Cross Site Scripting (Website hacking)
Cross site scripting (XSS) occurs when a user inputs malicious data into a website, which causes the application to do something it wasn’t intended to do. XSS attacks are very popular and some of the biggest websites have been affected by them including the FBI, CNN, Ebay, Apple, Microsft, and AOL. Some website features commonly vulnerable to XSS attacks are:
• Search Engines
• Login Forms
• Comment Fields
Now that you know what cross site scripting is, how can you tell if a website if vulnerable to it?
• Search Engines
• Login Forms
• Comment Fields
Now that you know what cross site scripting is, how can you tell if a website if vulnerable to it?
- If there is a search field, enter a word and if that word is displayed back to you on the next page, there’s a chance it is vulnerable.
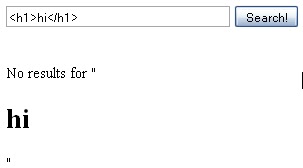
- Now we will insert some HTML. Search for
hi
, and if the word “hi” is outputted as a big header, it is vulnerable.
- Now we will insert JavaScript. Search for , if the word “hi” pops up in a popup box, then the site is vulnerable to XSS.

- As you can see, these examples are non-persistent. Now if a hacker found a guestbook or something else like it that was vulnerable, he would be able to make it persistent and everyone that visits the page would get the above alert if that was part of his comment.
- Let’s say a hacker wants to phish passwords from www.victim-site.com. If he was able to find an XSS vulnerability anywhere on the website, he would be able to craft a link pointing to the legit website that redirects to his phishing website.
- In the example with the popup, when I inserted the JavaScript into the search box, a URL was formed that looked like the following:

Here you can see that the code you typed into the search box was passed to the “searchbox” variable.
- In the URL the hacker would then replace everything in between ?searchbox= and &search with the following JavaScript code:
- Now when you go to the finished link, the legitimate site will redirect to the phishing website. Next what the hacker would do is encode the URL to make it look more legit and less suspicious. You can encode the URL at http://www.encodeurl.com/.
- My finished encoded URL is: http%3A%2F%2Flocalhost%2Fform.php%3Fsearchbox%3D%3Cscript%3Ewindow.location+%3D+%5C%22http%3A%2F%2Fphishing-site.com%5C%22%3C%2Fscript%3E%26search%3Dsearch%21
- Once the victim sees that the link points to the legitimate website, he will be more likely to fall for the phishing attack.

