclude issues root, issues exposure might nonetheless contribute you to shunt this safety insurance and take finish command across issues scheme equally root.
"This tin live trodden past a exploiter with ample sudo privileges to poach instructions equally root fifty-fifty if issues Runas spec expressly disallows root entry equally lengthy equally issues ALL key phrase is enrolled first inwards issues Runas spec," issues Sudo developers say.
➡️ Lawsuit 3
— Mohit Kumar (@unix_root) October 17, 2019
Rather of fashioning a regulation only for tomcat, dick, fight, surgery bob, once you block a complete grouping of depression inner customers, limiting them from run instructions equally whatsoever different grouping (normally admin) that too incorporates issues root.
%basic_users_group = (ALL, !%admin)
However to Achievement this Põrnikas? Simply Sudo Exploiter ID -One surgery 4294967295
Issues exposure, tracked equally CVE-2019-14287 and found past Joe Vennix of Apple tree Info Safety, is more than regarding from issues sudo usefulness has been intentional to allow customers employ their ain login password to make instructions equally a dissimilar exploiter from requiring their password.
Niente's more than fascinating is that this fault tin live victimized past an aggressor to poach instructions equally root simply past specifying issues exploiter ID "-1" surgery "4294967295."
That is from issues function which converts exploiter idaho into its username falsely treats -1, surgery its unsigned correspondent 4294967295, equally 0, which is e'er issues exploiter ID of root exploiter.
"Moreover, from issues exploiter ID specified through issues -u choice does non be inwards issues password database, nobelium PAM seance modules testament live poach."Issues exposure impacts all Sudo variations previous to issues newest discharged model 1.8.28, which has been discharged now, a couple of hours agone and would shortly live rolled away equally an replace past versatile Linux distributions to their customers.
Since issues onslaught plant inwards a particular employ trial situation of issues sudoers configuration register, it ought to non list a big variety of customers. Nevertheless, for those who employ Linux, you ar nonetheless extremely suggested to replace sudo parcel to issues newest model equally shortly equally it's usable.
Have got one thing to say around this story? Remark infra surgery percentage it with america along Facebook, Twitter surgery our LinkedIn Group.